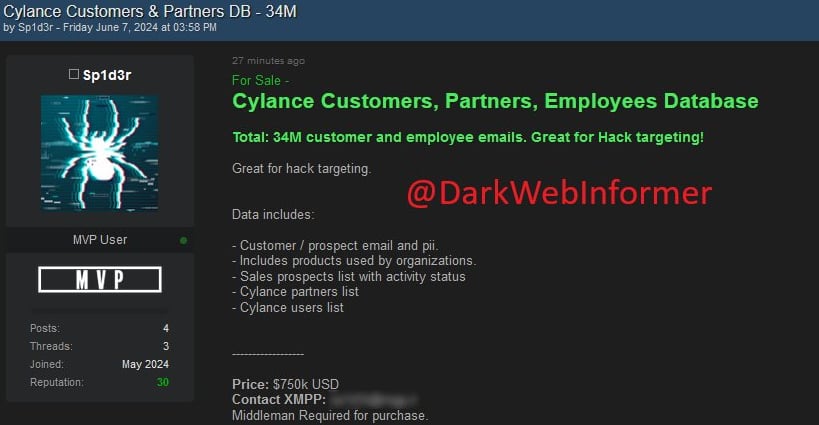
Cybersecurity firm Cylance confirmed the legitimacy of information being offered on a hacking discussion board, stating that it’s previous knowledge stolen from a “third-party platform.”
A menace actor referred to as Sp1d3r is promoting this stolen knowledge for $750,000, as first noticed by Darkish Internet Informer.
The info allegedly features a substantial quantity of data, resembling 34,000,000 buyer and worker emails and personally identifiable data belonging to Cylance clients, companions, and staff.
Nevertheless, researchers have informed BleepingComputer that the leaked samples look like previous advertising knowledge utilized by Cylance.
BlackBerry Cylance informed BleepingComputer that they are conscious of and investigating the menace actor’s claims however that no “BlackBerry knowledge and techniques associated to [..] clients, merchandise, and operations have been compromised.”
“Based mostly on our preliminary opinions of the info in query, no present Cylance clients are impacted, and no delicate data is concerned,” the corporate added.
“The info in query was accessed from a third-party platform unrelated to BlackBerry and seems to be from 2015-2018, predating BlackBerry’s acquisition of the Cylance product portfolio.”
Hyperlinks to Snowflake assaults
Whereas the corporate has but to answer to a follow-up request for extra particulars concerning the identify of the third-party platform that was breached to steal what it claims to be previous knowledge, the identical menace actor can be promoting 3TB of information from automotive aftermarket components supplier Advance Auto Elements, stolen after breaching the corporate’s Snowflake account.
BleepingComputer confirmed that Cylance is a Snowflake buyer, with the net administration console positioned at https://cylance.snowflakecomputing.com/.
Current breaches at Santander, Ticketmaster, and QuoteWizard/Lendingtree have additionally been linked to Snowflake assaults. Ticketmaster’s dad or mum firm, Reside Nation, additionally confirmed that a data breach had affected the ticketing agency after its Snowflake account was compromised on Might 20.
In a joint advisory with CrowdStrike and Mandiant, Snowflake stated that attackers had used stolen buyer credentials to focus on accounts with out multi-factor authentication safety.
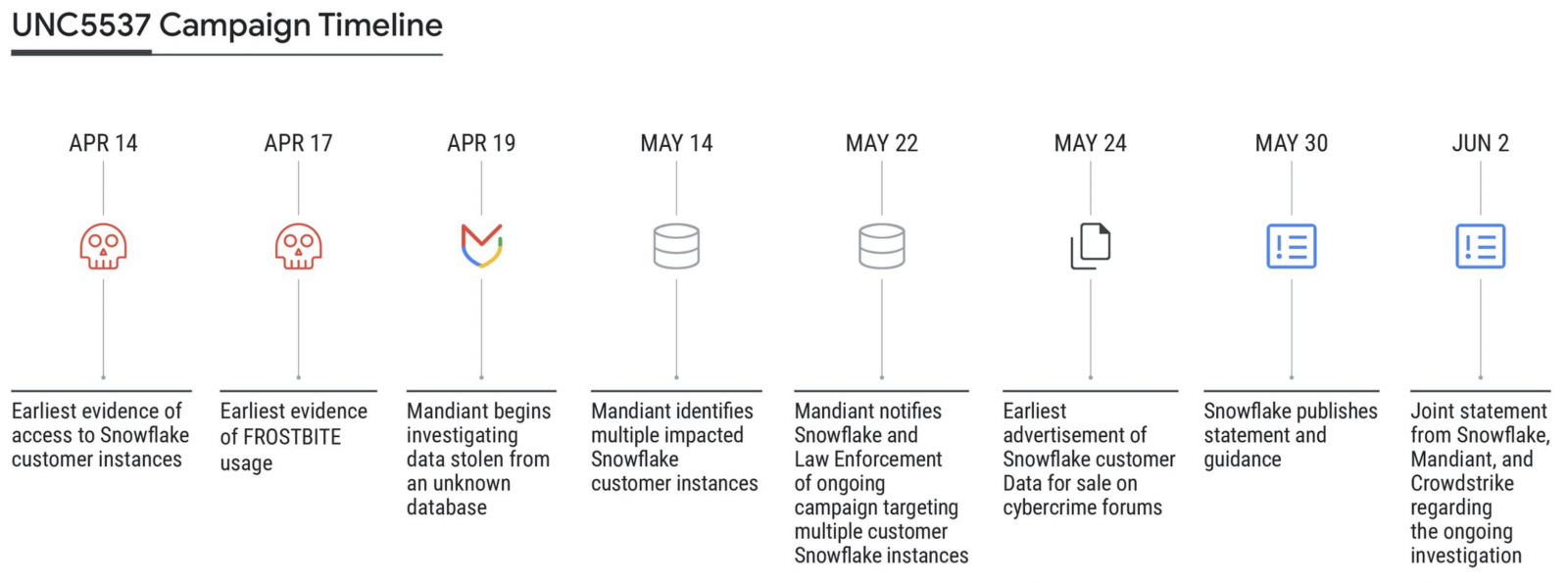
At present, Mandiant printed a report linking the Snowflake assaults to a financially motivated menace actor it tracks as UNC5537. The actor gained entry to Snowflake buyer accounts utilizing buyer credentials stolen in infostealer malware infections from way back to 2020.
Mandiant has been monitoring the UNC5537 since Might 2024. The financially motivated menace actor has focused lots of of organizations worldwide, extorting victims for monetary acquire.
Whereas Mandiant has not shared a lot details about UNC5537, BleepingComputer has discovered they’re half of a bigger group of menace actors who frequent the identical web sites, Telegram, and Discord servers, the place they generally collaborate on assaults.
“The impacted accounts weren’t configured with multi-factor authentication enabled, that means profitable authentication solely required a legitimate username and password,” Mandiant stated.
“Credentials recognized in infostealer malware output had been nonetheless legitimate, in some instances years after they had been stolen, and had not been rotated or up to date. The impacted Snowflake buyer cases didn’t have community permit lists in place to solely permit entry from trusted places.”
Mandiant says it has recognized lots of of buyer Snowflake credentials uncovered in Vidar, RisePro, Redline, Racoon Stealer, Lumm, and Metastealer infostealer malware assaults since a minimum of 2020.
So far, Snowflake and Mandiant have notified round 165 organizations doubtlessly uncovered to those ongoing assaults.




