A premium WordPress plugin named LayerSlider, utilized in over a million websites, is weak to unauthenticated SQL injection, requiring admins to prioritize making use of security updates for the plugin.
LayerSlider is a flexible software for creating responsive sliders, picture galleries, and animations on WordPress websites, permitting customers to construct visually interesting components with dynamic content material on on-line platforms.
Researcher AmrAwad found the vital (CVSS rating: 9.8) flaw, tracked as CVE-2024-2879, on March 25, 2024, and reported it to WordPress security agency Wordfence through its bug bounty program. For his accountable reporting, AmrAwad obtained a bounty of $5,500.
The flaw, which impacts variations 7.9.11 by means of 7.10.0 of the plugin, may enable attackers to extract delicate knowledge, equivalent to password hashes, from the positioning’s database, placing them susceptible to full takeover or data breaches.
Technical particulars offered in Wordfence’s report reveal that the vulnerability existed throughout the plugin’s ‘ls_get_popup_markup’ perform’s dealing with of the ‘id’ parameter.
This perform fails to sanitize the ‘id’ parameter correctly, permitting attackers to inject malicious SQL code into specifically crafted queries, leading to command execution.
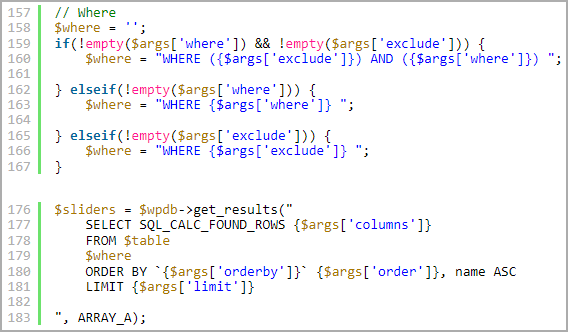
The construction of the potential queries limits the assault to time-based blind SQL injection, which means that the attackers want to watch the response occasions to deduce knowledge from the database.
Regardless of this limitation, CVE-2024-2879 nonetheless permits malicious actors to extract data from the positioning’s database with out requiring any authentication on the positioning, together with password hashes and delicate consumer data.
Wordfence explains that the difficulty is additional exacerbated as a result of the queries will not be ready utilizing WordPress’s ‘$wpdb->put together()’ perform, which prevents SQL injection by guaranteeing that consumer enter is sanitized earlier than being utilized in database queries.
The plugin’s creator, Kreatura Workforce, was instantly notified of the flaw and shortly acknowledged the report. The builders launched a security replace on March 27, 2024, lower than 48 hours after preliminary contact.
All customers of LayerSlider are advisable to improve to model 7.10.1, which addresses the vital vulnerability.
Generally, it’s important for WordPress web site admins to maintain all their plugins updated, disable those who aren’t wanted, use sturdy account passwords, and deactivate dormant accounts that may be hijacked.




