APIs: Nonetheless Straightforward Targets in 2025
APIs are the spine of contemporary purposes – and one of the crucial uncovered elements of a corporation’s infrastructure. This makes them a primary goal for attackers.
One of many highest-profile examples was the Optus breach in 2022, the place attackers stole hundreds of thousands of buyer data by means of an unauthenticated API endpoint – costing the telecom firm $140 million AUD in fallout.
Worryingly, vulnerabilities like this are really easy to take advantage of you might educate somebody with no technical background to do it in a day. And three years on, Intruder’s security crew continues to be discovering the identical points within the APIs of main organizations – together with members of the S&P 500.
That’s why we constructed Autoswagger – a free, open-source instrument that scans APIs for damaged authorization flaws. Learn on to see the way it works and a few of the most stunning points it uncovered once we put it to the take a look at.
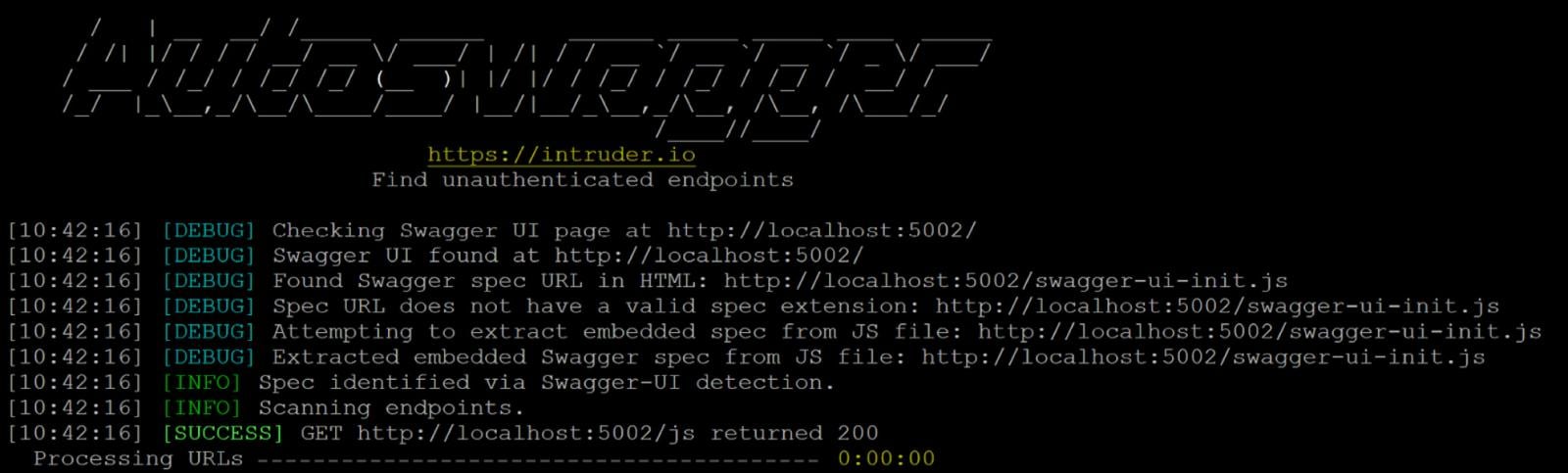
What’s Autoswagger and How Does it Work?
Autoswagger scans domains to detect uncovered API documentation – like OpenAPI or Swagger schemas – then parses them to generate a listing of endpoints to check. It sends requests utilizing legitimate parameters from the documentation and flags any endpoint that returns information with out correct entry management (i.e. no 401 or 403).
If a response consists of delicate information – like credentials or personally identifiable info (PII) – and the endpoint isn’t correctly secured, it will get flagged within the output.
Autoswagger is free to obtain and set up through GitHub.
For extra superior testing, Autoswagger could be run with the –brute flag to aim to bypass validation checks. This helps uncover flaws in endpoints that reject generic enter however settle for particular information codecs or values.
APIs are one of many best methods into programs – and attackers realize it.
1000’s of groups belief Intruder’s always-on publicity administration platform to safe their apps and APIs and repair essential points earlier than attackers discover them. Add your API schema and get peace of thoughts in minutes.
Begin Free Trial
Damaged Authorization in Motion: 4 Actual API Vulnerabilities Discovered by Autoswagger
We put Autoswagger to the take a look at on targets from a number of massive Bug Bounty packages, scanning for susceptible APIs at scale.
Listed below are just a few real-world examples to point out you what damaged authorization seems to be like within the wild.
Microsoft MPN Credentials
One vulnerability we discovered was in an endpoint merely named ‘config’, which uncovered credentials and API keys for Microsoft Accomplice Program information shops. Among the many information uncovered was a sound set of credentials for a Redis database containing the PII of the companions, together with the programs and certifications that they had undertaken.
The susceptible endpoint was buried six layers deep (/1/dashboard/mpn/program/api/config/), making it practically not possible to guess or uncover by means of brute-force – it was solely recognized as a result of the API’s OpenAPI schema was uncovered.
60,000+ Salesforce Data
One other case concerned an API related to a Salesforce occasion at a big tech firm. The API returned buyer data – together with names, contact particulars, and product orders – which may very well be extracted in bulk by incrementing the ‘ByDate’ url parameter to retrieve 1,000 data per request.
SQL Entry on Inside Coaching App
We additionally discovered an inner employees coaching API at a widely known soda firm, operating in Azure Capabilities, that allowed unauthenticated customers to run arbitrary SQL queries towards the database.
Whereas the info was restricted to inner coaching data, it included employees names and e mail addresses – the form of element an attacker might use to craft a convincing phishing marketing campaign.
Azure Capabilities APIs don’t usually expose documentation, however a developer had deployed an extension that did. Whereas this may occasionally have been for one more service to eat, there was no clear purpose for it to be publicly accessible because the app was meant for inner use.
Lively Listing (AD) Enumeration (Octopus Deploy)
Lastly, Autoswagger found CVE-2025-0589, which allowed an unauthenticated attacker to enumerate Lively Listing person info if AD was built-in with the Octopus Deploy server.
Automated Documentation = Attack Floor Danger
Automated API documentation is nice for builders – however simply as helpful for attackers. When an API’s schema is uncovered, it offers them a transparent map of each endpoint to focus on. With out that map, most wouldn’t even hassle – fuzzing endpoints blindly takes much more effort.
Hiding documentation isn’t an alternative choice to correct API vulnerability administration, however publicly exposing docs you don’t want is an pointless threat. A lot of the vulnerabilities we discovered had been in APIs by no means meant to be public – but their documentation was uncovered anyway.
Check out your personal surroundings: in case your inner APIs are documented and uncovered to the web, they is perhaps handing attackers every part they want.
Intruder constantly scans API endpoints to detect a variety of vulnerabilities, together with uncovered documentation.
Examine your APIs as we speak by beginning a free 14-day trial.
In regards to the writer:
Daniel Andrew, Head of Safety Companies, Intruder
Daniel Andrew heads up offensive security at Intruder, the place he leads Intruder’s Non-public Bug Bounty crew. His background is as a CREST-certified penetration tester and .NET software program engineer.
Sponsored and written by Intruder.




