Malicious actors are utilizing a respectable Rust-based injector known as Freeze[.]rs to deploy a commodity malware known as XWorm in sufferer environments.
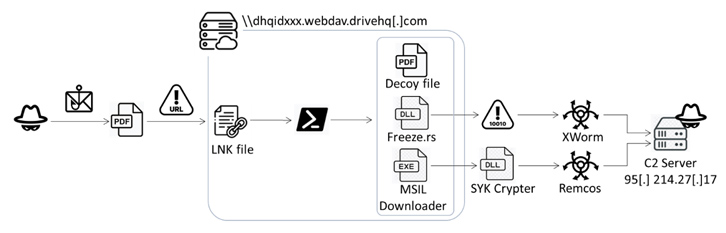
The novel assault chain, detected by Fortinet FortiGuard Labs on July 13, 2023, is initiated through a phishing e-mail containing a booby-trapped PDF file. It has additionally been used to introduce Remcos RAT via a crypter known as SYK Crypter, which was first documented by Morphisec in Could 2022.
“This file redirects to an HTML file and makes use of the ‘search-ms’ protocol to entry an LNK file on a distant server,” security researcher Cara Lin stated. “Upon clicking the LNK file, a PowerShell script executes Freeze[.]rs and SYK Crypter for additional offensive actions.”
Freeze[.]rs, launched on Could 4, 2023, is an open-source pink teaming software from Optiv that capabilities as a payload creation software used for circumventing security options and executing shellcode in a stealthy method.
“Freeze[.]rs makes use of a number of strategies to not solely take away Userland EDR hooks, however to additionally execute shellcode in such a method that it circumvents different endpoint monitoring controls,” based on an outline shared on GitHub.
SYK Crypter, then again, is a software employed to distributed all kinds of malware households corresponding to AsyncRAT, NanoCore RAT, njRAT, QuasarRAT, RedLine Stealer, and Warzone RAT (aka Ave Maria). It is retrieved from the Discord content material supply community (CDN) via a .NET loader connected to emails that masquerades as benign buy orders.
“This assault chain delivers a crypter that’s persistent, options a number of layers of obfuscation, and makes use of polymorphism to keep up its skill to keep away from detection by security options,” Morphisec researcher Hido Cohen defined.
It is value noting that the abuse of the “search-ms” URI protocol handler was not too long ago highlighted by Trellix, which unearthed an infection sequences bearing HTML or PDF attachments to run searches on an attacker-controlled server and checklist malicious information within the Home windows File Explorer as if they’re native search outcomes.
The findings from Fortinet aren’t any completely different in that the information are camouflaged as PDF information however are literally LNK information that execute a PowerShell script to launch the Rust-based injector, whereas displaying a decoy PDF doc.
Within the remaining stage, the injected shellcode is decrypted to execute the XWorm distant entry trojan and harvest delicate knowledge, corresponding to machine data, screenshots, and keystrokes, and remotely management the compromised gadget.
The truth that a three-month-old program is already being weaponized in assaults symbolizes the speedy adoption of offensive instruments by malicious actors to satisfy their targets.
That is not all. The PowerShell script, in addition to loading the injector, is configured to run one other executable, which capabilities as a dropper by contacting a distant server to fetch the SYK Crypter containing the encrypted Remcos RAT malware.
“The mixture of XWorm and Remcos creates a formidable trojan with an array of malicious functionalities,” Lin stated. “The C2 server’s site visitors report […] reveals Europe and North America as the first targets of this malicious marketing campaign.”
The findings come as Trellix disclosed particulars of one other XWorm marketing campaign propagated through social engineering emails with PDF, DOCX and RTF attachments masquerading as invoices and buy orders in assaults geared toward service, transport, and healthcare sectors within the U.S., South Korea, Germany, Austria, and Saudi Arabia.
“The marketing campaign used blogspot.com URLs pointing to scripts and PowerShell code to obtain and execute further payloads in addition to to determine persistence,” researchers Pratik Pachpor and Adarsh S stated. The XWorm payload is “closely obfuscated, including an additional layer of complexity to its evaluation.”




