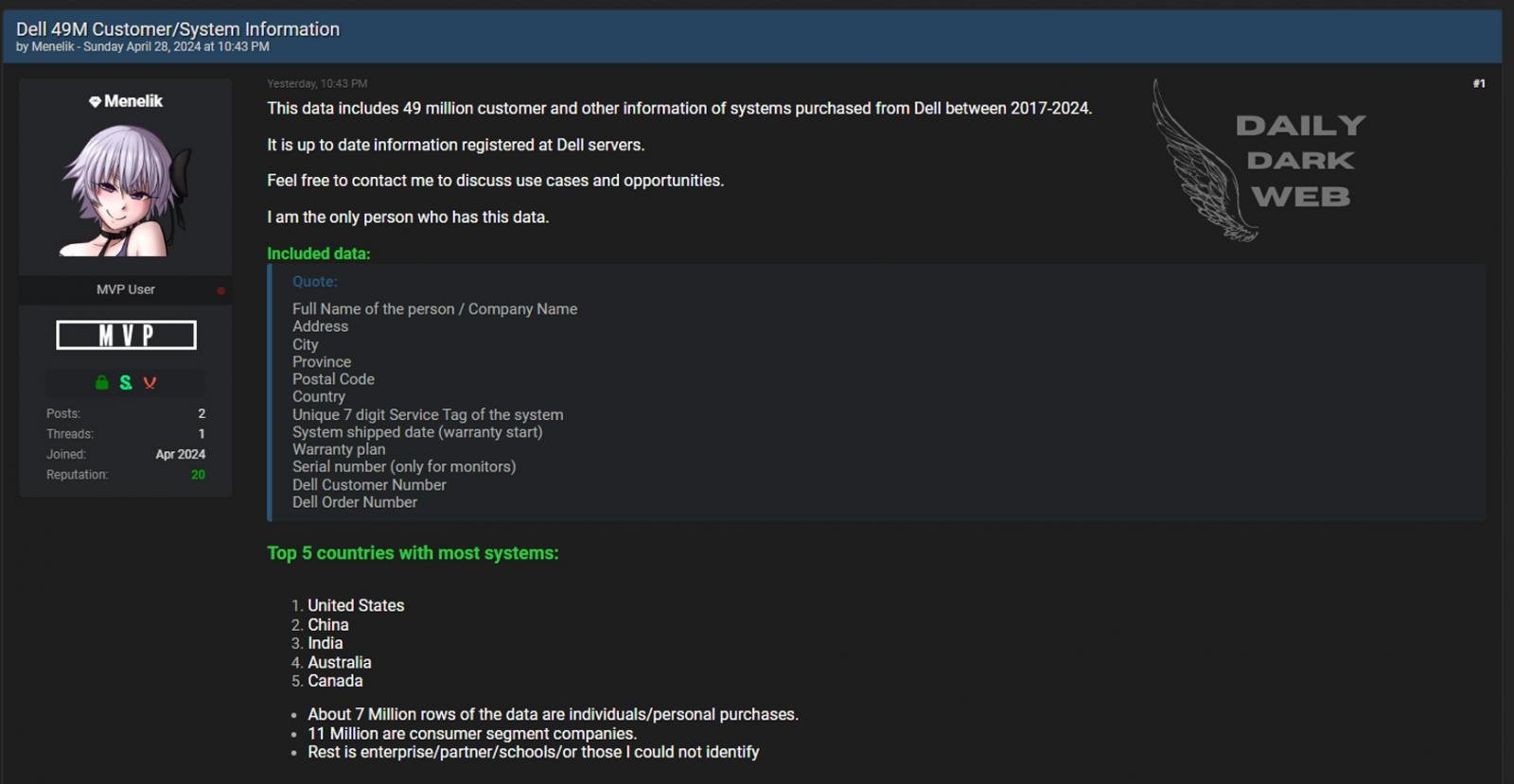
The menace actor behind the current Dell data breach revealed they scraped info of 49 million buyer information utilizing an companion portal API they accessed as a faux firm.
Yesterday, BleepingComputer reported that Dell had begun to ship notifications warning clients that their private knowledge was stolen in a data breach.
This data breach contained buyer order knowledge, together with guarantee info, service tags, buyer names, put in areas, buyer numbers, and order numbers.
A menace actor referred to as Menelik put the information up on the market on the Breached hacking discussion board on April twenty eighth, with the moderators quickly taking down the publish.
Supply: Every day Darkish Net
Menelik instructed BleepingComputer this morning they have been capable of steal the information after discovering a portal for companions, resellers, and retailers that may very well be used to search for order info.
Menelik says he might entry the portal by registering a number of accounts underneath faux firm names and had entry inside two days with out verification.
“It is vitally simple to register as a Companion. You simply fill an utility kind,” Menelik instructed BleepingComputer.
“You enter firm particulars, cause you need to turn into a companion, after which they simply approve you, and provides entry to this “approved” portal. I simply created my very own accounts on this approach. Complete course of takes 24-48 hours.”
As soon as they gained entry to the portal, Menelik instructed BleepingComputer that they had created a program that generated 7-digit service tags and submitted them to the portal web page beginning in March to scrape the returned info.
Because the portal reportedly didn’t embrace any charge limiting, the menace actor claims they may harvest the data of 49 million buyer information by producing 5,000 requests per minute for 3 weeks, with out Dell blocking the makes an attempt.
Menelik says the stolen buyer information embrace the next {hardware} breakdown:
- Screens: 22,406,133
- Alienware Notebooks: 447,315
- Chromebooks: 198,713
- Inspiron Notebooks: 11,257,567
- Inspiron Desktops: 1,731,767
- Latitude Laptops: 4,130,510
- Optiplex: 5,177,626
- Poweredge: 783,575
- Precision Desktops: 798,018
- Precision Notebooks: 486,244
- Vostro Notebooks: 148,087
- Vostro Desktops: 37,427
- Xps Notebooks: 1,045,302
- XPS/Alienware desktops: 399,695
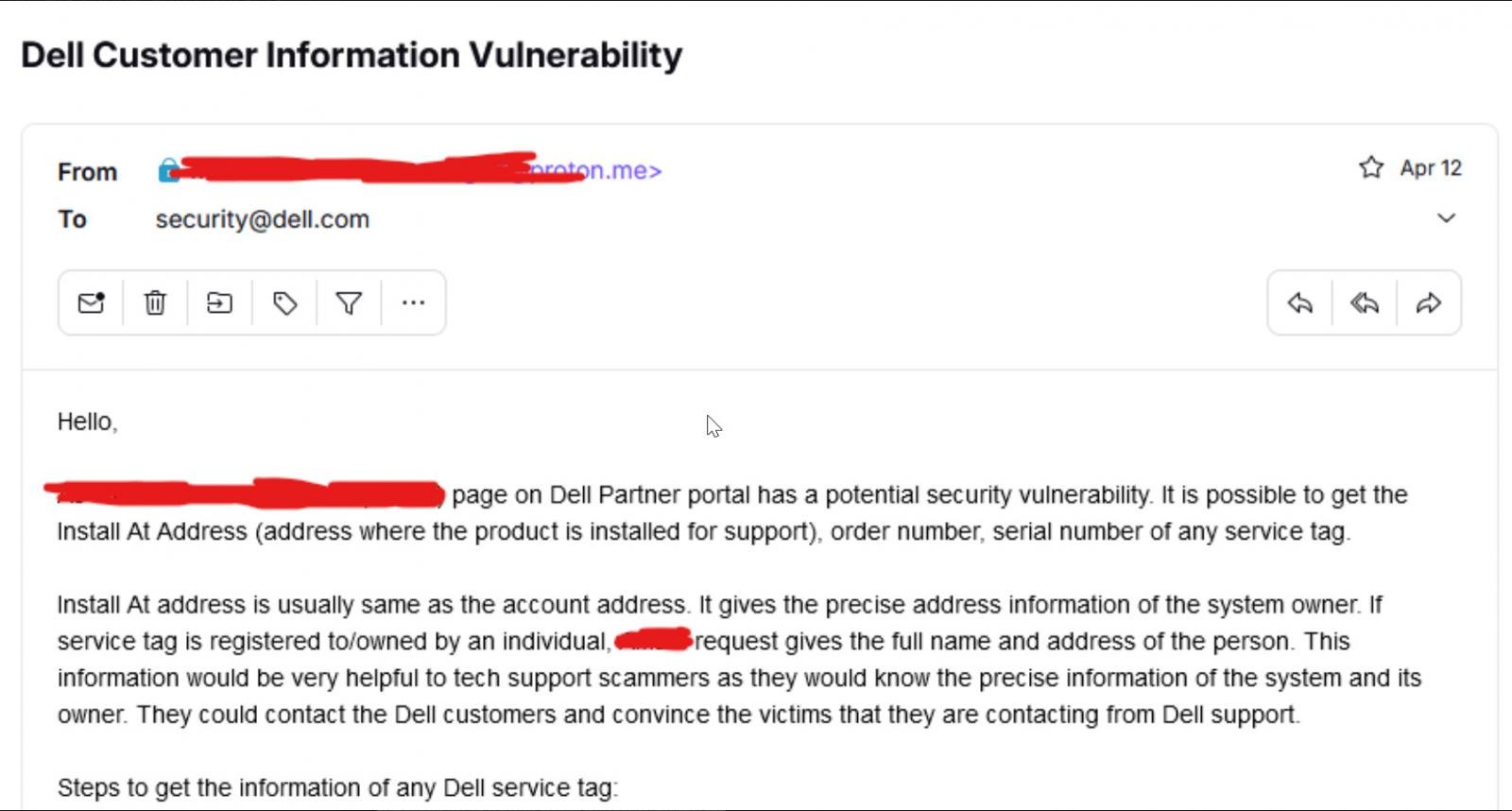
The menace actors stated they emailed Dell on April twelfth and 14th to report the bug to their security workforce, sharing the e-mail with BleepingComputer. Nonetheless, the menace actor admittedly harvested 49 million information earlier than contacting the corporate.
Supply: Menelik
The menace actor says Dell by no means replied to the emails and did not repair the bug till roughly two weeks later, across the time the stolen knowledge was first put up on the market on the Breach Boards hacking discussion board.
Dell confirmed to BleepingComputer they obtained the menace actor’s emails however declined to reply any additional questions, as they are saying the incident has turn into an energetic regulation enforcement investigation.
Nonetheless, the corporate claims that they had already detected the exercise earlier than receiving the menace actor’s e-mail.
“Let’s have in mind, this menace actor is a prison and we’ve got notified regulation enforcement,” Dell instructed BleepingComputer.
“We aren’t disclosing any info that might compromise the integrity of our ongoing investigation or any investigations by regulation enforcement.”
“Previous to receiving the menace actor’s e-mail, Dell was already conscious of and investigating the incident, implementing our response procedures and taking containment steps. We now have additionally engaged a third-party forensics agency to analyze.”
TechCrunch first reported Menelik’s use of this API to scrape Dell buyer knowledge.
APIs more and more abused in data breaches
Straightforward-to-access APIs have turn into a large weak point for firms in recent times, with menace actors abusing them to scrape delicate knowledge and promote them to different menace actors.
In 2021, menace actors abused a Fb API bug to hyperlink cellphone numbers to over 500 million accounts. This knowledge was leaked virtually free of charge on a hacking discussion board, solely requiring an account and paying $2 to obtain it.
Later that 12 months, in December, menace actors exploited a Twitter API bug to hyperlink hundreds of thousands of cellphone numbers and e-mail addresses to Twitter accounts, which have been then offered on hacking boards.
Extra lately, a Trello API flaw was exploited final 12 months to hyperlink an e-mail deal with to fifteen million accounts, which have been, as soon as once more, put up on the market on a hacking discussion board. The info was later shared with Have I Been Pwned to situation notifications to these uncovered in the breach.
Whereas all of those incidents concerned scraping of knowledge, they have been allowed because of the ease of entry to APIs and the dearth of correct charge limiting for the variety of requests that may be made per second from the identical host.




