The favored open supply venture, ‘ip’ not too long ago had its GitHub repository archived, or made “read-only” by its developer.
Fedor Indutny, because of a CVE report filed in opposition to his venture, began getting hounded by folks on the web bringing the vulnerability to his consideration.
Sadly, Indutny’s case is not remoted. In current occasions, open-source builders have been met with an uptick in receiving debatable or, in some circumstances, outright bogus CVE studies filed for his or her tasks with out affirmation.
This will result in unwarranted panic among the many customers of those tasks and alerts being generated by security scanners, all of which flip right into a supply of headache for builders.
‘node-ip’ GitHub repository archived
Earlier this month, Fedor Indutny who’s the writer of the ‘node-ip’ venture archived the venture’s GitHub repository successfully making it read-only, and limiting the power of individuals to open new points (discussions), pull requests, or submit feedback to the venture.
The ‘node-ip’ venture exists on the npmjs.com registry because the ‘ip’ package deal which scores 17 million downloads weekly, making it one of the vital standard IP handle parsing utilities in use by JavaScript builders.
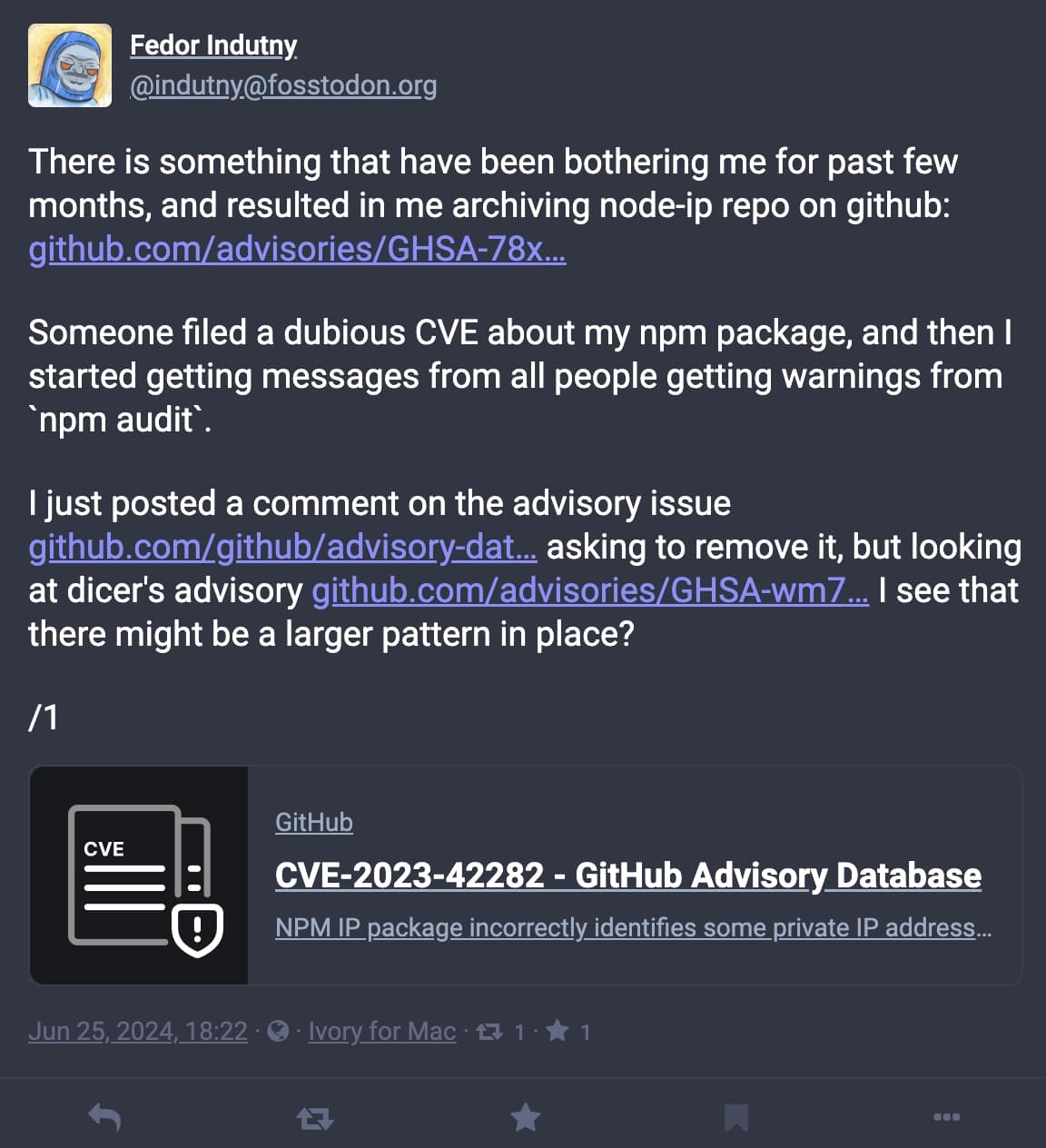
On Tuesday, June twenty fifth, Indutny took to social media to voice his reasoning behind archiving ‘node-ip’:
“There’s something which have [sic] been bothering me for previous few months, and resulted in me archiving node-ip repo on GitHub,” posted the developer by way of his Mastodon account.
It has to do with CVE-2023-42282, a vulnerability disclosed within the venture earlier this yr.
“Somebody filed a doubtful CVE about my npm package deal, after which I began getting messages from all folks getting warnings from ‘npm audit’,” states the developer in the identical put up.
Node.js builders utilizing different open tasks, equivalent to npm packages and dependencies of their utility can run the “npm audit” command to examine if any of those tasks utilized by their utility have had vulnerabilities reported in opposition to them.
The CVE has to do with the utility not appropriately figuring out non-public IP addresses equipped to it in a non-standard format, equivalent to hexadecimal. This might trigger the ‘node-ip’ utility to deal with a non-public IP handle (in hex format) equivalent to ” 0x7F.1…” (which represents 127.1…) as public.
Ought to an utility rely solely on node-ip to examine if a offered IP handle is public, non-standard inputs could cause inconsistent outcomes to be returned by the affected variations of the utility.
‘Doubtful’ security impression
Public sources counsel that CVE-2023-42282 had initially been scored as a 9.8 or “essential.”
Though Indutny did certainly repair the difficulty in later variations of his venture, he disputed that the bug constituted an precise vulnerability and that too of an elevated severity.
“I imagine that the security impression of the bug is quite doubtful,” the developer earlier wrote, requesting GitHub to revoke the CVE.
“Whereas I did not actually intend the module for use for any security associated checks, I am very curious how an untrusted enter might find yourself being handed into ip.isPrivate or ip.isPublic [functions] after which used for verifying the place the community connection got here from.”
Disputing a CVE is not any easy job both, as a GitHub security crew member defined. It requires a venture maintainer to chase the CVE Numbering Authorities (CNA) that had initially issued the CVE.
CNAs have conventionally comprised NIST’s NVD and MITRE. Over the previous few years, expertise corporations and security distributors joined the listing and are additionally capable of problem CVEs at will.
These CVEs, together with the vulnerability description and the reported severity score, are then syndicated and republished by different security databases, equivalent to GitHub advisories.
Following Indutny’s put up on social media, GitHub lowered the severity of the CVE of their database and urged the developer activate non-public vulnerability reporting to raised handle incoming studies and lower noise.
On the time of writing, the vulnerability’s severity on NVD stays “essential.”
A rising nuisance
The CVE system, initially designed to assist security researchers ethically report vulnerabilities in a venture and catalog these after accountable disclosure, has these days attracted a section of group members submitting unverified studies.
Whereas many of the CVEs are filed in good religion by accountable researchers and signify credible security vulnerabilities, a not too long ago rising sample includes beginner security fanatics and bug bounty hunters ostensibly “gathering” CVEs to counterpoint their resume quite than reporting security bugs that represent real-world, sensible impression from exploitation.
Consequently, builders and venture maintainers have pushed again.
In September 2023, Daniel Stenberg, creator of the well-known software program venture ‘curl’ rebuked the “bogus curl problem CVE-2020-19909,” a Denial of Service bug reported in opposition to the venture.
Initially scored as a 9.8 or essential in severity per NVD’s historical past, the now-disputed CVE has had its score dropped to a “low” 3.3 after discussions ensued questioning the tangible security impression of the flaw.
“This was not a novel occasion and it was not the primary time it occurred. This has been occurring for years,” Stenberg wrote criticizing the CVE entry.
“I’m not a fan of philosophical thought workouts round vulnerabilities.”
“They’re distractions from the true issues and I discover them quite pointless. It’s straightforward to check how this flaw performs out on quite a few platforms utilizing quite a few compilers.”
“It isn’t a security downside on any of them.”
In response to Stenberg, the technical particulars of the “foolish bug” meant it might lead to surprising conduct, not a security flaw that might be abused.
One more npm venture, micromatch which will get 64 million weekly downloads has had ‘excessive’ severity ReDoS vulnerabilities reported in opposition to it with its creators being chased by group members inquiring in regards to the points.
“Are you able to level out at the least one library that implements micromatch or braces that’s vulnerable to the vulnerability so we will see the way it’s truly a vulnerability in the true world, and never simply theoretical?” requested Jon Schlinkert, reacting to CVE-2024-4067 filed for his venture, micromatch.
In the identical thread, the developer, apparently after failing to obtain a passable proof of idea exploit from the vulnerability reporter responded with:
“I get these points on a regular basis for issues that may’t even be a vulnerability except you do it to your self. Like regex in low degree libraries that can by no means be accessible to a browser, except you are letting customers submit common expressions in an online type which might be simply utilized by your utility.”
“I requested for examples of how a real-world library would encounter these ‘vulnerabilities’ and also you by no means responding with an instance.”
I too, not too long ago messaged micromatch builders after a third occasion knowledgeable us of a possible “threat” posed by the venture, because it appeared just like the accountable factor to do on the time.
Sadly, versus representing an exploitable vulnerability, it ended up being a nuisance report (very similar to CVE-2024-4067) that builders had already been chased about.
Different than simply being an annoyance for venture maintainers, the act of getting CVEs issued for unverified vulnerability studies is akin to stirring up a Denial of Service (DoS) in opposition to a venture, its creators, and its wider shopper base, and for good causes.
Developer security options (equivalent to npm audit) that are designed to forestall weak elements from reaching your purposes might set off alerts if any recognized vulnerabilities are detected and relying in your settings, break your builds.
“Jackson had this downside a couple of months again, the place somebody reported a essential CVE in opposition to the venture and broke builds throughout the planet,” a commentator had written in 2023, reacting to the bogus curl CVE.
Somewhat than being a security downside with the venture, as different builders acknowledged, the difficulty represented the inherent nature of recursive Java knowledge buildings.
The place is the stability?
Recurring incidents like these elevate the query, how does one strike a stability?
Relentlessly reporting theoretical vulnerabilities can go away open-source builders, many of who’re volunteers, exhausted from triaging noise.
On the flip facet, wouldn’t it be moral if security practitioners, together with novices, sat on what they thought was a security flaw—in order to not inconvenience the venture maintainers?
A 3rd downside arises for tasks with out an energetic maintainer. Deserted software program tasks that haven’t been touched in years comprise vulnerabilities that, even when disclosed, won’t ever be mounted and there exists no means to contact their unique maintainer.
In such circumstances, intermediaries together with CNAs and bug bounty platforms are left in limbo.
On receiving a vulnerability report from a researcher, these organizations might not all the time be capable of sufficiently vet each such report independently. With out listening to from the (now absent) venture maintainers, they might be compelled to assign and publish CVEs after the “accountable disclosure” window has elapsed.
No easy reply exists to those issues simply but.
Till the security analysis, developer, and vendor communities come collectively to establish an efficient resolution, builders are sure to get pissed off with bogus studies burning them out, and the CVE system changing into flooded with exaggerated “vulnerabilities” which will look credible on paper however are successfully moot.




