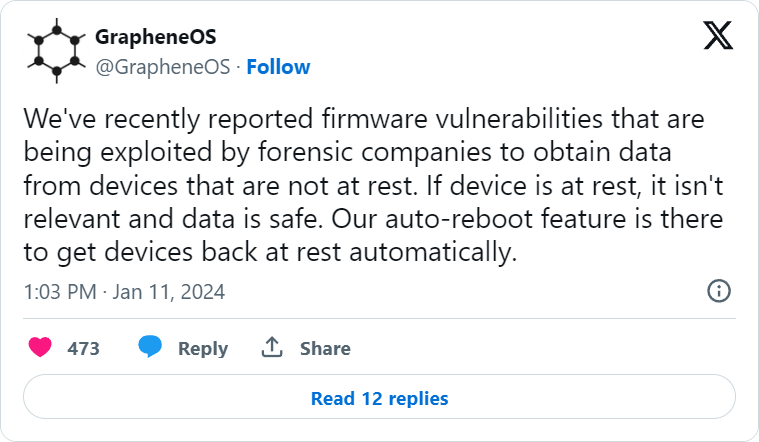
The GrapheneOS workforce behind the privateness and security-focused Android-based working system with the identical title is suggesting that Android ought to introduce an auto-reboot characteristic to make exploitation of firmware flaws harder.
The undertaking revealed that it just lately reported firmware vulnerabilities within the Android working system that affect Google Pixel and Samsung Galaxy telephones, which might be exploited to steal information and spy on customers when the machine just isn’t at relaxation.
When a tool is “at relaxation,” it implies that it’s both turned off or has not been unlocked after booting up. On this state, privateness protections are very excessive and the cellular machine just isn’t absolutely practical as a result of encryption keys are nonetheless not out there for put in apps to make use of.
The primary unlock after a reboot causes a number of cryptographic keys to maneuver to the short entry reminiscence so put in apps to work correctly and the machine switches to a “not at relaxation” state.
The GrapheneOS workforce highlights that locking the display screen after utilizing the machine doesn’t place it again into the “at relaxation” state as a result of some security exemptions persist.
Rebooting the machine terminates all non permanent states, processes, or actions that might be exploited and requires authentication like PIN, password, or biometric verification to unlock, thereby re-engaging all security mechanisms.
Though GrapheneOS devs haven’t shared many particulars concerning the exploited firmware bugs, they proposed a generic mitigation that will work properly usually: an auto-reboot characteristic that’s already current of their working system.
The thought is to attenuate the window of alternative for attackers and disrupt present compromises by resetting all safety programs on the machine extra ceaselessly than a consumer would.
GrapheneOS’ auto-reboot system resets the machine each 72 hours however because the OS maker feedback, that is too lengthy a interval and so they plan to cut back it.
GrapheneOS additionally notes that flight modes on smartphones that folks assume scale back the assault floor typically nonetheless enable information trade through Wi-Fi, Bluetooth, NFC, and USB Ethernet, so relying on the assault vector, it is probably not an efficient safety measure.
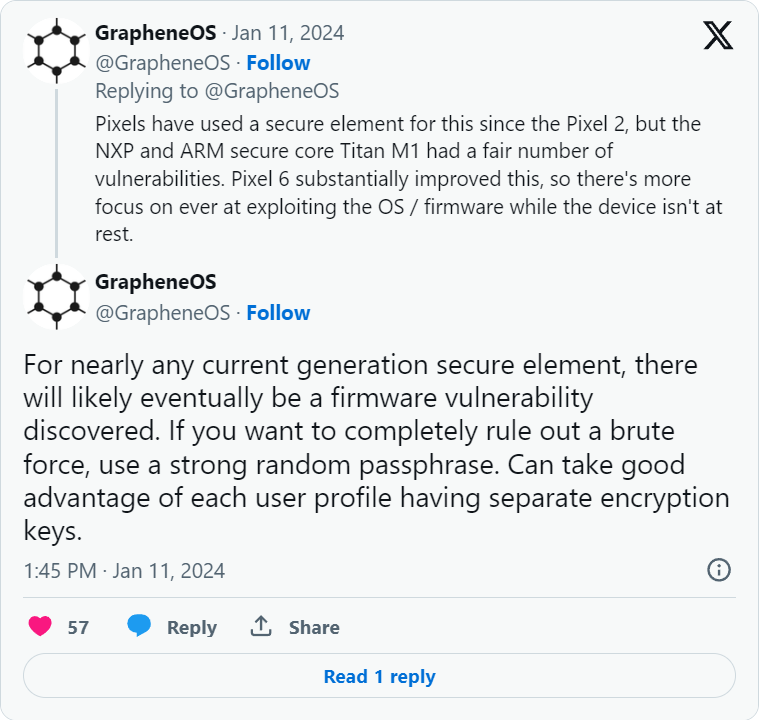
The builders contact on the subject of PIN/password security and its relation to the machine’s encryption and security programs, as these authentication strategies are used as keys to encrypt machine information.
Safe factor throttling is significant for securing quick PINs and passphrases towards stealthy brute forcing that might unlock not simply the display screen but additionally the safe enclave on the machine’s chip.
BleepingComputer has reached out to the GrapheneOS workforce and Google to be taught extra concerning the found vulnerabilities, their affect, and noticed exploitation circumstances. We didn’t obtain a reply from GrapheneOS however Google supplied the following assertion:
“GrapheneOS is a third-party cellular working system based mostly on the Android Open Supply Venture. GrapheneOS reported these points to our Android Vulnerability Reward Program (VRP) on January 2. We’re within the technique of reviewing and figuring out subsequent steps” – Google
Ceaselessly rebooting your Android or iOS machine has been touted as a good suggestion for fixing issues similar to heating, reminiscence, and even name sign but additionally. From a security perspective, this motion can defend from unlawful information restoration or cellular threats that do not need efficient persistence mechanisms.