Earlier this 12 months, Microsoft Entra ID (which by then was referred to as Azure Lively Listing) might have been simply hacked and compromised by hackers utilizing deserted reply URLs. A staff of researchers from SecureWorks found this vulnerability and alerted Microsoft.
The Redmond-based tech large shortly addressed the vulnerability and inside 24 hours of the preliminary announcement, it eliminated the deserted reply URL in Microsoft Entra ID.
Now, nearly 6 months after this discovery, the staff behind it, uncovered in a weblog put up, the method that lies behind infecting deserted reply URLs and utilizing them to set Microsoft Entra ID on hearth, basically compromising it.
Utilizing the deserted URL, an attacker might simply acquire elevated privileges of the group utilizing Microsoft Entra ID. For sure, the vulnerability posed an excellent threat, and Microsoft was apparently unaware of it.
An attacker might leverage this deserted URL to redirect authorization codes to themselves, exchanging the ill-gotten authorization codes for entry tokens. The menace actor might then name Energy Platform API by way of a middle-tier service and procure elevated privileges.
SecureWorks
That is how an attacker would benefit from the Microsoft Entra ID vulnerability
- The deserted reply URL can be found by the attacker and hijacked with a malicious hyperlink.
- This malicious hyperlink would then be accessed by a sufferer. Entra ID would then redirect the sufferer’s system to the reply URL, which might additionally embody the authorization code within the URL.
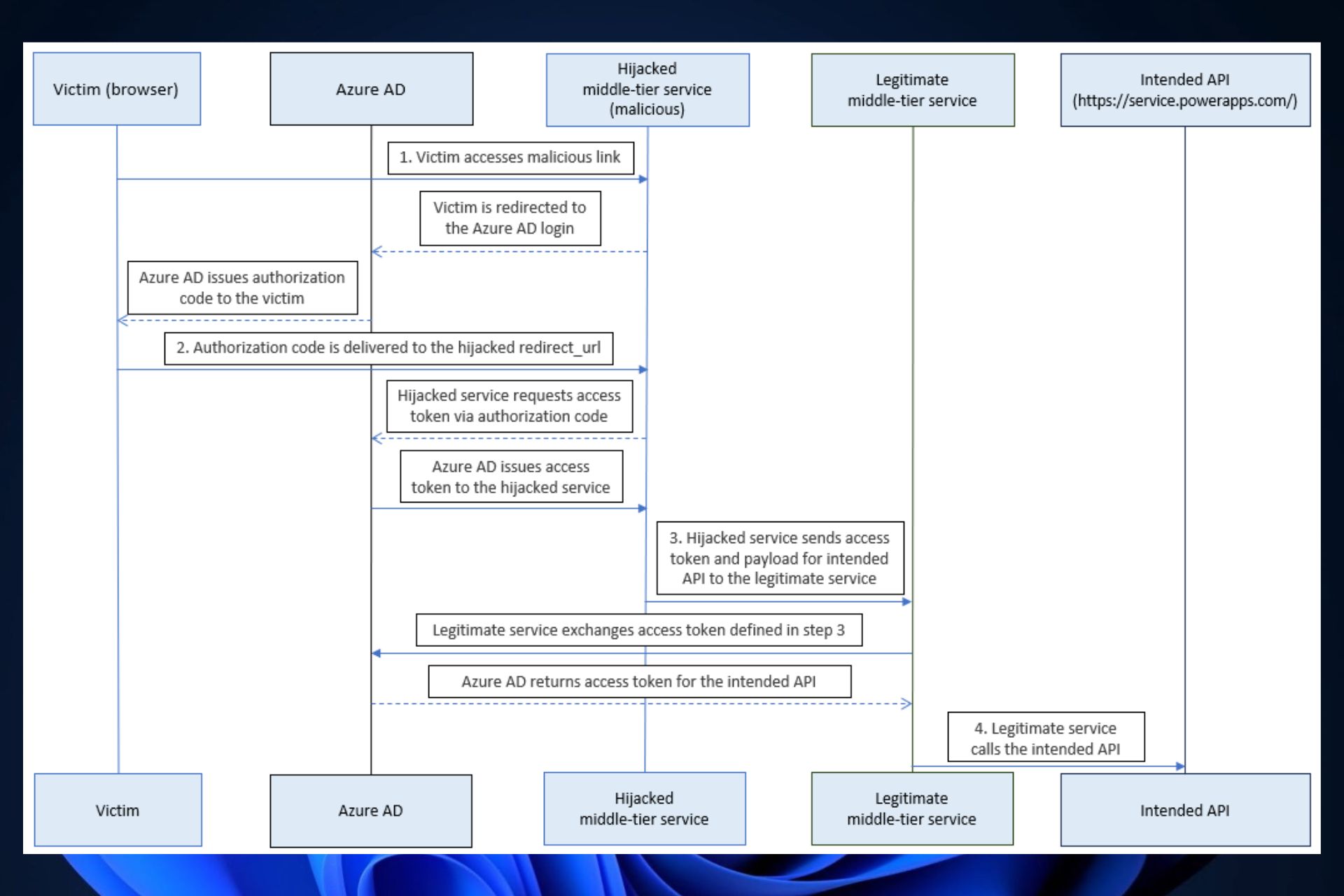
- The malicious server exchanges the authorization code for the entry token.
- The malicious server calls the middle-tier service utilizing the entry token and meant API, and the Microsoft Entra ID would find yourself being compromised.
Nonetheless, the staff behind the analysis additionally found that an attacker might merely change the authorization codes for entry tokens with out relaying tokens to the middle-tier service.
Given simply how simply would have been for an attacker to successfully compromise Entra ID servers, Microsoft shortly addressed this challenge, and it launched an replace to it on the next day.
However it’s fairly fascinating to see how the Redmond-based tech large by no means noticed this vulnerability to start with. Nonetheless, Microsoft does have a historical past of considerably neglecting vulnerabilities.
Earlier this summer season, the corporate was closely criticized by Tenable, one other prestigious cybersecurity agency, for failing to handle one other harmful vulnerability that may enable malignant entities to entry the financial institution info of Microsoft customers.
It’s clear that Microsoft must someway broaden its cybersecurity division. What do you consider it?




