SonicWall has confirmed that every one clients that used the corporate’s cloud backup service are affected by the security breach final month.
Beforehand, the seller acknowledged that the incident “uncovered firewall configuration backup information saved in sure MySonicWall accounts,” with out sharing further particulars.
MySonicWall is an internet buyer portal used for managing product entry, licensing, registration, firmware updates, assist instances, and cloud backups of firewall configurations (.EXP information).
On September 17, the corporate warned clients to reset their MySonicWall account credentials to guard their firewall configuration backup information that may very well be doubtlessly accessed by unauthorized actors who had breached its methods.
To assist directors navigate the chance stemming from the breach, the corporate offered the important steps of the reset process, which ought to cowl all credentials, API keys, and customers’ authentication tokens, VPN accounts, and providers.
The corporate offers a guidelines “to make sure all related passwords, keys, and secrets and techniques are up to date constantly.” Essential actions consult with the next preocedures:
- resetting and updating passwords of all native customers
- reseting non permanent entry codes (TOTP) for native customers
- updating passwords on LDAP, RADIUS, or TACACS+ servers
- updating the shared secret in all IPSec site-to-site and GroupVPN insurance policies
- updating the passwords used for any L2TP/PPPoE/PPTP WAN interfaces
- resetting the Cloud Safe edge (CSE) API key
The listing additionally consists of much less important motion, which refers to updating AWS keys for logging and VPN integration, resetting SNMPv3 consumer credentials and updating passwords for WWAN connections.
“Entry to the uncovered firewall configuration information comprise data that would make exploitation of firewalls considerably simpler for risk actors,” warned SonicWall on the time, additionally publishing detailed remediation steering.
On the time, SonicWall specified that roughly 5% of its firewall clients use its cloud backup service.
In an replace printed yesterday the seller mentioned that the incident impacts all clients who used its cloud backup portal to retailer firewall configuration information.
“SonicWall has accomplished its investigation, carried out in collaboration with main IR Agency, Mandiant, into the scope of a current cloud backup security incident,” reads the up to date bulletin.
“The investigation confirmed that an unauthorized celebration accessed firewall configuration backup information for all clients who’ve used SonicWall’s cloud backup service.”
The uncovered information comprise AES-256-encrypted credentials and configuration knowledge.
Customers can now examine if their units are among the many impacted ones by logging into MySonicWall and going to ‘Product Administration → Concern Record.’
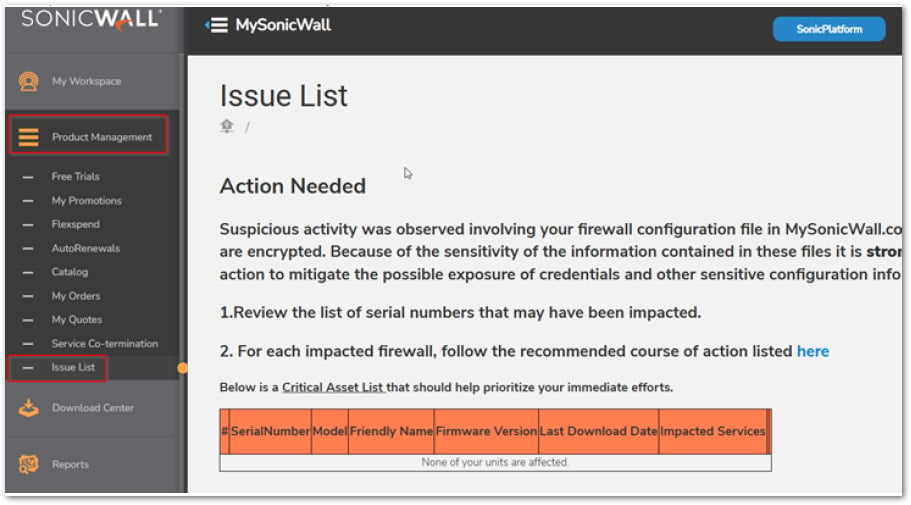
If any motion objects are pending evaluate there, customers ought to observe the Important Credential Reset steps, prioritizing lively, internet-facing firewalls.
Though SonicWall has acknowledged that the investigation is now full, it could be prudent for system directors to proceed monitoring MySonicWall alerts periodically for up to date lists of affected units.
Replace [10:28]: Article up to date with a listing of important remediation steps from SonicWall

Be a part of the Breach and Attack Simulation Summit and expertise the way forward for security validation. Hear from prime specialists and see how AI-powered BAS is remodeling breach and assault simulation.
Do not miss the occasion that can form the way forward for your security technique




