Europol, the European Union’s regulation enforcement company, confirmed that its Europol Platform for Specialists (EPE) portal was breached and is now investigating the incident after a menace actor claimed they stole For Official Use Solely (FOUO) paperwork containing categorised knowledge.
EPE is a web based platform regulation enforcement consultants use to “share data, greatest practices and non-personal knowledge on crime.”
“Europol is conscious of the incident and is assessing the scenario. Preliminary actions have already been taken. The incident considerations a Europol Platform for Professional (EPE) closed person group,” Europol advised BleepingComputer.
“No operational info is processed on this EPE utility. No core methods of Europol are affected and subsequently, no operational knowledge from Europol has been compromised.”
BleepingComputer additionally requested when the breach occurred and whether or not it’s true FOUO and categorised paperwork had been stolen as claimed by the menace actor, however a response was not instantly accessible.
At publication time, the EPE web site was offline, and a message mentioned the service was unavailable as a result of it was beneath upkeep.

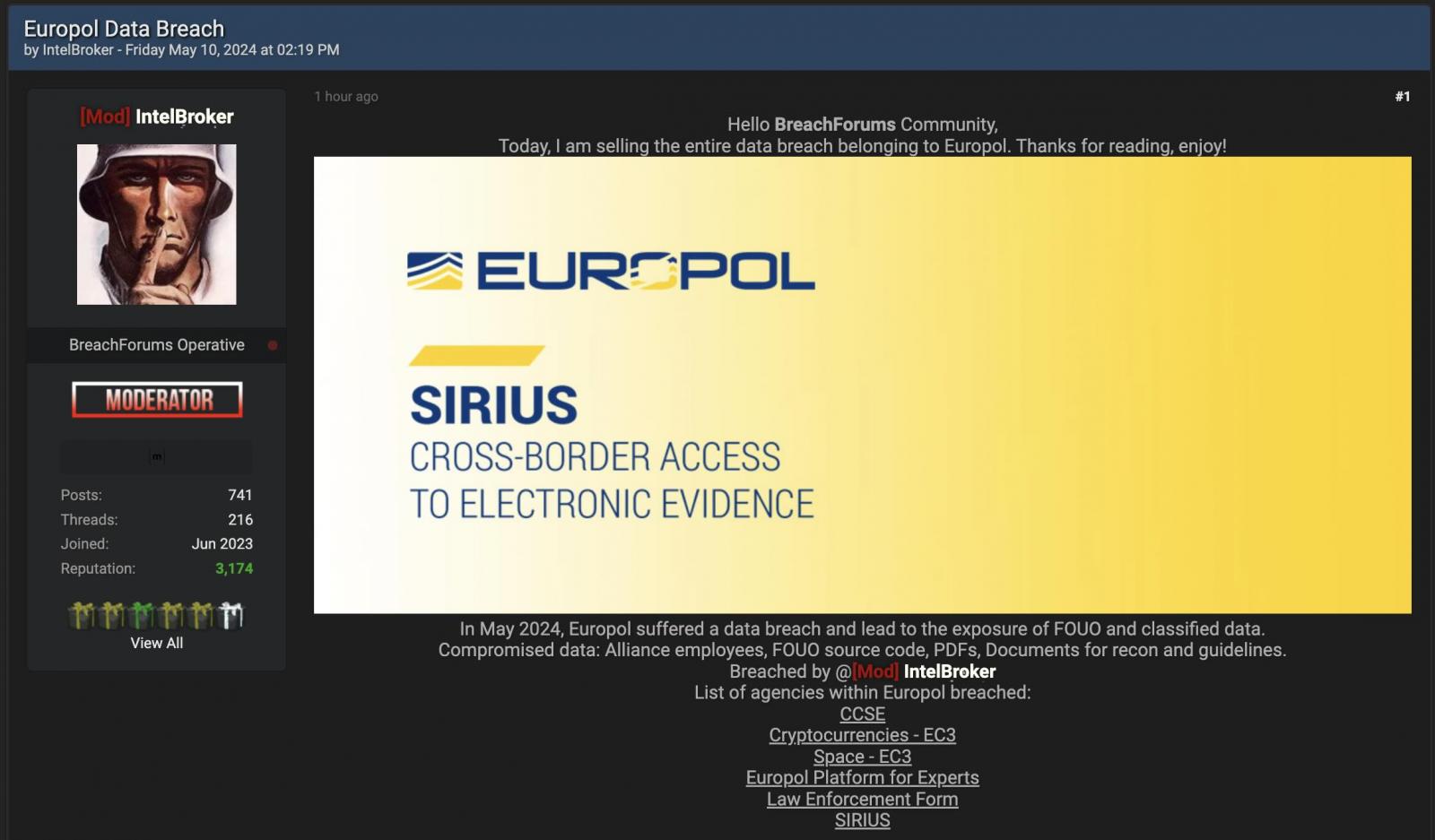
IntelBroker, the menace actor behind the data breach claims, describes the information as being FOUO and containing categorised knowledge.
The menace actor says the allegedly stolen knowledge consists of info on alliance staff, FOUO supply code, PDFs, and paperwork for recon and pointers.
Additionally they declare to have gained entry to EC3 SPACE (Safe Platform for Accredited Cybercrime Specialists), one of many communities on the EPE portal, internet hosting lots of of cybercrime-related supplies and utilized by over 6,000 licensed cybercrime consultants from around the globe, together with:
- Regulation enforcement from EU Member States’ competent authorities and non-EU international locations;
- Judicial authorities, educational establishments, personal corporations, non-governmental and worldwide organizations;
- Europol workers
IntelBroker additionally says they compromised the SIRIUS platform utilized by judicial and regulation enforcement authorities from 47 international locations, together with EU member states, the UK, international locations with a cooperation settlement with Eurojust, and the European Public Prosecutor’s Workplace (EPPO).
SIRIUS is used to entry cross-border digital proof within the context of felony investigations and proceedings
In addition to leaking screenshots of EPE’s on-line person interface, IntelBroker additionally leaked a small pattern of an EC3 SPACE database allegedly containing 9,128 information. The pattern comprises what seems to be like the non-public info of regulation enforcement brokers and cybercrime consultants with entry to the EC3 SPACE neighborhood.
“PRICING: Ship gives. XMR ONLY. Message me on the boards for a degree of contact. Proof of funds is required. I’m solely promoting to respected members,” the menace actor says in a Friday submit on a hacking discussion board.
Who’s IntelBroker?
Since December, this menace actor has been leaking knowledge he allegedly stole from numerous authorities companies, equivalent to ICE and USCIS, the Division of Protection, and the U.S. Military.
It’s unclear whether or not these incidents are additionally linked to the alleged April 2024 5 Eyes knowledge leak, however a few of the knowledge dumped within the ICE/USCIS discussion board submit overlaps with the 5 Eyes submit.
IntelBroker turned identified after breaching DC Well being Hyperlink, which manages well being care plans for U.S. Home members, workers, and households.
The breach led to a congressional listening to after the non-public knowledge of 170,000 affected people, together with U.S. Home of Representatives members and workers, was uncovered.
Different cybersecurity incidents linked to this menace actor are the breaches of Hewlett Packard Enterprise (HPE), Dwelling Depot, the Weee! grocery service, and an alleged breach of Basic Electrical Aviation.
Earlier this week, IntelBroker additionally began promoting entry info to the community of cloud security firm Zscaler (i.e., “logs full of credentials, SMTP Entry, PAuth Pointer Auth Entry, SSL Passkeys & SSL Certificates”).
Zscaler later confirmed they found an “remoted take a look at setting” uncovered on-line, which was taken offline for forensic evaluation regardless that no firm, buyer, or manufacturing environments had been impacted. Zscaler has additionally employed an incident response agency to run an unbiased investigation.




