Attackers are actually focusing on a important authentication bypass vulnerability within the CrushFTP file switch software program utilizing exploits primarily based on publicly accessible proof-of-concept code.
The security vulnerability (CVE-2025-2825) was reported by Outpost24, and it permits distant attackers to achieve unauthenticated entry to gadgets working unpatched CrushFTP v10 or v11 software program.
“Please take quick motion to patch ASAP. The underside line of this vulnerability is that an uncovered HTTP(S) port may result in unauthenticated entry,” CrushFTP warned in an e mail despatched to prospects on Friday, March 21, when it launched patches to handle the security flaw.
As a workaround, admins who cannot instantly replace CrushFTP 10.8.4 and later or 11.3.1 and later can allow the DMZ (demilitarized zone) perimeter community possibility to guard their CrushFTP servers till they’ll patch.
Every week later, security risk monitoring platform Shadowserver warned that its honeypots detected dozens of exploitation makes an attempt focusing on Web-exposed CrushFTP servers, with over 1,500 susceptible situations uncovered on-line.
The warning comes days after ProjectDiscovery revealed a write-up containing CVE-2025-2825 technical particulars and a proof-of-concept exploit.
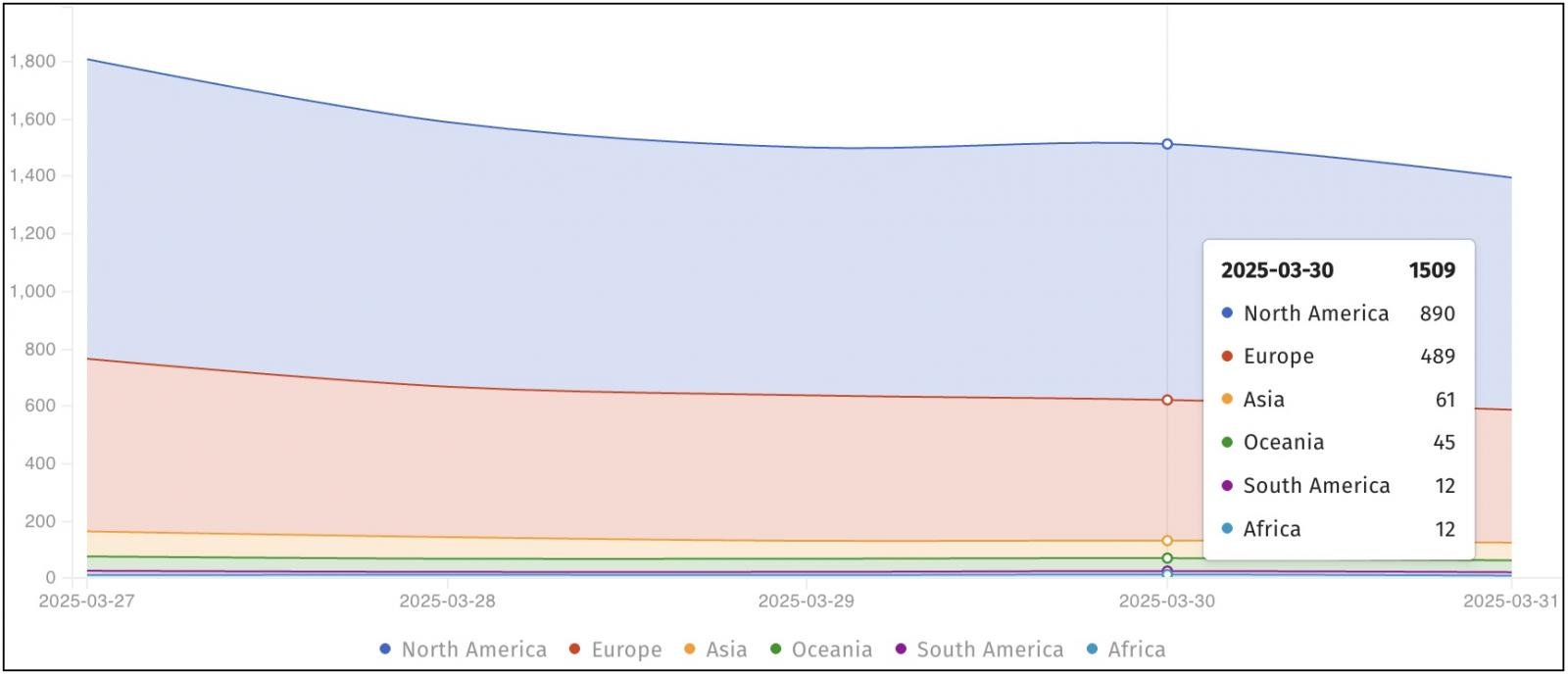
“We’re observing CrushFTP CVE-2025-2825 exploitation makes an attempt primarily based on publicly accessible PoC exploit code,” Shadowserver stated on Monday. “Nonetheless 1512 unpatched situations susceptible to CVE-2025-2825 seen on 2025-03-30.”
File switch merchandise equivalent to CrushFTP are excessive on ransomware gangs’ listing of targets, particularly Clop, which has been linked to knowledge theft assaults focusing on zero-day flaws in Accelion FTA, MOVEit Switch, GoAnywhere MFT, and, most lately, Cleo software program.
One yr in the past, in April 2024, CrushFTP patched an actively exploited zero-day vulnerability (tracked as CVE-2024-4040) that allow unauthenticated attackers escape the consumer’s digital file system (VFS) and obtain system information.
On the time, cybersecurity firm CrowdStrike discovered proof that the marketing campaign focusing on CrushFTP servers at a number of U.S. organizations was doubtless politically motivated and centered on intelligence-gathering.
The Cybersecurity and Infrastructure Safety Company (CISA) additionally added CVE-2024-4040 to its Recognized Exploited Vulnerabilities catalog, ordering federal businesses to safe susceptible methods on their networks inside per week.
CrushFTP prospects have been additionally warned to patch a important distant code execution bug (CVE-2023-43177) within the firm’s enterprise suite in November 2023 after Converge security researchers (who found and reported the flaw) launched a proof-of-concept exploit three months after security updates have been launched.

Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and the right way to defend towards them.




