The Cuba ransomware gang was noticed in assaults focusing on crucial infrastructure organizations in the USA and IT corporations in Latin America, utilizing a mix of outdated and new instruments.
BlackBerry’s Menace Analysis and Intelligence workforce, which noticed the most recent marketing campaign in early June 2023, reviews that Cuba now leverages CVE-2023-27532 to steal credentials from configuration information.
The actual flaw impacts Veeam Backup & Replication (VBR) merchandise, and an exploit for it has been accessible since March 2023.
Beforehand, WithSecure reported that FIN7, a bunch with a number of confirmed affiliations with numerous ransomware operations, was actively exploiting CVE-2023-27532.
Cuba assault particulars
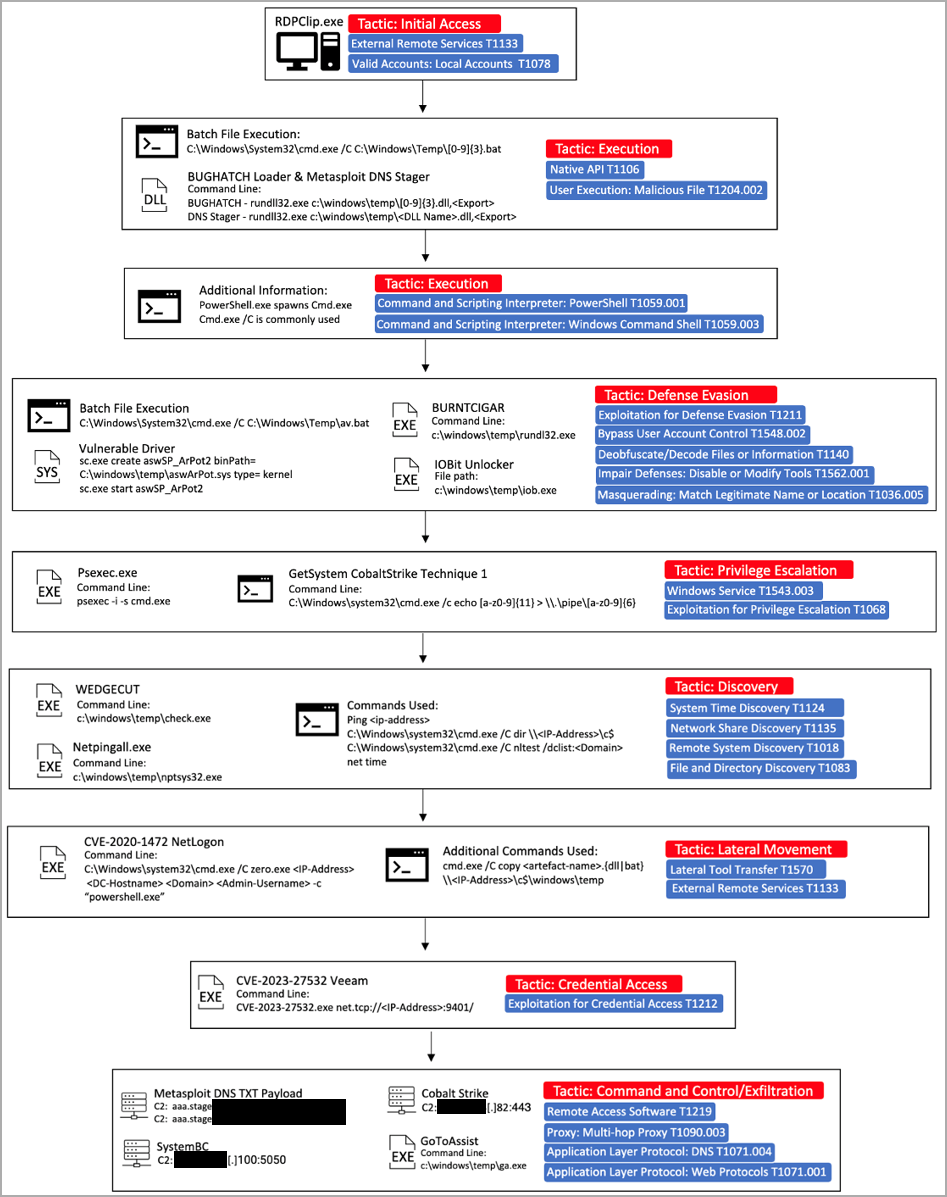
BlackBerry reviews that Cuba’s preliminary entry vector seems to be compromised admin credentials through RDP, not involving brute forcing.
Subsequent, Cuba’s signature customized downloader ‘BugHatch’ establishes communication with the C2 server and downloads DLL information or executes instructions.
An preliminary foothold on the goal atmosphere is achieved by way of a Metasploit DNS stager that decrypts and runs shellcode immediately in reminiscence.
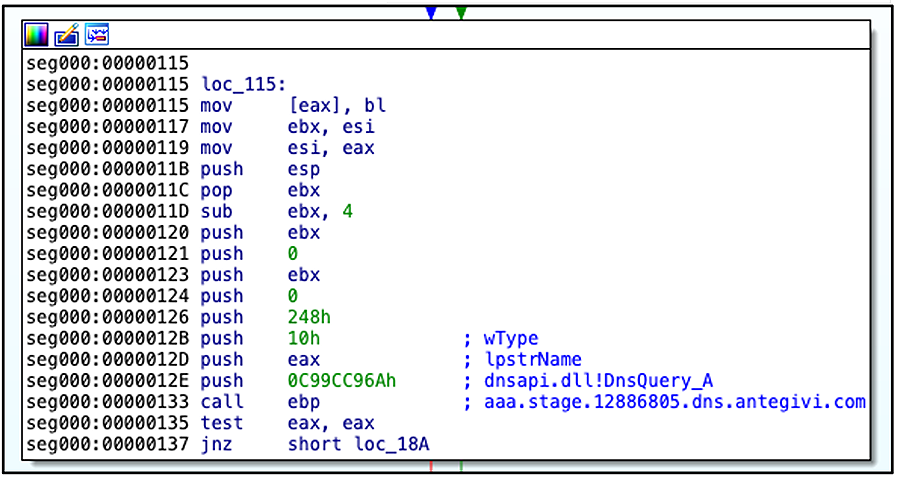
Cuba makes use of the now-widespread BYOVD (Carry Your Personal Weak Driver) approach to show off endpoint safety instruments. Additionally, it makes use of the ‘BurntCigar’ software to terminate kernel processes related to security merchandise.
Aside from the Veeam flaw that is comparatively current, Cuba additionally exploits CVE-2020-1472 (“Zerologon”), a vulnerability in Microsoft’s NetLogon protocol, which provides them privilege escalation in opposition to AD area controllers.
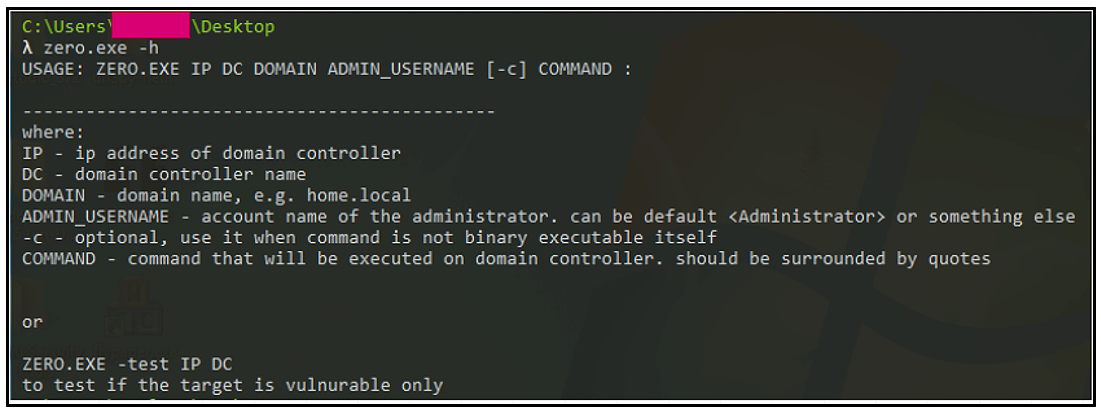
Within the post-exploitation part, Cuba was noticed utilizing Cobalt Strike beacons and numerous “lolbins.”
Cuba nonetheless very energetic
BlackBerry underlines the clear monetary motivation of the Cuba ransomware gang and mentions that the risk group is probably going Russian, one thing that has been hypothesized by different cyber-intelligence reviews up to now.
This assumption is predicated on the exclusion of computer systems that use a Russian keyboard format from infections, Russian 404 pages on components of its infrastructure, linguistic clues, and the group’s Western-focused focusing on.
In conclusion, Cuba ransomware stays an energetic risk roughly 4 years into its existence, which is not frequent in ransomware.
The inclusion of CVE-2023-27532 in Cuba’s focusing on scope makes the immediate set up of Veeam security updates extraordinarily necessary and as soon as once more highlights the chance of delaying updates when publicly accessible PoC (proof-of-concept) exploits can be found.




