As we enter 2024, Gcore has launched its newest Gcore Radar report, a twice-annual publication during which the corporate releases inside analytics to trace DDoS assaults. Gcore’s broad, internationally distributed community of scrubbing facilities permits them to comply with assault developments over time. Learn on to find out about DDoS assault developments for Q3–This autumn of 2023, and what they imply for growing a strong safety technique in 2024.
Gcore’s Key Findings
DDoS assault developments for the second half of 2023 reveal alarming developments within the scale and class of cyberthreats.
Unprecedented Attack Energy
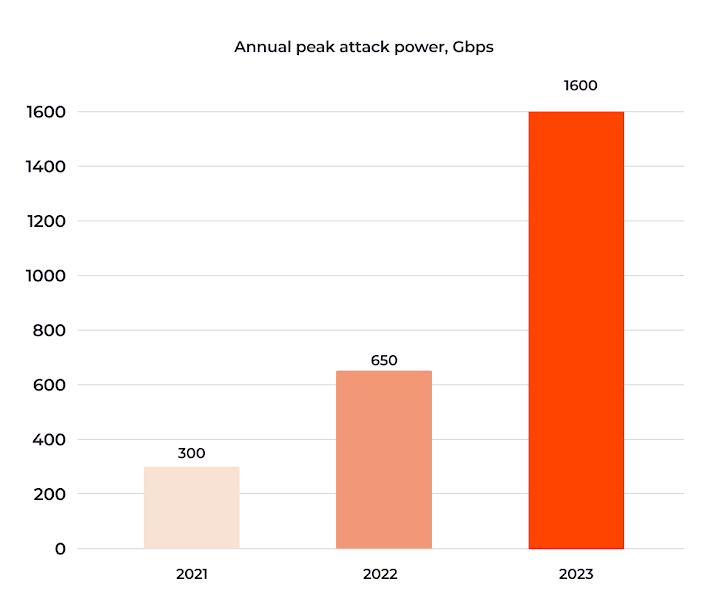
The previous three years have caused a >100% annual improve in DDoS peak (registered most) assault quantity:
- In 2021, the height capability of DDoS assaults was 300 Gbps
- In 2022, it elevated to 650 Gbps
- In Q1–Q2 of 2023, it elevated once more to 800 Gbps
- In Q3–This autumn of 2023, it surged to 1600 Gbps (1.6 Tbps)
Notably, the soar in H2 of 2023 means the cybersecurity trade is measuring DDoS assaults in a brand new unit, Terabits.
 |
| Most assault energy in 2021–2023 in Gbps |
This illustrates a big and ongoing escalation within the potential harm of DDoS assaults, a development Gcore expects to see proceed in 2024.
Attack Period
Gcore noticed assault lengths various from three minutes to 9 hours, with a mean of about an hour. Normally, brief assaults are tougher to detect as they do not for correct visitors evaluation as a result of knowledge shortage, and since they’re tougher to acknowledge, they’re additionally tougher to mitigate. Longer assaults require extra sources to struggle, requiring a strong mitigation response; in any other case, the chance is extended server unavailability.
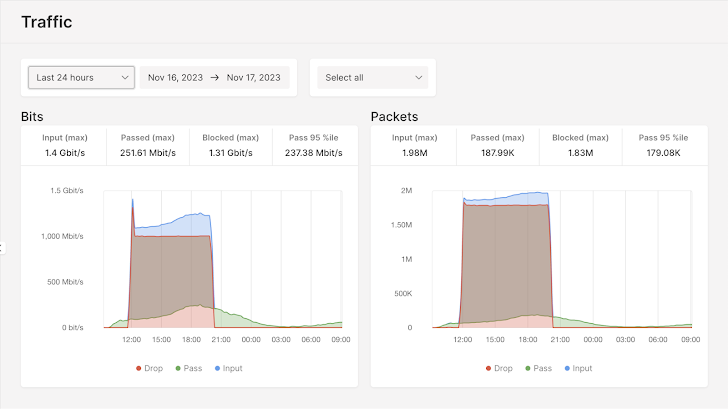 |
| Gcore’s longest registered assault lasted 9 hours |
Predominant Attack Sorts
UDP floods proceed to dominate, constituting 62% of DDoS assaults. TCP floods and ICMP assaults additionally stay well-liked at 16% and 12% of the whole, respectively.
All different DDoS assault sorts, together with SYN, SYN+ACK flood, and RST Flood, accounted for a mere 10% mixed. Whereas some attackers might use these extra subtle approaches, the bulk are nonetheless targeted on delivering sheer packet quantity to take down servers.
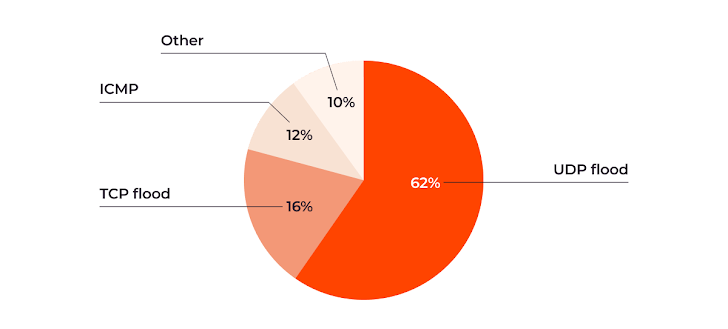 |
| Dominant assault sorts in H2 of 2023 |
The variation in assault strategies necessitates a multifaceted protection technique that may defend towards a spread of DDoS strategies.
World Attack Sources
This international unfold of assault sources demonstrates the borderless nature of cyber threats, the place attackers function throughout nationwide boundaries. Gcore recognized numerous assault origins within the latter half of 2023, with the US main at 24%. Indonesia (17%), the Netherlands (12%), Thailand (10%), Colombia (8%), Russia (8%), Ukraine (5%), Mexico (3%), Germany (2%,) and Brazil (2%) make up the highest ten, illustrating a widespread international risk.
 |
| Geographical assault supply unfold |
The geographic distribution of DDoS assault sources gives necessary data for creating focused protection methods and for shaping worldwide policy-making geared toward combating cybercrime. Nevertheless, figuring out the situation of the attacker is difficult as a result of using strategies like IP spoofing and the involvement of distributed botnets. This makes it troublesome to evaluate motivations and capabilities, which might fluctuate from state-sponsored actions to particular person hackers.
Focused Industries
Probably the most-targeted industries in H2 of 2023 spotlight the influence of DDoS assaults throughout numerous sectors:
- The gaming trade stays probably the most affected, enduring 46% of the assaults.
- The monetary sector, together with banks and playing companies, got here in second at 22%.
- Telecommunications (18%,) infrastructure-as-a-service (IaaS) suppliers (7%,) and laptop software program corporations (3%) had been additionally considerably focused.
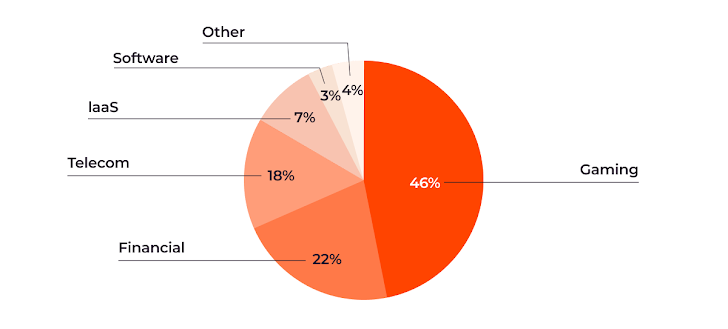 |
| DDoS assaults by affected trade |
Since the earlier Gcore Radar report, attackers have not modified their focus: The gaming and monetary sectors are notably attention-grabbing to attackers, doubtless as a result of their monetary features and person influence. This underscores a necessity for focused cybersecurity methods within the most-hit industries, like countermeasures for particular gaming servers.
Evaluation
The info from the latter half of 2023 highlights a worrying development within the DDoS assault panorama. The rise in assault energy to 1.6 Tbps is especially alarming, signaling a brand new degree of risk for which organizations should put together. For comparability, even a “humble” 300 Gbps assault is able to disabling an unprotected server. Paired with the geographical distribution of assault sources, it is clear that DDoS threats are a critical and international problem, necessitating worldwide cooperation and intelligence sharing to mitigate doubtlessly devastating assaults successfully.
The vary in assault durations means that attackers have gotten extra strategic, tailoring their approaches to particular targets and goals:
- Within the gaming sector, for instance, assaults are comparatively low in energy and length however extra frequent, inflicting repeated disruption to a selected server with the purpose of disrupting the participant expertise to power them to modify to a competitor’s server.
- For the monetary and telecom sectors, the place the financial influence is extra instant, assaults are sometimes greater in quantity with size extremely variable.
The continuing concentrating on of the gaming, monetary sectors, telecommunications, and IaaS industries displays the strategic alternative of attackers to choose companies whose disruption has a big financial and operational influence.
Conclusion
The Gcore Radar report for Q3–This autumn of 2023 serves as a well timed reminder of the ever-evolving nature of cyberthreats. Organizations throughout sectors should spend money on complete and adaptive cybersecurity measures. Staying forward of DDoS threats requires a eager understanding of the altering patterns and techniques of cyber attackers.
Gcore DDoS Safety has a confirmed document of repelling even probably the most highly effective and sustained assaults. Join Gcore DDoS Safety to guard your small business from regardless of the 2024 DDoS panorama brings.




