Hackers stole partial cost info and personally identifiable information, together with names and government-issued IDs, from some Discord customers after compromising a third-party customer support supplier.
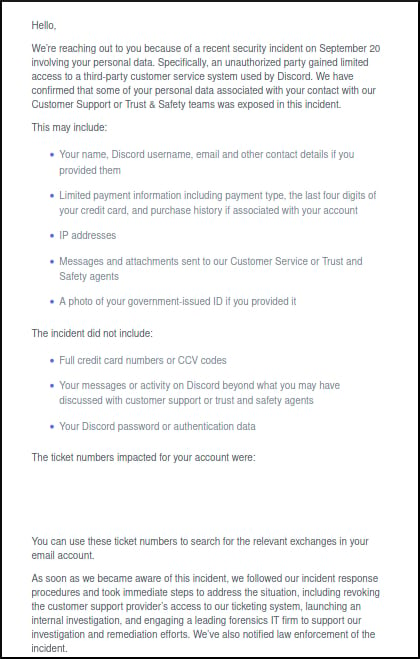
The assault occurred on September 20 and affected “a restricted variety of customers” who interacted with Discord’s buyer assist and/or Belief and Security groups.
Discord was created as a communication platform for avid gamers, who signify greater than 90% of the userbase, however expanded to numerous different communities, permitting textual content messages, voice chats, and video calls.
In response to the platform’s statistics, greater than 200 million individuals are utilizing Discord each month.
Hackers demanded a ransom
Within the notification to affected customers, the messaging firm says that the assault occurred on September 20 and “an unauthorized occasion gained restricted entry to a third-party customer support system utilized by Discord.”
On Friday, Discord disclosed the incident publicly, saying that it took speedy motion to isolate the assist supplier from its ticketing system and began an investigation.
This included revoking the client assist supplier’s entry to our ticketing system, launching an inside investigation, partaking a number one laptop forensics agency to assist our investigation and remediation efforts, and interesting regulation enforcement – Discord
The assault seems to be financially motivated, because the hackers demanded a ransom from Discord in alternate for not leaking the stolen info.
Uncovered information consists of personally figuring out info comparable to actual names and usernames, e-mail addresses, and different contact particulars offered to the assist workforce.
The social communication service says IP addresses, messages and attachments despatched to customer support brokers have been additionally compromised.
The hackers additionally accessed photographs of government-issued identification paperwork (driver’s license, passport) for a small variety of customers.
Partial billing information, like cost kind, the final 4 bank card digits, and buy historical past related to the compromised account, have been uncovered as properly.
supply: VX-Underground
VX-Underground security group notes that the kind of information stolen from Discord customers represents “actually peoples [sic] complete identification.”
Alon Gal, Chief Expertise Officer at risk intelligence firm Hudson Rock, believes that if the hackers launch the Discord information, it might present essential info to assist uncover or resolve crypto hacks and scams.
“I’ll simply say that if it leaks, this db goes to be big for fixing crypto associated hacks and scams as a result of scammers don’t usually keep in mind utilizing a burner e-mail and VPN and nearly all of them are on Discord,” says Alon Gal, Chief Expertise Officer at Hudson Rock
At present, it’s unclear what number of Discord customers are affected, and the identify of the third-party supplier or the entry vector has not been disclosed publicly.
Nonetheless, the Scattered Lapsus$ Hunters (SLH) risk group claimed the assault saying that they breached a Zendesk occasion utilized by Discord for buyer assist.
A picture the hackers posted on-line reveals a Kolide entry management listing for Discord staff with entry to the admin console. Kolide is a tool belief resolution that connects to Okta cloud-based Id and Entry Administration (IAM) service for multi-factor authentication.
SLH confirmed to BleepingComputer that it was a Zendesk breach that allowed them to steal the Discord person information.
BleepingComputer contacted Discord with a request for extra particulars in regards to the assault, however a remark from the social communications platform was not instantly obtainable.
It’s price noting that a whole lot of corporations had their Salesforce situations compromised after the ShinyHunters extortion group accessed them utilizing stolen Salesloft Drift OAuth tokens.
Final month, the hackers claimed to have stolen greater than 1.5 billion Salesforce information from 760 corporations.
Extra not too long ago, ShinyHunters launched an information leak website itemizing greater than three dozen victims.

Be part of the Breach and Attack Simulation Summit and expertise the way forward for security validation. Hear from prime specialists and see how AI-powered BAS is reworking breach and assault simulation.
Do not miss the occasion that can form the way forward for your security technique




