An unfixed hardcoded encryption key flaw in Dell’s Compellent Integration Instruments for VMware (CITV) permits attackers to decrypt saved vCenter admin credentials and retrieve the cleartext password.
The flaw, tracked as CVE-2023-39250, is brought on by a static AES encryption key, shared throughout all installs, that’s used to encrypt the vCenter credentials saved in this system’s configuration file.
Dell Compellent is a line of enterprise storage methods providing options equivalent to information development, reside quantity, skinny provisioning, information snapshots and cloning, and built-in administration.
The software program helps storage integration with VMware vCenter, a broadly used platform for managing ESXi digital machines.
Nevertheless, to combine the consumer, it have to be configured with VMware vCenter credentials, that are saved within the Dell program’s encrypted configuration file.
A hardcoded AES encryption key
LMG Safety’s researcher Tom Pohl, found in a penetration train that Dell CITV incorporates a static AES encryption key that’s similar for all Dell prospects throughout all installs.
This AES encryption secret is used to encrypt the CITV configuration file containing this system’s settings, together with the entered vCenter admin credentials.
As AES is a symmetric cipher, it makes use of the identical key for encrypting and decrypting information. This permits an attacker who extracts the important thing to simply decrypt the configuration file and retrieve the encrypted password.
“The Dell software program wants administrative vCenter credentials to operate accurately, and it protects these credentials of their config information with a static AES key,” Pohl advised BleepingComputer.
“Dell is interacting with vCenter servers, and is retaining its credentials in an encrypted confih file that must be fully inaccessible for viewing by something or anybody aside from the Dell software program.”
“Attackers shouldn’t be capable of get entry to the contents of that file, however it’s accessible. Nevertheless, on account of this newly found vulnerability, attackers can extract the encryption key that the Dell software program is utilizing to guard the contents of that file.”
LMG Safety’s crew discovered that the Dell Compellent software program listing incorporates a JAR file that, when decompiled, revealed a hardcoded static AES key.
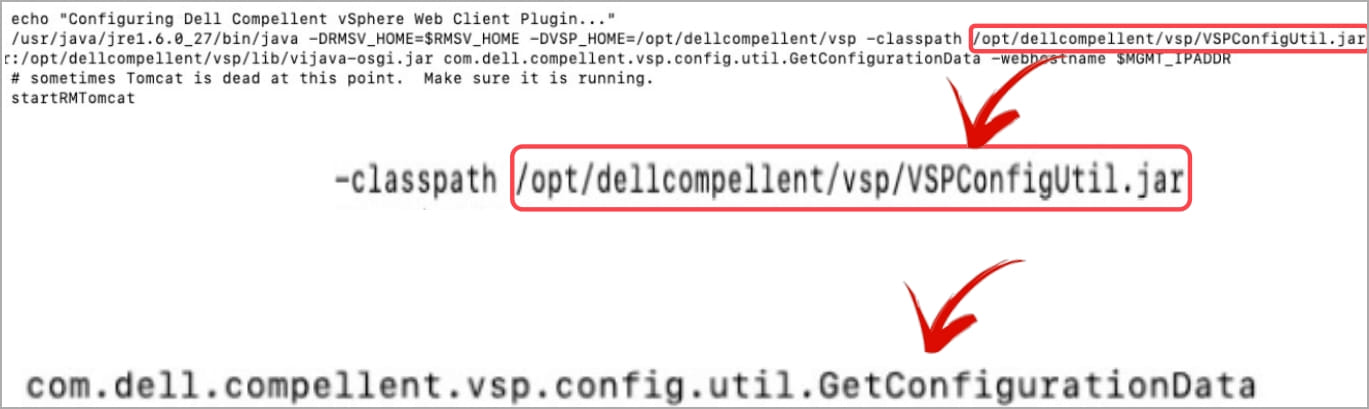
Utilizing this AES key, Pohl may decrypt the Dell Compellent configuration file and retrieve the person title and password for the VMware vCenter administrator, as proven under.
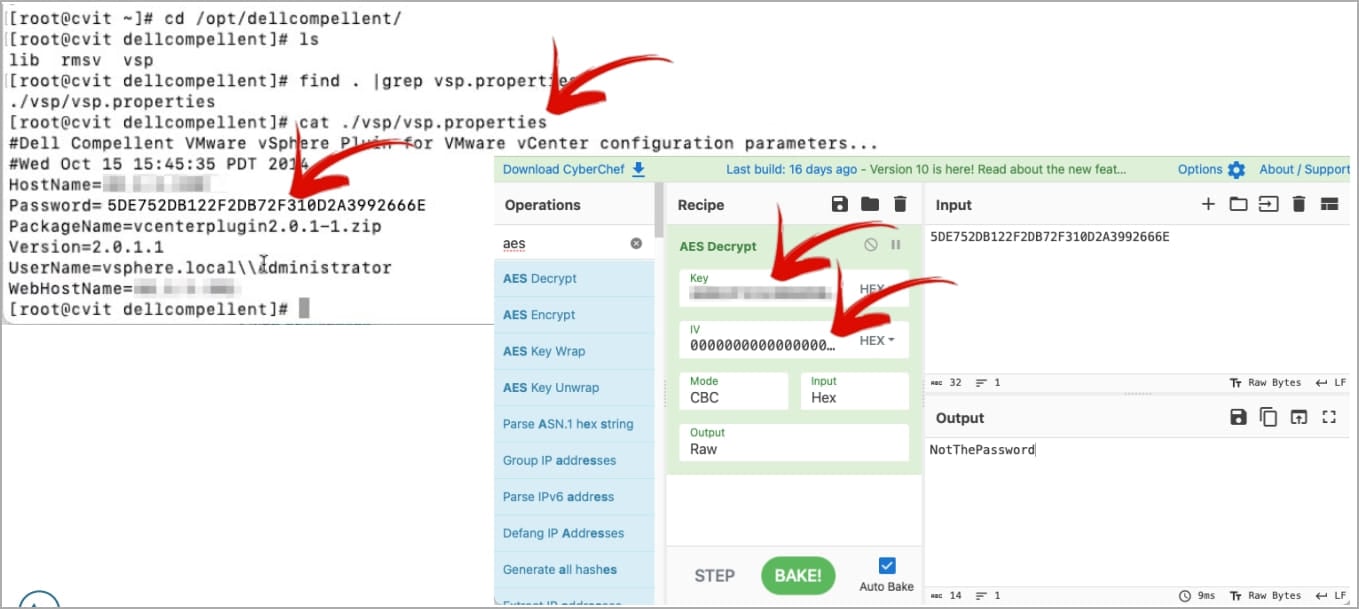
The server containing that key was accessible utilizing weak credentials (admin/admin). Nevertheless, as seen repeatedly, menace actors can acquire entry to servers in varied methods on account of vulnerabilities or unhealthy practices.
Additionally, the difficulty may very well be exploitable by rogue insiders or low-privileged exterior attackers who’ve entry to Dell CITV.
On this occasion, the LMG crew may have gone additional by leveraging entry to area controls however as a substitute opted to create a website admin account, exploiting the chance when a community admin mistakenly left their console unlocked.
The analysts emailed Dell to tell them about their discovery on April eleventh, 2023, however the pc and software program vendor initially dismissed the report, misunderstanding the scope.
After additional communication, Dell promised to roll out a repair by November 2023.
As the usual 90-day vulnerability disclosure coverage has expired, Pohl has publicly shared his analysis in a DEFCON session titled “Non-public Keys in Public Locations.”
Pohl found related hardcoded keys in Netgear and Fortinet in 2020, which have been subsequently mounted.
Replace 8/10/23: After the publishing of this story, Dell shared an advisory for CVE-2023-39250 with BleepingComputer that implies customers change the basis password of their Compellent units as a mitigation.
“Dell Applied sciences launched directions for a full workaround to handle a vulnerability within the Dell Storage Compellent Integration Instruments for VMware product. Prospects ought to evaluation Dell Safety Advisory DSA-2023-282 at their earliest comfort for particulars. The security of our merchandise is a high precedence and significant to defending our prospects.”
Nevertheless, it’s unclear how this might forestall an area person from extracting the AES key.
BleepingComputer has despatched comply with up questions relating to this advisory and can replace this text if we obtain a response.




