Quite a few industries—together with know-how, monetary companies, vitality, healthcare, and authorities—are speeding to include cloud-based and containerized net functions.
The advantages are plain; nevertheless, this shift presents new security challenges.
OPSWAT’s 2023 Internet Software Safety report reveals:
- 75% of organizations have modernized their infrastructure this 12 months.
- 78% have elevated their security budgets.
- But simply 2% are assured of their security posture.
Let’s discover why confidence in security lags infrastructure upgrades and the way OPSWAT closes that hole.
Evolving Infrastructure Outpaces Safety Upgrades.
The tempo of security upgrades struggles to maintain up with technological developments. This hole is particularly seen in file add security. Firms are updating their infrastructure by embracing distributed, scalable functions that leverage microservices and cloud options—creating new avenues of assault for criminals.
Cloud Internet hosting
Companies are transferring to public cloud internet hosting for its scalability and effectivity. Software program as a Service (SaaS) sees rising adoption whereas non-public cloud and on-site internet hosting wane. Data is unfold over a number of cloud storage suppliers. Sadly, this will increase complexity and opens extra assault vectors.
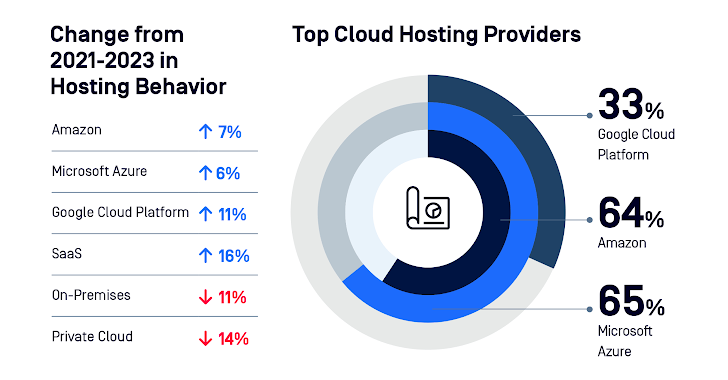 |
| Determine 1: Breakdown of cloud internet hosting suppliers |
Organizations are Shifting to Containers
97% of organizations use containers or will deploy containers over 12 months of their webhosting environments. Azure Kubernetes, AWS Kubernetes, and Docker are prime decisions. Misconfiguration and elevated updates required for microservices open the door for file add assaults leveraging weak and outdated parts.
Unsecure File Uploads Concern
Our survey highlights three main issues:
Data Breaches
Data breaches are the #1 concern. Reputational injury, loss in enterprise or income and regulatory fines, spherical out the checklist. Cybercriminals can entry delicate information, resulting in monetary losses, regulatory fines, and reputational injury.
Compliance
Normal Data Safety Regulation (GDPR) leads the way in which with the best share of respondents. 56% of corporations state that it was a driving issue of their security selections.
Malware
98% of respondents are involved about malware assaults from file uploads.
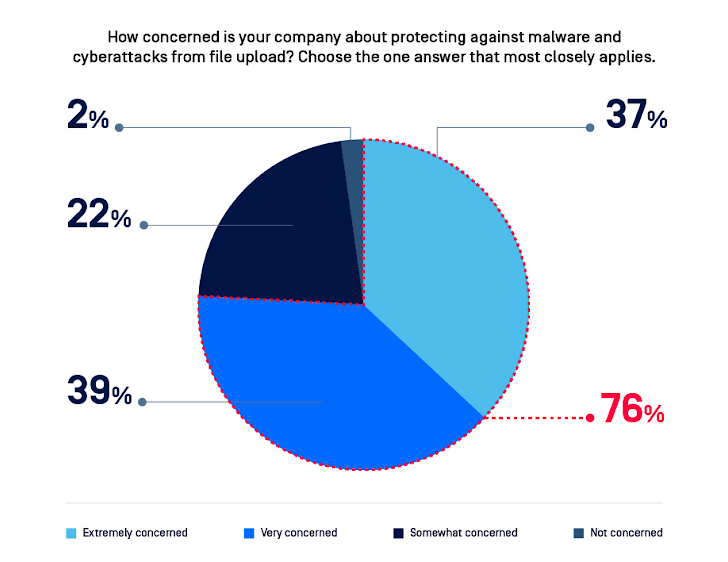 |
| Determine 2: Three quarters (76%) are “extraordinarily” or “very involved” about defending towards assaults. |
Click on right here to schedule a 15-minute demo of how OPSWAT may also help safe your net functions from malicious file uploads.
File Add Safety Wants Fixing
As organizations proceed to shift their operations to cloud internet hosting and containerized net functions, the necessity for efficient security measures has develop into much more crucial. That is very true when accepting file uploads, as cybercriminals exploit file add vulnerabilities to entry safe networks.
We discovered that:
- Solely 63% use multi-engine scans for malware.
- Simply 32% disarm recordsdata through Content material Disarm and Reconstruction (CDR) to deal with zero-day and embedded threats.
- Using a number of anti-malware engines is significant. Scanning with over 30 engines hit a 99%+ accuracy price.
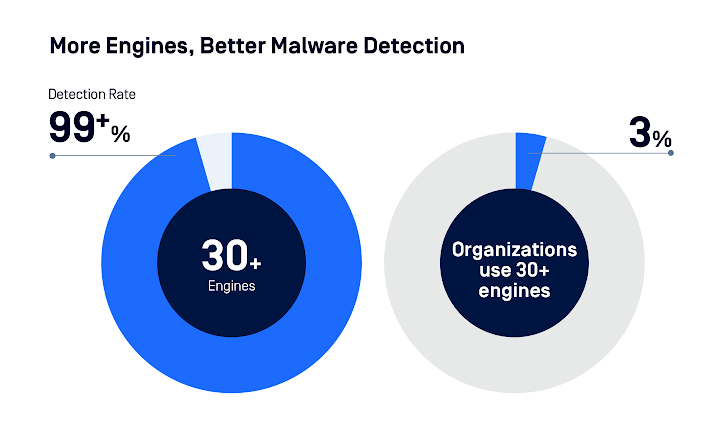 |
| Determine 3: Anti-malware scanning efficacy. |
The Path Ahead
To maintain tempo with evolving infrastructure and elevated assault floor, corporations want an built-in answer using prevention- and detection-based applied sciences.
Extra Antivirus Engines
Utilizing a number of antivirus (AV) engines to safe towards malicious file uploads and malware can present extra layers of safety and improve the detection price. Every antivirus engine has its personal algorithm and algorithms for detecting a variety of threats.
Deep CDR Disarms Lively Content material & Regenerates Secure Information
Our survey discovered that giant corporations take away potential threats from recordsdata with Deep CDR to disarm energetic content material and regenerate secure recordsdata whereas alerting and blocking out-of-policy recordsdata with embedded objects, resembling JavaScript in PDFs or macros.
 |
| Determine 4: CDR file regeneration course of |
One-Billion Data Factors
It is crucial to maintain net functions vulnerability-free. It is extremely beneficial that organizations implement File-Primarily based Vulnerability Evaluation know-how to detect utility and file-based vulnerabilities earlier than set up, closing any future backdoors that hackers may exploit. We use our patented know-how (U.S. 9749349 B1) to evaluate vulnerabilities collected from over one billion information factors from in-the-wild units and customers.
AI-Enabled Malware Evaluation
OPSWAT Filescan performs quick adaptive risk evaluation on recordsdata to detect zero-day malware and shortly discover Indicators of Compromise (IOCS) from varied sources, together with recordsdata and URLs. It makes use of fuzzy hashing and similarity scores powered by machine studying to carry out in-depth evaluation.
Conclusion
As net utility infrastructure progresses to the cloud, the assault floor grows. OPSWAT MetaDefender is the appropriate path ahead to protect towards malicious file uploads and information loss. You possibly can maintain tempo with the evolving risk panorama by combining key file add security applied sciences that seamlessly combine along with your present infrastructure.
Able to get a demo of our file add security answer? Attain out to considered one of our security specialists as we speak.
Need extra insights from the 2023 Internet Software Safety Report. Get it right here.




