The Nationwide Police Company in South Korea issued an pressing warning right now about North Korean hacking teams concentrating on protection business entities to steal beneficial expertise info.
The police found a number of cases of profitable breaches of protection firms in South Korea involving the hacking teams Lazarus, Andariel, and Kimsuky, all a part of the North Korean hacking equipment.
In response to the announcement, the attackers breached the organizations by leveraging vulnerabilities in targets’ or their subcontractors’ environments to plant malware succesful to exfiltrate information.
The Nationwide Police Company and the Protection Acquisition Program Administration performed a particular inspection earlier this 12 months between January 15 and February 16 and applied protecting measures to safe crucial networks.
This particular operation found a number of firms that had been compromised since late 2022 however have been unaware of the breach till authorities knowledgeable them.
Various assaults
The police report highlights three circumstances involving every of the talked about hacking teams, displaying multi-faceted assault strategies geared toward stealing protection tech.
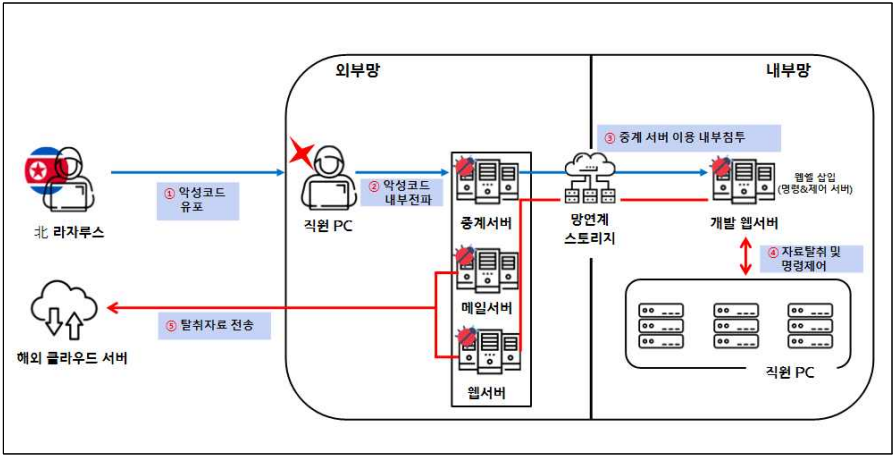
Lazarus hackers exploited poorly managed community connection techniques designed for testing and penetrated the inner networks of a protection firm since November 2022.
After infiltrating the community, they gathered crucial information saved in no less than six of the agency’s computer systems and transferred it to a cloud server overseas.
Korean police
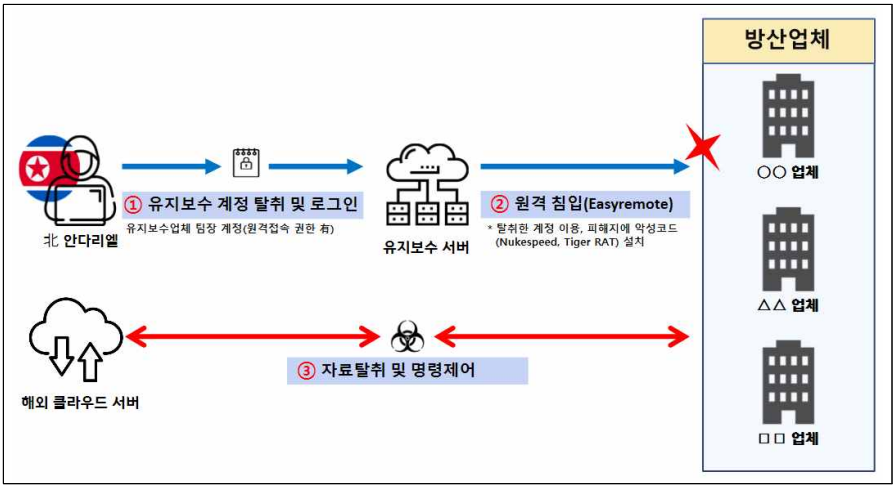
The second assault was attributed to the Andariel group, who stole account info from an worker of a upkeep firm that serviced protection subcontractors.
Utilizing this stolen account in October 2022, they put in malware on the servers of those subcontractors, resulting in important leaks of defense-related technical information.
This community infiltration was additional exacerbated by workers utilizing the identical passwords for private and work accounts.
Korean police
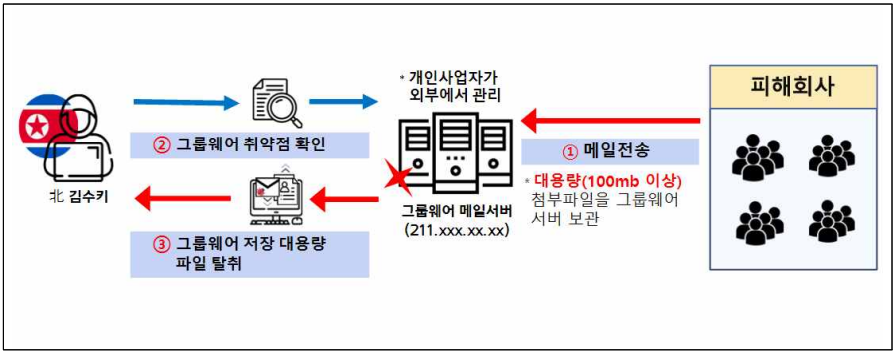
A 3rd assault highlighted within the police’s advisory, Kimsuky exploited a vulnerability within the e mail server of a protection subcontractor between April and July 2023, which allowed giant recordsdata to be downloaded with out the necessity to authenticate.
This vulnerability was used to obtain and steal substantial technical information from the corporate’s inner server.
Korean police
The Korean police recommends each protection firms and their subcontractors to enhance community security segmentation, periodic password resets, organising two-factor authentication on all crucial accounts, and blocking overseas IP accesses.




