A number of risk actors are weaponizing a design flaw in Foxit PDF Reader to ship quite a lot of malware reminiscent of Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm.
“This exploit triggers security warnings that might deceive unsuspecting customers into executing dangerous instructions,” Examine Level stated in a technical report. “This exploit has been utilized by a number of risk actors, from e-crime to espionage.”
It is value noting that Adobe Acrobat Reader – which is extra prevalent in sandboxes or antivirus options – shouldn’t be prone to this particular exploit, thus contributing to the marketing campaign’s low detection price.
The difficulty stems from the truth that the appliance reveals “OK” because the default chosen choice in a pop-up when customers are requested to belief the doc previous to enabling sure options to keep away from potential security dangers.
As soon as a consumer clicks OK, they’re displayed a second pop-up warning that the file is about to execute extra instructions with the choice “Open” set because the default. The command triggered is then used to obtain and execute a malicious payload hosted on Discord’s content material supply community (CDN).
“If there have been any probability the focused consumer would learn the primary message, the second can be ‘Agreed’ with out studying,” security researcher Antonis Terefos stated.

“That is the case that the Risk Actors are making the most of this flawed logic and customary human conduct, which offers because the default selection essentially the most ‘dangerous’ one.”
Examine Level stated it recognized a PDF doc bearing a army theme that, when opened by way of Foxit PDF Reader, executed a command to fetch a downloader that, in flip, retrieved two executables to gather and add knowledge, together with paperwork, photos, archive information, and databases to a command-and-control (C2) server.
Additional evaluation of the assault chain has revealed that the downloader is also used to drop a 3rd payload that is able to capturing screenshots of the contaminated host, after which they’re uploaded to the C2 server.
The exercise, assessed to be geared in direction of espionage, has been linked to DoNot Group (aka APT-C-35 and Origami Elephant), citing overlaps with beforehand noticed ways and strategies related to the risk actor.
A second occasion weaponizing the identical method employs a multi-stage sequence to deploy a stealer and two cryptocurrency miner modules reminiscent of XMRig and lolMiner. Apparently, a number of the booby-trapped PDF information are distributed by way of Fb.
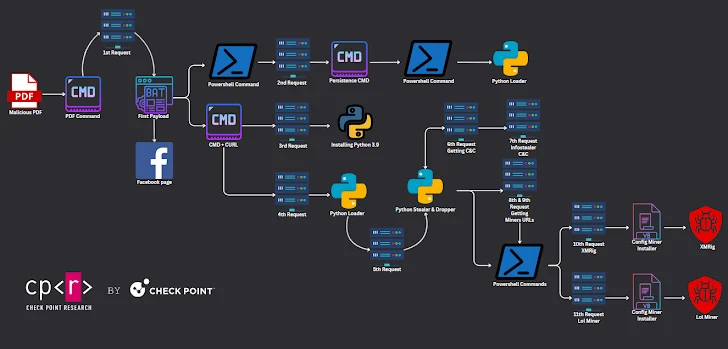
The Python-based stealer malware is supplied to steal victims’ credentials and cookies from Chrome and Edge browsers, with the miners retrieved from a Gitlab repository belonging to a consumer named topworld20241. The repository, created on February 17, 2024, remains to be energetic as of writing.
In one other case documented by the cybersecurity firm, the PDF file acts as a conduit to retrieve from Discord CDN Clean-Grabber, an open-source data stealer that is out there on GitHub and which has been archived as of August 6, 2023.
“One other attention-grabbing case occurred when a malicious PDF included a hyperlink to an attachment hosted on trello[.]com,” Terefos stated. “Upon downloading, it revealed a secondary PDF file containing malicious code, which takes benefit of this
‘exploitation’ of Foxit Reader customers.”
The an infection pathway culminates within the supply of Remcos RAT, however solely after progressing by way of a sequence of steps that contain the usage of LNK information, HTML Utility (HTA), and Visible Primary scripts as intermediate steps.
The risk actor behind the Remcos RAT marketing campaign, who goes by the identify silentkillertv and claims to be an moral hacker with over 22 years of expertise, has been noticed promoting a number of malicious instruments by way of a devoted Telegram channel referred to as silent_tools, together with crypters and PDF exploits concentrating on Foxit PDF Reader. The channel was created on April 21, 2022.

Examine Level stated it additionally recognized .NET- and Python-based PDF builder companies reminiscent of Avict Softwares I Exploit PDF, PDF Exploit Builder 2023, and FuckCrypt that had been used to create the malware-laced PDF information. The DoNot Group is claimed to have used a .NET PDF builder freely out there on GitHub.
If something, the usage of Discord, Gitlab, and Trello demonstrates the continued abuse of reputable web sites by risk actors to mix in with regular community visitors, evade detection, and distribute malware. Foxit has acknowledged the problem and is predicted to roll out a repair in model 2024 3. The present model is 2024.2.1.25153.
“Whereas this ‘exploit’ does not match the classical definition of triggering malicious actions, it might be extra precisely categorized as a type of ‘phishing’ or manipulation geared toward Foxit PDF Reader customers, coaxing them into habitually clicking ‘OK’ with out understanding the potential dangers concerned,” Terefos stated.
“The an infection success and the low detection price permit PDFs to be distributed by way of many untraditional methods, reminiscent of Fb, with out being stopped by any detection guidelines.”




