Google has assigned a brand new CVE ID (CVE-2023-5129) to a libwebp security vulnerability exploited as a zero-day in assaults and patched two weeks in the past.
The corporate initially disclosed the flaw as a Chrome weak spot, tracked as CVE-2023-4863, somewhat than assigning it to the open-source libwebp library used to encode and decode photographs in WebP format.
This zero-day bug was collectively reported by Apple Safety Engineering and Structure (SEAR) and the Citizen Lab at The College of Toronto’s Munk College on Wednesday, September 6, and glued by Google lower than every week later.
Safety researchers at Citizen Lab have a longtime monitor document of detecting and revealing zero-days which have been abused in focused spyware and adware campaigns, typically linked to state-sponsored risk actors primarily focusing on high-risk people comparable to journalists and opposition politicians.
The choice to tag it as a Chrome bug triggered confusion inside the cybersecurity neighborhood, prompting questions concerning Google’s option to categorize it as a Google Chrome problem somewhat than figuring out it as a flaw in libwebp.
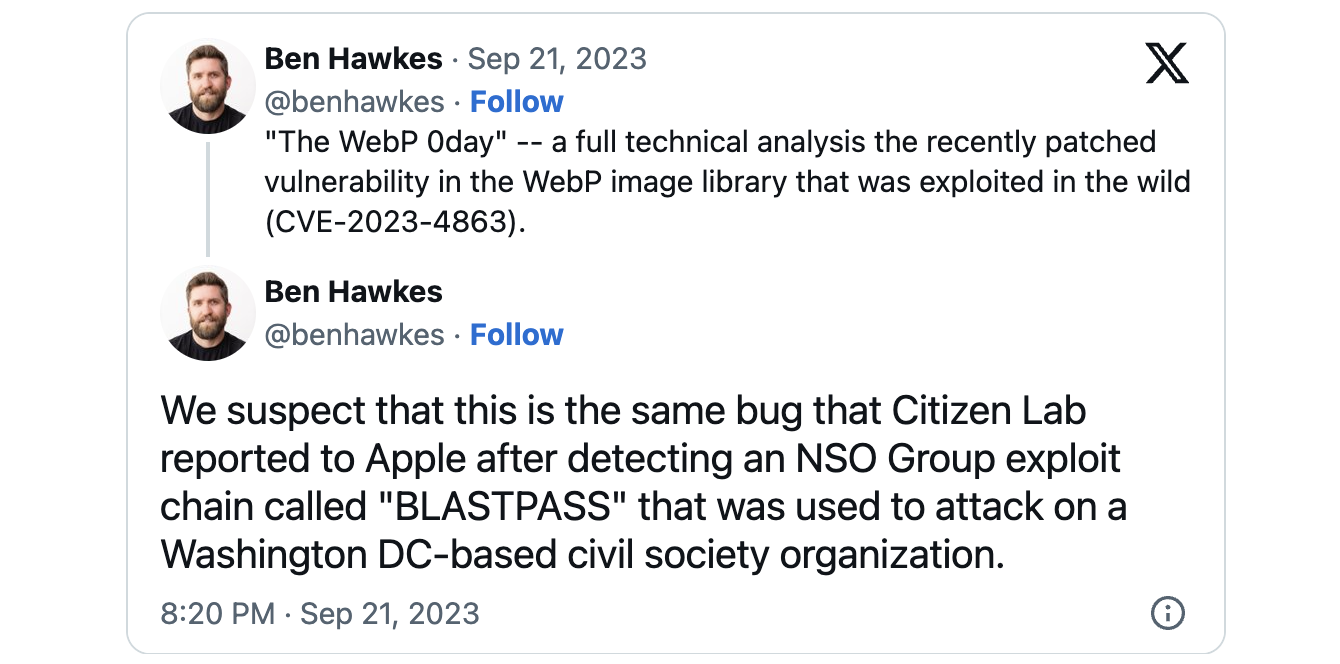
Safety consulting agency founder Ben Hawkes (who beforehand led Google’s Undertaking Zero crew) additionally linked CVE-2023-4863 to the CVE-2023-41064 vulnerability addressed by Apple on September 7 and abused as a part of a zero-click iMessage exploit chain (dubbed BLASTPASS) to contaminate totally patched iPhones with NSO Group’s Pegasus business spyware and adware.
New most severity CVE
Nevertheless, it has now assigned one other CVE ID, CVE-2023-5129, marking it as a important problem in libwebp with a most 10/10 severity ranking. This variation has vital implications for different initiatives utilizing the libwebp open-source library.
Now formally acknowledged as a libwebp flaw, it entails a heap buffer overflow in WebP, impacting Google Chrome variations previous 116.0.5845.187.
This vulnerability resides inside the Huffman coding algorithm utilized by libwebp for lossless compression and it permits attackers to execute out-of-bounds reminiscence writes utilizing maliciously crafted HTML pages.
This kind of exploit can have extreme penalties, from crashes to arbitrary code execution and unauthorized entry to delicate data.
The reclassification of CVE-2023-5129 as a libwebp vulnerability holds explicit significance as a consequence of it initially going unnoticed as a possible security risk for quite a few initiatives utilizing libwebp, together with 1Password, Sign, Safari, Mozilla Firefox, Microsoft Edge, Opera, and the native Android net browsers.
The revised important ranking underscores the significance of promptly addressing the security vulnerability (now tracked underneath a number of CVE IDs with totally different severity scores) throughout these platforms to make sure customers’ knowledge security.
A Google spokesperson was not instantly accessible for remark when contacted by BleepingComputer earlier right now.