People are complicated beings with consciousness, feelings, and the capability to behave based mostly on ideas. Within the ever-evolving realm of cybersecurity, people persistently stay main targets for attackers. Over time, these attackers have developed their experience in exploiting varied human qualities, sharpening their abilities to govern biases and emotional triggers with the target of influencing human behaviour to compromise security whether or not it’s private and organisational security.
Greater than only a ‘human issue’
Understanding what defines our humanity, recognizing how our qualities might be perceived as vulnerabilities, and comprehending how our minds might be focused present the inspiration for figuring out and responding after we inevitably change into the goal.
The human thoughts is a fancy panorama that advanced over years of publicity to the pure surroundings, interactions with others, and classes drawn from previous experiences.
As people, our minds set us aside, marked by a mess of traits and feelings, usually too sophisticated to articulate exactly.
Human behaviour is complicated
A few of our basic traits might be outlined as follows:
- Belief – People place their belief in others, assuming inherent goodness.
- Empathy – People exhibit take care of others and their emotions.
- Ego – People harbour a aggressive spirit, aspiring to outshine their friends.
- Guilt – People expertise regret for his or her actions, particularly after they hurt others.
- Greed – People want possessions and will succumb to impulsivity.
- Urgency – People reply promptly to conditions demanding fast consideration.
- Vulnerability – People usually grapple with worry and are candid about their feelings.
Whereas this record isn’t exhaustive, it summarises widespread and comprehensible features that drive human behaviour. Human interactions maintain important worth, instilling life with significance and advancing cultural norms. Nonetheless, for attackers searching for to take advantage of us, the social assemble of human-to-human interactions gives a pathway for manipulation.
Safety Navigator 2024 is Right here – Obtain Now
The long-awaited Safety Navigator 2024 has formally launched, providing unprecedented insights into at present’s digital risks.With 129,395 incidents resulting in 25,076 confirmed breaches, this report isn’t just a doc; it is a roadmap to a safer digital future.
What’s Inside?
- International Snapshot: Discover the intricate internet of worldwide occasions, cyber extortion, and the way geopolitics intertwines with hacktivism.
- Regional Impression: Uncover the precise results of cyber-attacks throughout varied areas and industries.
🔗 Get Your Copy Now
Our naturally social nature forces us to revert to those traits. Feelings function a security web for communication, problem-solving, and connections in our on a regular basis life and now we have come to belief our emotional responses to additional information and defend us in a wide range of conditions.
I believe, subsequently I might be manipulated
Attackers exploit this security web (feelings and basic traits) when focusing on people, as it may be manipulated to fulfil their aims. This security web weakens much more after we enterprise into the “on-line” realm, as sure safeguards fail attributable to a scarcity of perception. The abstraction of communication by way of a reputation on display screen usually misleads our minds in decoding conditions in a method that our feelings can’t precisely navigate.
Within the realm of manipulation, varied fashions and strategies have been employed over centuries to affect human behaviour. In at present’s context, attackers exploit these fashions to establish human vulnerabilities, characterised as weaknesses inside the system that may be exploited.
Along with instantly manipulating basic traits by way of rigorously focused assaults, attackers have a tendency to focus on people by way of types of affect and persuasion. These might be summarised as follows, and people are inclined to function mentally in these realms:
- Reciprocation – People really feel compelled to reciprocate what they’ve acquired.
- Authority – People are inclined to adjust to authoritative/recognized figures.
- Shortage – People want objects which might be much less attainable.
- Dedication & Consistency – People favour routine and construction.
- Liking – People type emotional connections.
- Social Proof – People search validation and fame.
These features might be seen as potential vulnerabilities within the human thoughts when mixed with feelings and basic traits. Attackers leverage these features to achieve direct management over our actions, an prevalence now recognised as social engineering. Social engineering encompasses varied methods and ways, but at its core, it exploits a number of of the areas talked about above by way of precisely crafted interactions.
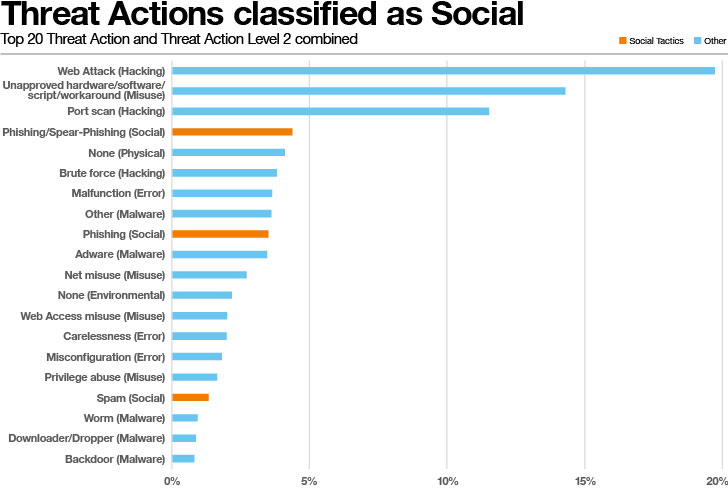
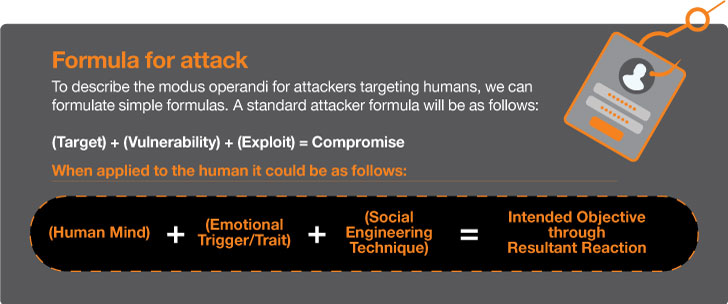

Exploitation methods, usually seen in digital channels like e mail, cellphone calls, or textual content messages, are ceaselessly used for phishing. These ways manipulate established interactions to attain varied aims, reminiscent of deceiving people into parting with funds, opening malicious recordsdata, submitting credentials, or revealing delicate knowledge. The implications of those assaults can differ from particular person losses to organizational breaches.
Defending ourselves
To safeguard towards these assaults towards our minds, we must always align our cognitive requirements with emotional triggers by asking questions like; what’s the objective, expectation, and legitimacy of the interplay. These questions might stop impulsive reactions and permit introspection.
Establishing a “cease and assess” mentality acts as a psychological firewall, strengthened by vigilance, to reinforce private and organisational security. By contemplating potential assaults, we heighten our consciousness of vulnerabilities and work on resilience. This consciousness, coupled with a proactive strategy, helps mitigate threats to our minds and humanity, selling collaboration to disarm attackers and weaken their operations.
Keep vigilant, keep knowledgeable, and proceed to query every little thing.
That is simply one of many tales discovered within the Safety Navigator. Different thrilling analysis like a examine of Hacktivism and an evaluation of the surge in Cyber Extortion (in addition to a ton of different attention-grabbing analysis matters) might be discovered there as nicely. It is freed from cost, so take a look. It is value it!
Be aware: This text was expertly written by Ulrich Swart, Coaching Supervisor & Technical Staff Chief at Orange Cyberdefense.




