E mail internet hosting supplier Cock.li has confirmed it suffered a data breach after risk actors exploited flaws in its now-retired Roundcube webmail platform to steal over 1,000,000 consumer data.
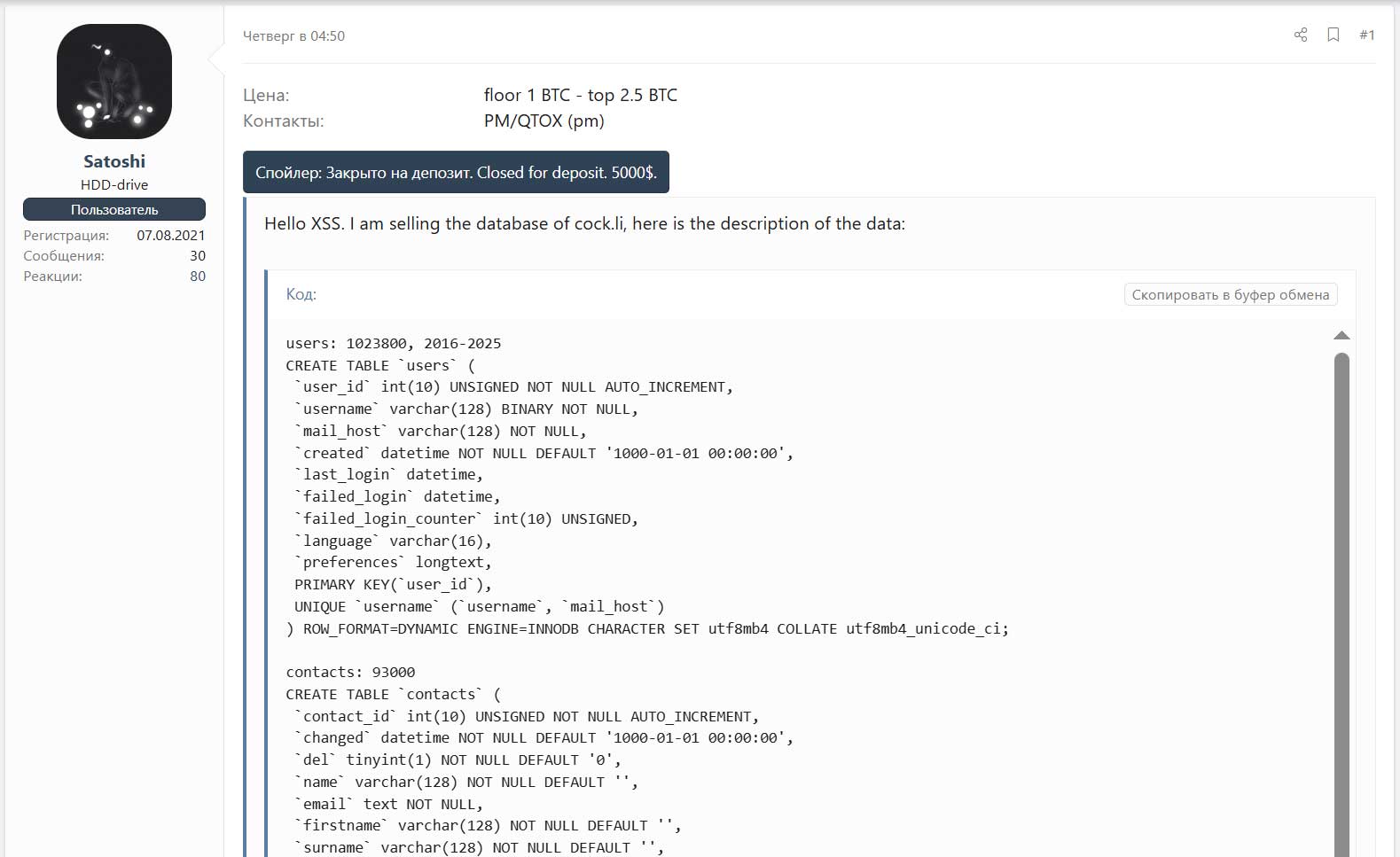
The incident uncovered all customers who had logged in to the mail service since 2016, estimated at 1,023,800 folks, together with contact entries for a further 93,000 customers.
Cock.li is a Germany-based free e mail internet hosting supplier with a privacy-focused ethos and lax moderation insurance policies, run by a single operator often known as ‘Vincent Canfield’ since 2013.
It’s promoted as a substitute for mainstream e mail suppliers, supporting customary security protocols like SMTP, IMAP, and TLS.
Cock.li is utilized by individuals who mistrust main suppliers and members of infosec and open-source communities. It’s also fashionable amongst cybercriminals, resembling associates from Dharma, Phobos, and different ransomware gangs.
Late final week, the Cock.li service was disrupted with out public rationalization, leaving customers questioning what may need occurred.
Quickly after, a risk actor claimed to be promoting two databases containing dumped from Cock.li that contained delicate consumer data, providing them on the market for at least one Bitcoin ($92.5k).
Supply: BleepingComputer
Cock.li printed a press release on its web site yesterday, confirming the breach and the validity of the risk actor’s claims.
The e-mail service confirmed that the next data has been uncovered for 1,023,800 consumer accounts:
- E mail deal with
- First and final login timestamps
- Failed login makes an attempt and rely
- Language
- A serialized blob of Roundcube settings and e mail signature
- Contact names (just for a subset of 10,400 accounts)
- Contact e mail addresses (just for a subset of 10,400 accounts)
- vCards (just for a subset of 10,400 accounts)
- Feedback (just for a subset of 10,400 accounts)
The service’s announcement clarifies that consumer account passwords, e mail content material, and IP addresses weren’t compromised, as these aren’t current within the stolen databases.
In the meantime, the ten,400 account holders who had third-party contact data uncovered might be getting a separate notification.
For everybody who used the service since 2016, it is strongly recommended to reset their account passwords.
The Cock.li data breach could possibly be precious to researchers and legislation enforcement, because the uncovered data can be utilized to study extra concerning the risk actors who use the platform.
Cock. li’s removes Roundcube
Cock.li says they consider the info was stolen utilizing an outdated RoundCube SQL injection vulnerability tracked as CVE-2021-44026.
This breach comes simply as Cock.li not too long ago analyzed an RCE flaw in Roundcube, CVE-2025-49113, which is believed to be actively exploited in assaults. Their evaluation led them to take away the software program from their platform in June 2025.
“Cock.li will not offer Roundcube webmail,” defined the service admins.
“No matter whether or not our model was weak to this, we have discovered sufficient about Roundcube to drag it from the service for good.”
“One other webmail is certainly on the desk, however it isn’t an instantaneous precedence for us.”
The announcement mentions that higher security practices might have prevented this consumer information leak, admitting that “Cock.li mustn’t have been operating Roundcube within the first place.”
For individuals who need to proceed utilizing Cock.li for e mail, they’ll now have to make use of an IMAP or SMTP/POP3 shopper.
Patching used to imply advanced scripts, lengthy hours, and infinite fireplace drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch sooner, scale back overhead, and deal with strategic work — no advanced scripts required.





