A brand new phishing marketing campaign is leveraging decoy Microsoft Phrase paperwork as bait to ship a backdoor written within the Nim programming language.
“Malware written in unusual programming languages places the security neighborhood at an obstacle as researchers and reverse engineers’ unfamiliarity can hamper their investigation,” Netskope researchers Ghanashyam Satpathy and Jan Michael Alcantara stated.
Nim-based malware has been a rarity within the menace panorama, though that has been slowly altering in recent times as attackers proceed to both develop customized instruments from scratch utilizing the language or port present variations of their nefarious applications to it.
This has been demonstrated within the case of loaders equivalent to NimzaLoader, Nimbda, IceXLoader, in addition to ransomware households tracked below the names Darkish Energy and Kanti.
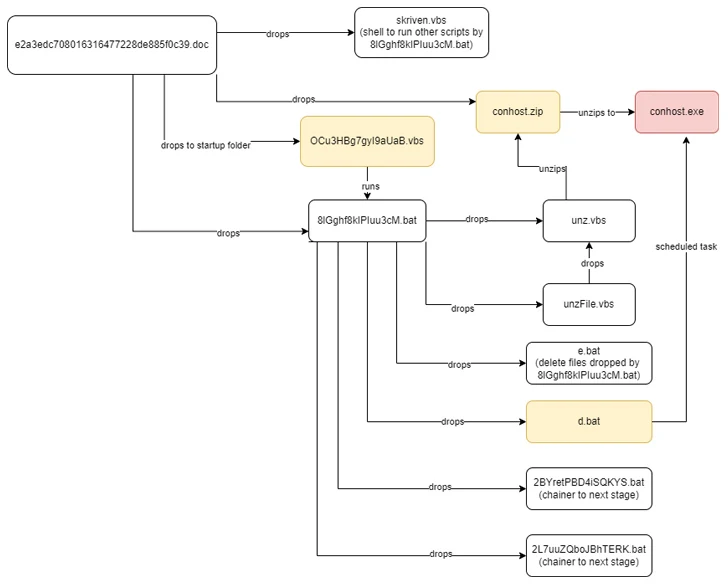
The assault chain documented by Netskope begins with a phishing e-mail containing a Phrase doc attachment that, when opened, urges the recipient to allow macros to activate the deployment of the Nim malware. The e-mail sender disguises themselves as a Nepali authorities official.
As soon as launched, the implant is chargeable for enumerating operating processes to find out the existence of identified evaluation instruments on the contaminated host and promptly terminate itself ought to it discover one.
In any other case, the backdoor establishes connections with a distant server that mimics a authorities area from Nepal, together with the Nationwide Info Know-how Middle (NITC) and awaits additional directions. The command-and-control (C2) servers are not accessible –
- mail[.]mofa[.]govnp[.]org
- nitc[.]govnp[.]org
- mx1[.]nepal[.]govnp[.]org
- dns[.]govnp[.]org
“Nim is a statically typed compiled programming language,” the researchers stated. “Except for its acquainted syntax, its cross-compilation options enable attackers to put in writing one malware variant and have it cross-compiled to focus on completely different platforms.”
The disclosure comes as Cyble revealed a social engineering marketing campaign that leverages messages on social media platforms to ship a brand new Python-based stealer malware known as Editbot Stealer that is designed to reap and exfiltrate useful knowledge by way of an actor-controlled Telegram channel.
At the same time as menace actors are experimenting with new malware strains, phishing campaigns have additionally been noticed distributing identified malware equivalent to DarkGate and NetSupport RAT by way of e-mail and compromised web sites with faux replace lures (aka RogueRaticate), notably these from a cluster dubbed BattleRoyal.
Enterprise security agency Proofpoint stated it recognized no less than 20 campaigns that used DarkGate malware between September and November 2023, earlier than switching to NetSupport RAT earlier this month.
One assault sequence recognized in early October 2023 notably stands out for chaining two visitors supply methods (TDSs) – 404 TDS and Keitaro TDS – to filter and redirect victims assembly their standards to an actor-operated area internet hosting a payload that exploited CVE-2023-36025 (CVSS rating: 8.8), a high-severity Home windows SmartScreen security bypass that was addressed by Microsoft in November 2023.
This means BattleRoyal weaponized this vulnerability as a zero-day a month earlier than it was publicly revealed by the tech large.
DarkGate is designed to steal data and obtain further malware payloads, whereas NetSupport RAT, which began off as a bona fide distant administration instrument, has metamorphosed right into a potent weapon wielded by malevolent actors to infiltrate methods and set up unfettered distant management.
“Cybercriminal menace actors [are] adopting new, various, and more and more inventive assault chains – together with using numerous TDS instruments – to allow malware supply,” Proofpoint stated.
“Moreover, using each e-mail and faux replace lures exhibits the actor utilizing a number of kinds of social engineering methods in an try to get customers to put in the ultimate payload.”
DarkGate has additionally been put to make use of by different menace actors like TA571 and TA577, each of that are identified to disseminate a wide range of malware, together with AsyncRAT, NetSupport, IcedID, PikaBot, and QakBot (aka Qbot).
“TA577 for instance, one of the outstanding Qbot distributors, returned to e-mail menace knowledge in September to ship DarkGate malware and has since been noticed delivering PikaBot in campaigns that sometimes have tens of hundreds of messages,” Selena Larson, senior menace intelligence analyst at Proofpoint, instructed The Hacker Information.




