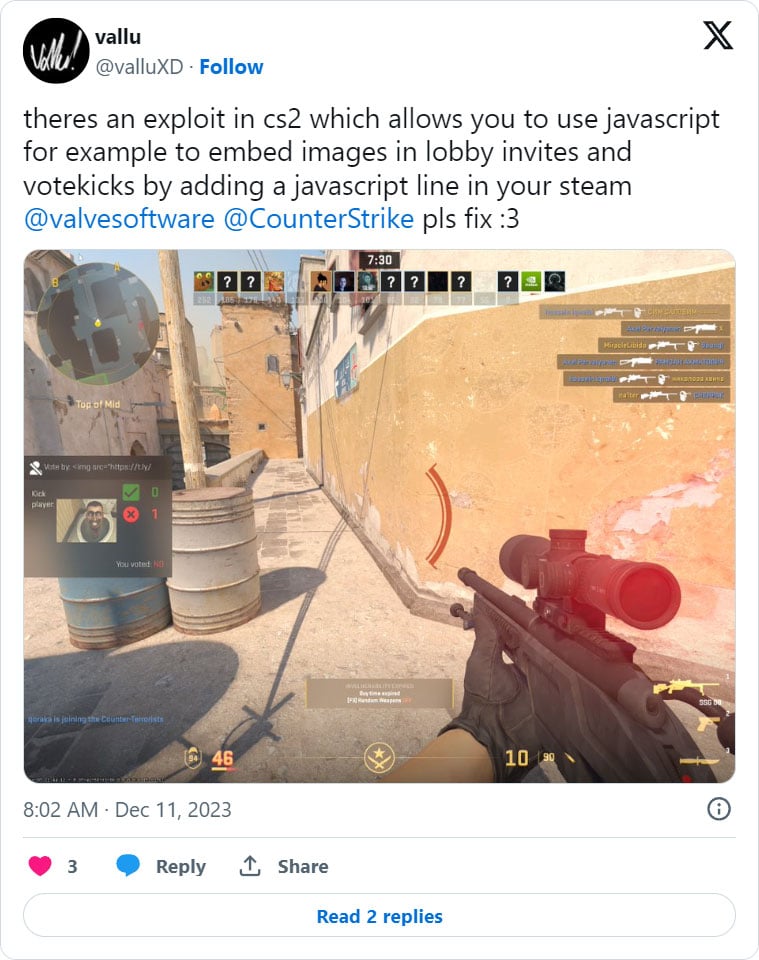
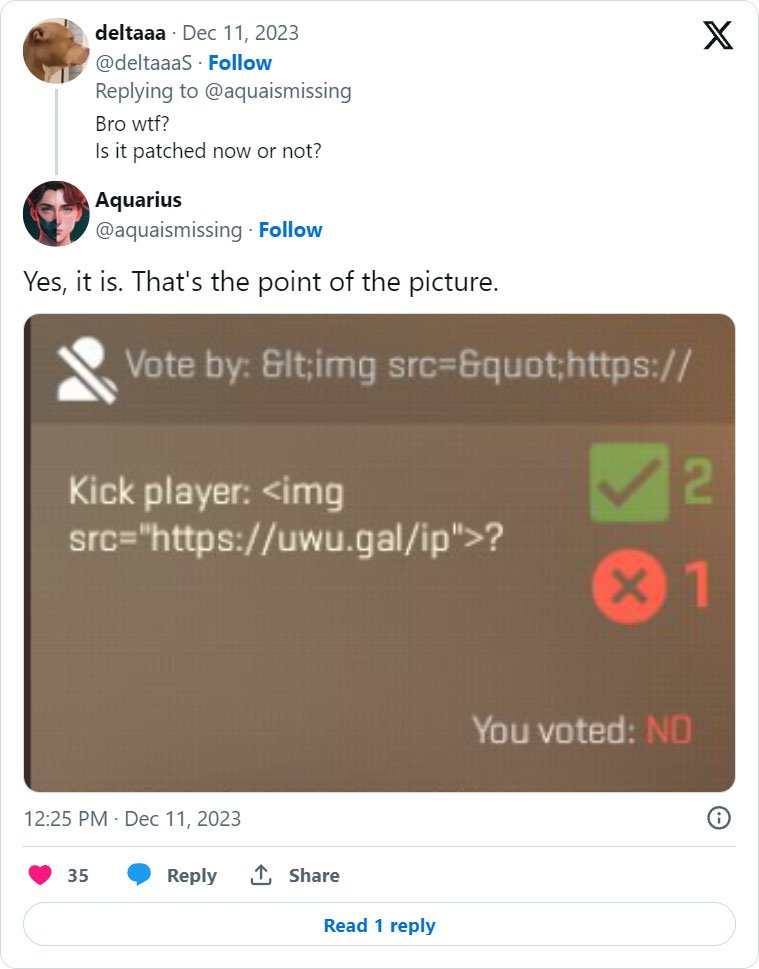
Valve has reportedly fastened an HTML injection flaw in Counter-Strike 2 that was closely abused at present to inject photos into video games and acquire different gamers’ IP addresses.
Whereas initially considered a extra extreme Cross Web site Scripting (XSS) flaw, which permits JavaScript code to be executed in a shopper, the bug was decided solely to be an HTML injection flaw, permitting the injection of photos.
Counter-Strike 2 makes use of Valve’s Panorama UI, a person interface that closely incorporates CSS, HTML, and JavaScript for design format.
As a part of the design format, builders can configure enter fields to just accept HTML quite than sanitize it to an everyday string. If the sphere enabled HTML, any inputted textual content can be rendered on output as HTML.
As we speak, Counter-Strike customers started reporting that customers have been abusing an HTML injection flaw to inject photos into the kick voting panel.
Whereas the flaw was abused largely for innocent enjoyable, others used it to acquire the IP addresses of different players within the match.
This was accomplished by utilizing the <img> tag to open a distant IP logger script that prompted the IP handle for each participant who noticed the vote kick to be logged.
These IP addresses could possibly be used maliciously, corresponding to launching DDoS assaults to power gamers to disconnect from the match.
This afternoon, Valve launched a small 7MB replace that reportedly fixes the vulnerability and causes any inputted HTML to be sanitized to an everyday string.
For instance, as soon as the patch is put in, as an alternative of injected HTML being rendered by the person interface, it could simply be displayed as a string, as demonstrated beneath.
BleepingComputer contacted Valve to substantiate if this replace fastened the exploit however has not acquired a response.
In 2019, an analogous, however extra severe, bug was discovered in Counter-Strike: World Offensive’s Panorama UI that allowed HTML to be injected by way of the kick function.
Nonetheless, in that exact case, it is also used to launch JavaScript, inflicting it to be a much more essential XSS vulnerability that could possibly be used to execute instructions remotely.