Sponsored Put up: Dominique Kilman – Director at Unit 42 by – Palo Alto Networks
Not surprisingly, ransomware assaults proceed to rise as extra organizations fall sufferer to menace actor teams motivated by monetary acquire, notoriety, and espionage (on behalf of nation-states). Nonetheless, the character of ransomware assaults has advanced as multi-extortion assaults—involving encryption (victims pay to regain entry to their information), information theft (attackers threaten to launch stolen information), distributed denial-of-service (DDoS—public web sites and providers are shut down), and harassment (attackers straight contact/extort prospects, enterprise companions, and media)—have change into more and more frequent. In actual fact, roughly 10% of current ransomware assaults that the Palo Alto Networks Unit 42 responded to on behalf of shoppers didn’t contain any information encryption. Data theft and harassment, specifically, have risen considerably as most well-liked extortion ways over the previous 12 months (see Determine 1).
Sustaining dependable, immutable backups is a corporation’s greatest guess for recovering encrypted information with out paying a ransom. However attackers are actually pivoting to completely different ways and methods to monetize their nefarious efforts. Fairly than merely infiltrating a sufferer’s community, encrypting their information, then demanding a ransom cost, attackers observe an assault lifecycle methodology that features evading detection, establishing persistence, deploying malware, transferring laterally throughout the community (and linked companion networks), and exfiltrating beneficial information. Armed with a duplicate of the group’s most delicate information, an attacker can extort the group in trade for not disclosing the stolen information, straight harass and extort prospects, companions, and suppliers recognized within the stolen information, and/or promote the knowledge on the darkish net. This stolen information will also be utilized by attackers to craft very convincing phishing campaigns in opposition to the group and its prospects, companions, and suppliers. The rise of Ransomware as a Service (RaaS) additionally makes it comparatively simple for virtually anybody to execute a ransomware assault. RaaS is a subscription-based mannequin that permits menace actors (referred to as “associates”) to make use of predeveloped ransomware instruments to execute ransomware assaults. These associates then earn a proportion of every profitable ransom cost. Along with ready-to-deploy ransomware, associates may pay for assortment providers, technical help, and extra. Earlier than RaaS, menace actors wanted some proficiency in writing or accessing code to hold out a ransomware assault. With RaaS, menace actors require little-to-no coding experience.
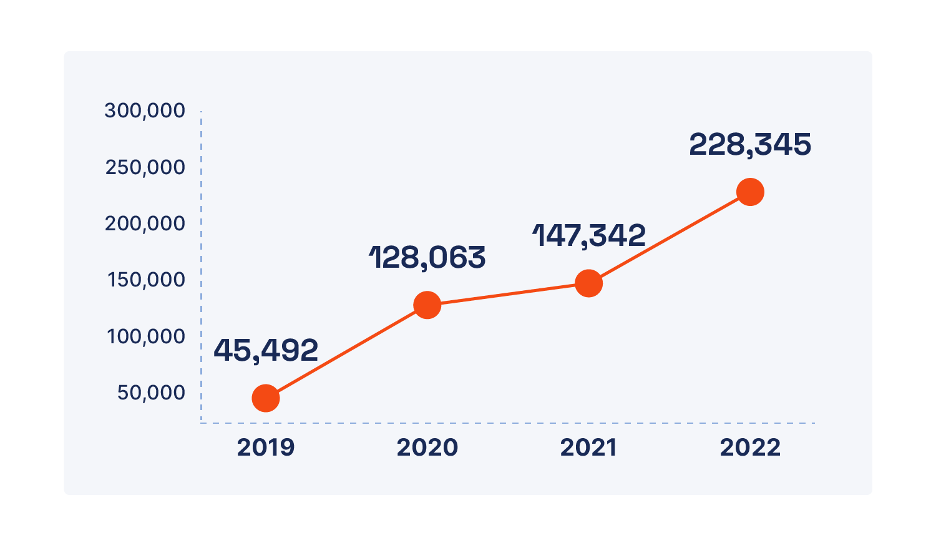
Past backups, organizations should keep a proactive patch administration program to guard in opposition to vulnerability exploits which are utilized by attackers to breach community defenses and infect techniques with malware (together with ransomware). In 2022, Palo Alto Networks Unit 42 analysis discovered a 55% enhance in exploitation of vulnerabilities in comparison with 2021 (see Determine 2).
The Log4j and Realtek provide chain vulnerabilities accounted for a lot of this enhance, however different vulnerabilities will inevitably be found and exploited sooner or later. As menace actor teams enhance their capabilities, the time between when a vulnerability is publicly disclosed and when it’s exploited continues to shrink. Within the case of Log4j, attackers started scanning for susceptible techniques throughout the Web inside minutes of disclosure.
Phishing continues to be a well-liked tactic amongst menace actors for stealing credentials and initially compromising networks. Social engineering is vital to a profitable phishing marketing campaign, and menace actors will more and more leverage synthetic intelligence (AI), comparable to ChatGPT, to ensnare even tech-savvy victims. Between November 2022 and April 2023, Palo Alto Networks Unit 42 menace analysis famous a 910% enhance in month-to-month area registrations—each benign and malicious—associated to ChatGPT, and a 17,818% development in makes an attempt to imitate ChatGPT by squatting domains (web sites which are fraudulently registered to trick victims into clicking a probably malicious hyperlink or visiting a probably malicious web site, for instance, https://www[.]pal[.]altonetworks[.]com).
Lastly, insider threats are one other disturbing pattern on the rise. Throughout difficult financial instances with a unstable job market, workers could discover it tempting to steal beneficial info for private monetary acquire or, within the case of a disgruntled worker, retribution. With extra workers now working remotely a minimum of a part of the time in our post-pandemic world, there could also be a notion—actual or imagined—that nobody is watching, and it’ll thus be simple to “get away with it.”
To guard your group from ransomware and different threats, a sturdy security technique should embrace the next parts:
- A playbook for multi-extortion assaults that features ransomware negotiation—every part is negotiable, even ransom calls for. Retain an expert ransomware negotiator as a part of your incident response plan—and “stress” take a look at your incident response plans repeatedly to make sure they’re complete and efficient.
- Safety orchestration and automatic response (SOAR) options with built-in menace intelligence administration and customizable out-of-the-box workflows for automating and dashing response to phishing marketing campaign incidents and mapping of threats found within the wild to incidents in your community.
- Proactive assault floor discount to reduce the variety of an infection vectors throughout your enterprise. Remember to embrace Linux and cell units because the honeymoon is over and menace actors are actually focusing on these techniques and units as properly.
- An efficient Zero Belief strategy to community entry to restrict the injury that an attacker can do as soon as inside your community. Microsegmentation with virtual- and container-based next-generation firewalls, steady verification, and granular entry controls restricts lateral motion and enforces the “by no means belief, all the time confirm” tenet of Zero Belief.
- Take a holistic view of your setting throughout clouds, datacenters, department places, distant and residential workplaces, and cell units. Leverage prolonged detection and response (XDR) know-how to quickly detect and routinely reply to security occasions as wanted.
- Implement strong menace intelligence and vulnerability administration packages. Leverage insights from trusted distributors and others in your business/group to share info and bolster your defenses. Additionally, do not forget that not all ransomware threats are related to “important” or “excessive” severity vulnerabilities—in truth, many threats benefit from the “low-and-slow” medium- to low-severity vulnerabilities that many organizations by no means get round to patching.
Study extra about ransomware threats and ransomware protection greatest practices at https://paloaltonetworks.com and hone your Cybersecurity Abilities with Cortex right here.
Remember to take a look at the next assets: