Taiwanese networking gear producer D-Hyperlink confirmed a data breach linked to data stolen from its community and put up on the market on BreachForums earlier this month.
The attacker claims to have stolen supply code for D-Hyperlink’s D-View community administration software program, together with hundreds of thousands of entries containing private data of consumers and workers, together with particulars on the corporate’s CEO.
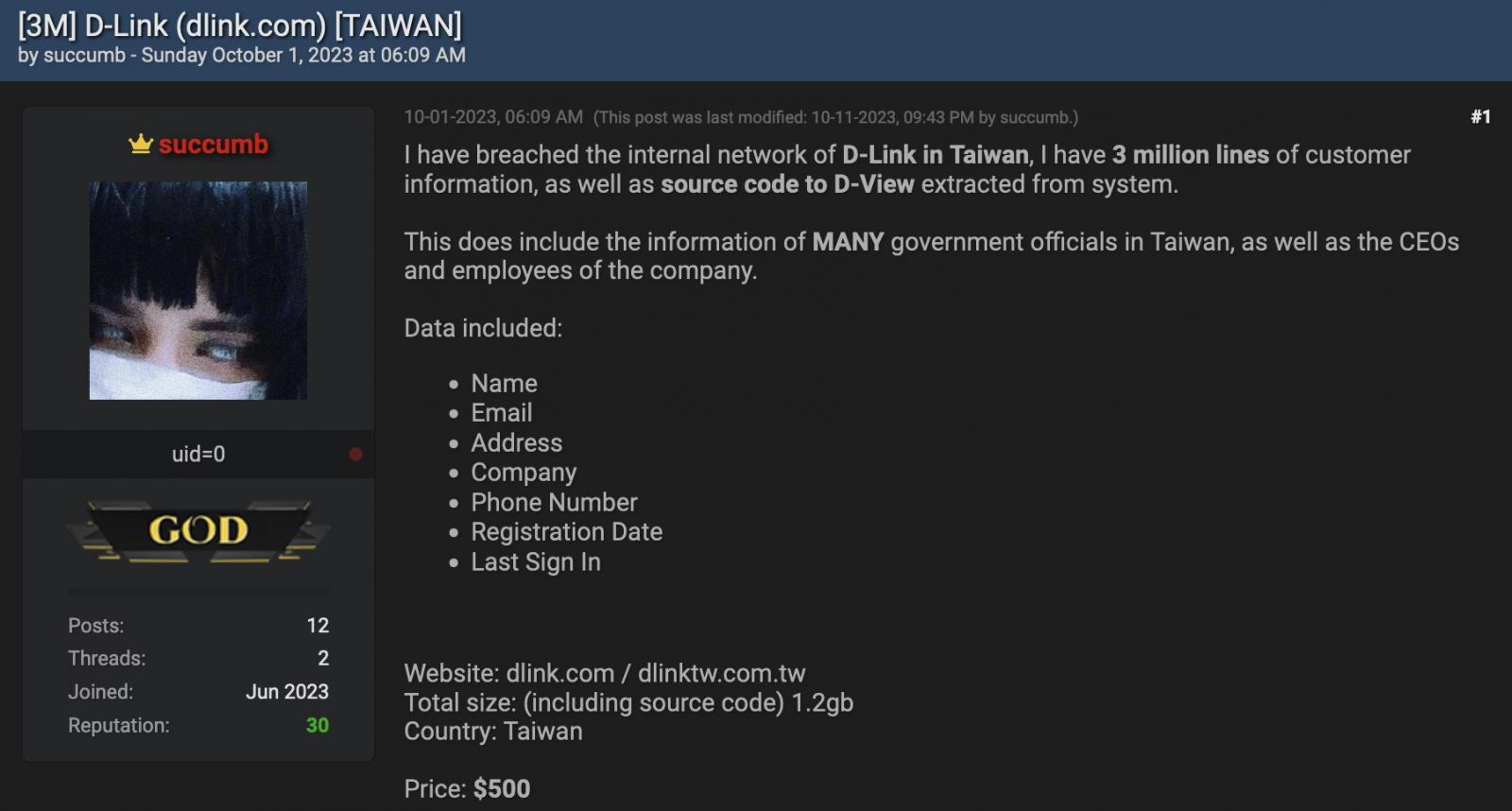
The stolen information allegedly consists of names, emails, addresses, telephone numbers, account registration dates, and the customers’ final sign-in dates.
The risk actor supplied samples of 45 stolen data with timestamps between 2012 and 2013, which prompted one other participant within the thread to remark on the truth that the info regarded very outdated.
“I’ve breached the inner community of D-Hyperlink in Taiwan, I’ve 3 million strains of buyer data, in addition to supply code to D-View extracted from system,” the attacker stated.
“This does embody the knowledge of MANY authorities officers in Taiwan, in addition to the CEOs and workers of the corporate.”
The information has been accessible for buy on the hacking discussion board since October 1st, with the risk actor demanding $500 for the stolen buyer data and the alleged D-View supply code.
Data stolen from a “take a look at lab” system
D-Hyperlink stated the security breach occurred attributable to an worker falling sufferer to a phishing assault, granting the attacker entry to the corporate’s community.
In response to the breach, the corporate instantly shut down probably impacted servers and disabled all however two consumer accounts used through the investigation.
Whereas it confirmed the breach, D-Hyperlink specified that the intruder accessed a product registration system inside what it described as a “take a look at lab atmosphere,” working on an outdated D-View 6 system that reached the tip of life in 2015.
The explanation why an end-of-life server was nonetheless operational on D-Hyperlink’s community, probably remaining uncovered to Web entry for seven years, stays unclear.
Opposite to the attacker’s declare of stealing hundreds of thousands of customers’ information, D-Hyperlink stated the compromised system contained roughly 700 data, with data on accounts which have been for at the least seven years.
“Based mostly on the investigations, nevertheless, it solely contained roughly 700 outdated and fragmented data that had been inactive for at the least seven years,” D-Hyperlink stated.
“These data originated from a product registration system that reached its finish of life in 2015. Moreover, nearly all of the info consisted of low-sensitivity and semi-public data.”
D-Hyperlink additionally suspects the risk actor intentionally tampered with the latest login timestamps to create the phantasm of a newer information theft. Moreover, the corporate said that almost all of its present prospects are unlikely to be impacted by this incident.




