What occurred
Proofpoint lately recognized a cluster of exercise conducting malicious e-mail campaigns utilizing piano-themed messages to lure folks into advance payment fraud (AFF) scams. The campaigns have occurred since not less than January 2024, and are ongoing. Many of the messages goal college students and college at faculties and universities in North America, nevertheless different focusing on of industries together with healthcare and meals and beverage providers was additionally noticed. Proofpoint noticed not less than 125,000 messages thus far this 12 months related to the piano rip-off campaigns cluster.
Within the campaigns, the menace actor purports to supply up a free piano, typically resulting from alleged circumstances like a demise within the household. When a goal replies, the actor instructs them to contact a transport firm to rearrange supply. That contact tackle may also be a pretend e-mail managed by the identical menace actor. The “transport firm” then claims they are going to ship the piano if the recipient sends them the cash for transport first.
Lure e-mail purporting to be freely giving a “free” piano.
Proofpoint
Delivery choices supplied by the pretend transport firm.
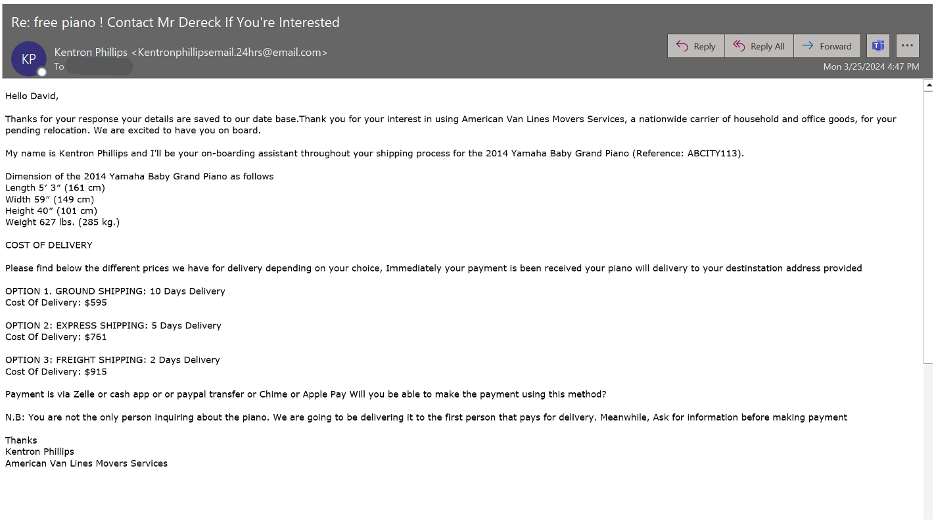
Proofpoint
The actor requests fee by way of a number of choices together with Zelle, Money App, PayPal, Apple Pay, or cryptocurrency. The actor additionally makes an attempt to gather personally identifiable data (PII) from the person together with names, bodily addresses, and telephone numbers.
Proofpoint recognized not less than one Bitcoin pockets tackle the piano rip-off fraudsters directed fee to. On the time of this writing, it contained over $900,000 in transactions. It’s probably that a number of menace actors are conducting quite a few various kinds of scams concurrently utilizing the identical pockets tackle given the amount of transactions, the variations in transaction costs, and general amount of cash related to the account.
Whereas the e-mail physique content material of the messages is comparable, the sender addresses fluctuate. Sometimes, the actors use freemail e-mail accounts, normally with some mixture of names and numbers. Many of the campaigns embody a number of variations on the e-mail content material and call addresses.
Attribution
To acquire extra details about the fraudsters, researchers began a dialogue with the actors and satisfied them to work together with a researcher-managed redirect service. Proofpoint was in a position to determine not less than one perpetrator’s IP tackle and system data. Based mostly on the data obtained, researchers assess with excessive confidence that not less than one a part of the operation is predicated in Nigeria.
Screenshot of part of a dialog between a researcher and menace actor.
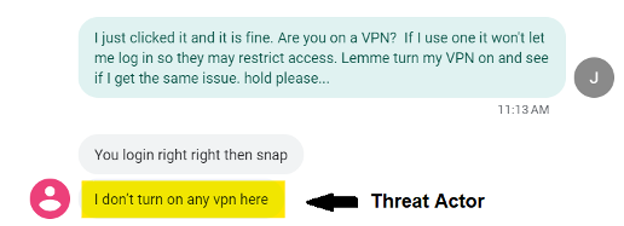
Proofpoint
Advance Payment Fraud (AFF), which prior to now has been known as 419,” “Nigerian 419,” or “Nigerian Prince” e-mail fraud, happens when a menace actor asks the potential sufferer for a small amount of cash upfront of a bigger, promised payout to be given to the sufferer at a later date. There are limitless variations of the sort of fraud. Typical schemes comprise elaborate tales that specify why there’s a giant sum of cash, job alternative, or different items or providers obtainable to the sufferer and why the sender wants a small upfront or superior payment earlier than the sufferer will get the promised cash or items. The fraudsters typically bait victims with topics reminiscent of inheritance, awards, authorities payouts, and worldwide enterprise.
As soon as the sufferer supplies the small amount of cash to the fraudster, nevertheless, they reduce all contact and disappear.
Why it issues
Proofpoint has beforehand revealed analysis on AFF campaigns utilizing a wide range of completely different themes to entice recipients to interact with them, together with employment alternatives focusing on college college students and cryptocurrency fraud. In all circumstances, AFF depends on elaborate social engineering and the usage of a number of completely different fee platforms. Folks ought to concentrate on the frequent strategies utilized by menace actors and do not forget that if an unsolicited e-mail sounds too good to be true, it in all probability is.
Indicators of compromise
| Indicator | Description | First Seen |
| hamj6842@gmail[.]com | Sender E-mail | March 2024 |
| Kentronphillipsemail.24hrs@e-mail[.]com | Sender E-mail | March 2024 |
| brireedmoversse@outlook[.]com | Sender E-mail | March 2024 |
| dereckadamsprivatemail21@mail[.]com | Sender E-mail | March 2024 |
| Kentronphillipsemail[.]24hrs@e-mail[.]com | Sender E-mail | March 2024 |
| aldo[.]moran97 @anahuac[.]mx | Sender E-mail | March 2024 |
| verocaress@gmail[.]com | Sender E-mail | March 2024 |
| 17kE4HzqAiPxwoC7rqHwJHoPwAk2bV2hKU | BTC Pockets | March 2024 |
| ABCITY113 | Reference Quantity | March 2024 |




