There’s a appreciable amount of underground posts discussing insiders for performing SIM swaps. Within the picture under an actor in search of an insider at a Verizon retailer to carry out SIM swapping.
Cybersixgill
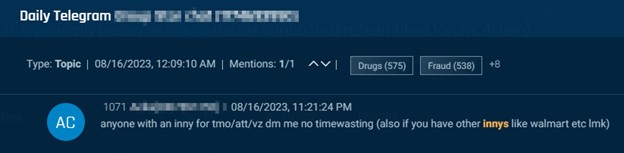
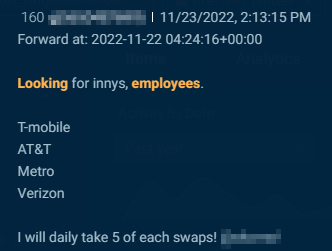
Telegram is the preferred venue for actors to hunt telecom insiders, additionally known as innys. Within the examples under, menace actors search SIM swaps via insiders at organizations together with T-Cellular, AT&T, Metro and Verizon.
Cybersixgill
Cybersixgill
Cybersixgill
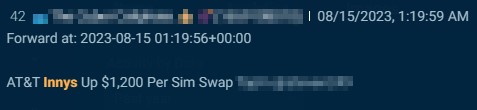
Sometimes, the submit’s creator will even state how a lot they may pay for swaps, reminiscent of this creator (under), who gives $1,200 apiece.
Cybersixgill
This actor, who expenses $2,000 per swap, gives proof of working with an insider, together with a screenshot of AT&T’s worker portal and DMs with the insider.
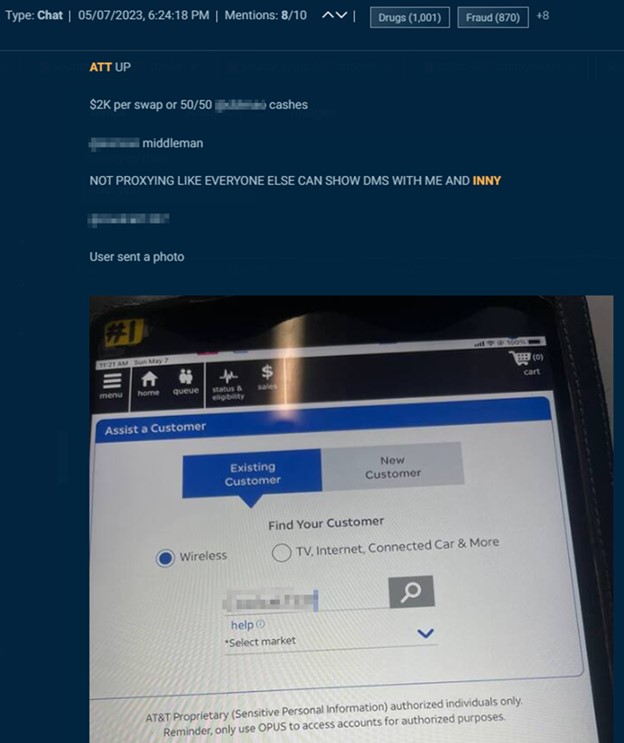
Cybersixgill
Along with SIM swapping, underground actors additionally search telecom insiders for credentials, buyer knowledge, and normal info. Within the photos under you’ll first see an actor on an underground discussion board in search of Vodafone insiders to offer buyer knowledge. Then an actor seeks telecom insiders in Russia, Ukraine, Kazakhstan, Belarus, and Uzbekistan. Folowed by an actor that seeks a Claro Colombia worker to reply some questions.
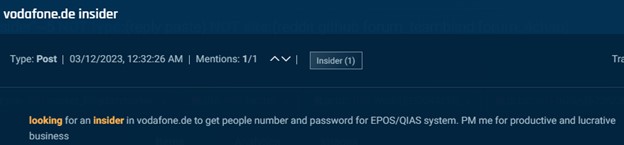
Cybersixgill
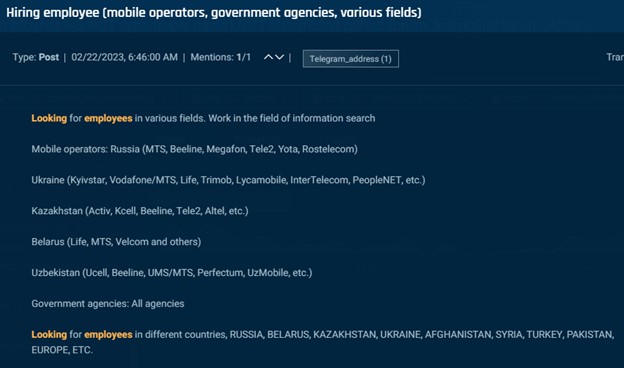
Cybersixgill
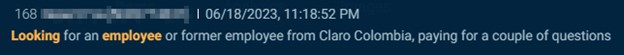
Cybersixgill
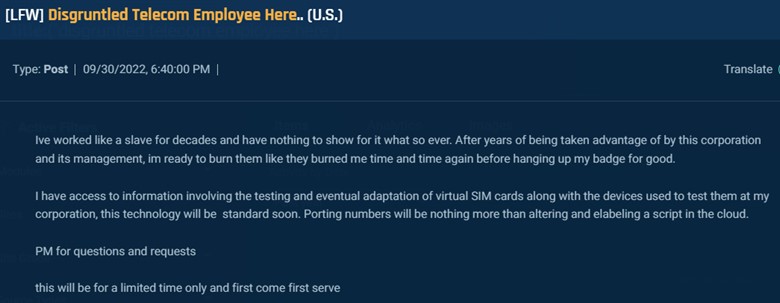
Typically we discover insiders reaching out. For instance, this self-described “disgruntled telecom worker” is providing to promote info concerning eSIMs, which can allow porting numbers with nothing greater than working “a script within the cloud.”
Cybersixgill
Insider Threats: Retail Sector
Underground menace actors sometimes search retail insiders to obtain items without cost. One widespread scheme through which they will contain insiders is refund fraud, also referred to as refunding, through which an actor claims undeserved refunds for a product.
There are a lot of methods to hold out this sort of assault, together with reporting that an empty field or broken merchandise arrived or returning an empty field. Nonetheless, most strategies require convincing an worker to just accept the story; it’s simpler to hold out a faux return if they’re already a prepared confederate.
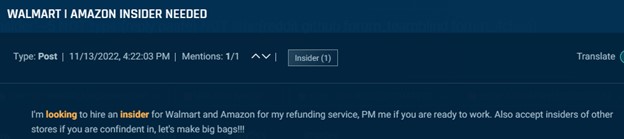
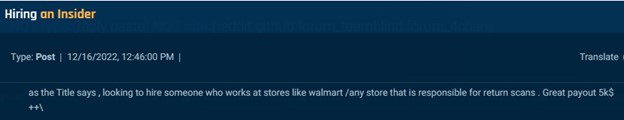
Some menace actors state fairly plainly that they’re in search of insiders for refund scams. Within the examples under, one actor gives $5,000 for an insider accountable for returns at Walmart or some other retailer, whereas one other gives an undisclosed sum to insiders who work with them.
Cybersixgill
Cybersixgill
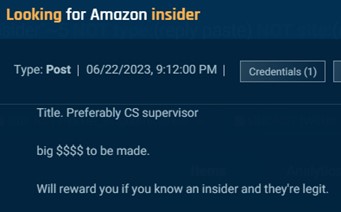
Different actors aren’t as express about wanting an insider to help with refund scams. For instance, the actor within the submit under sought an Amazon insider, ideally a buyer assist supervisor. Somebody on this position would be capable of authorize returns.
Cybersixgill
Menace actors additionally recruit insiders in e-commerce. For instance, this actor seeks eBay insiders who can unblock suspended accounts.
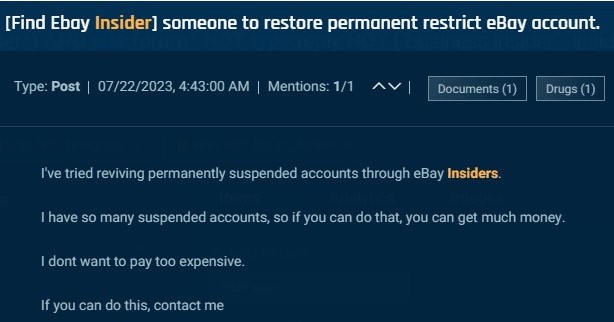
Cybersixgill
One other actor persistently sought insiders at lego.com to offer details about orders, posting eight occasions in two months.
Nonetheless, in lots of postings, there are few, if any, clues about why an insider is requested, although we could presume that they’re associated to theft. One actor seeks an Amazon warehouse employee; one other seeks an Amazon India worker who can help with bulk orders, and one other seeks associates at a protracted and diversified record of corporations to assist with “buyer lookups,” to offer delicate and confidential buyer knowledge.
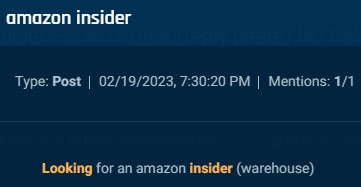
Cybersixgill
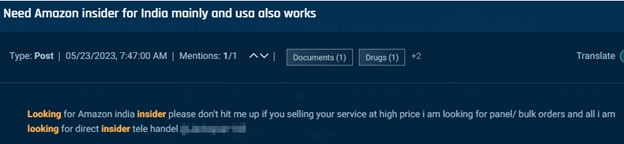
Cybersixgill
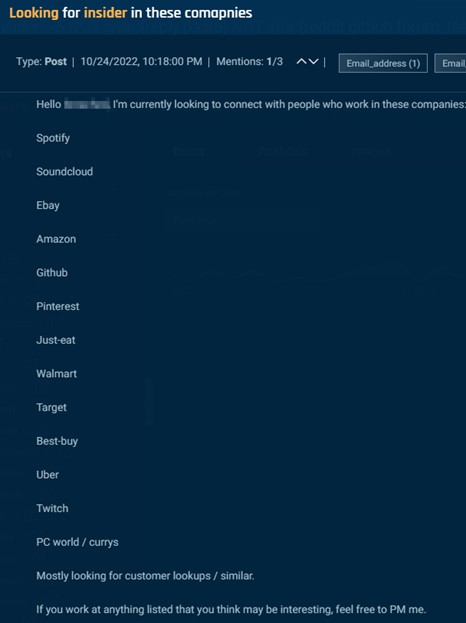
Cybersixgill
Insider Threats: Transport and logistics
Underground menace actors recruit insiders in delivery and logistics primarily to execute fraudulent monitoring scans. Similar to within the instance under the place an actor seeks an insider at UPS and different couriers to carry out scans.
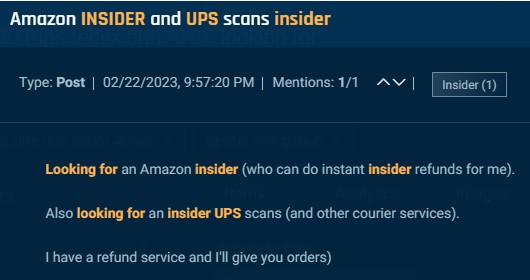
Cybersixgill
Insider scans are one other method in refund scams. On this scheme, an actor requests to return an merchandise to an e-commerce retailer. An confederate within the delivery firm scans the delivery label, confirming to the retailer that the merchandise is in transit. The retailer points a refund however by no means receives the bundle. Fraudsters can even use insider scans and courier insiders to easily “ship” a bundle that disappears, permitting them to say insurance coverage for his or her losses.
The examples under present how malicious actors go about performing these scams. In a single picture an actor in search of insider scans at UPS, DHL, and different carriers to help with refund scams and within the following an actor on the lookout for staff at UPS, FedEx, USPS or different couriers.
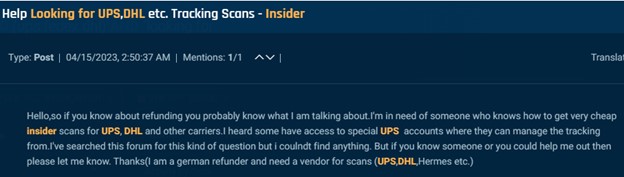
Cybersixgill
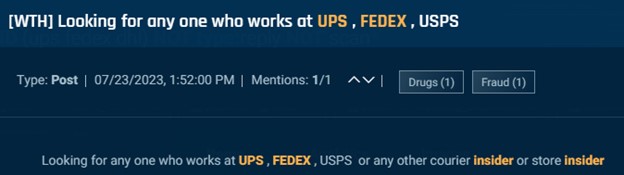
Cybersixgill
Many posts recruiting courier insiders, reminiscent of the instance under, supply “massive cash” to malicious staff.
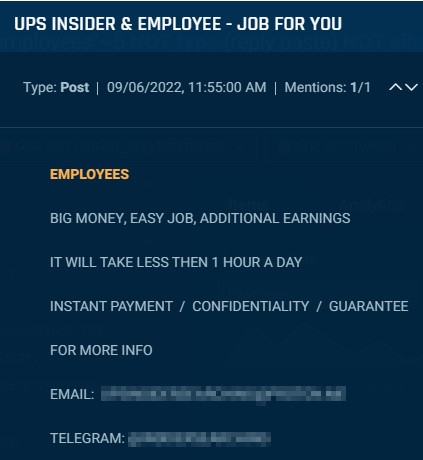
Cybersixgill
Others supply insider scans as a service such because the submit under, requesting $60 per scan at FedEx, UPS, Royal Mail, and different couriers.
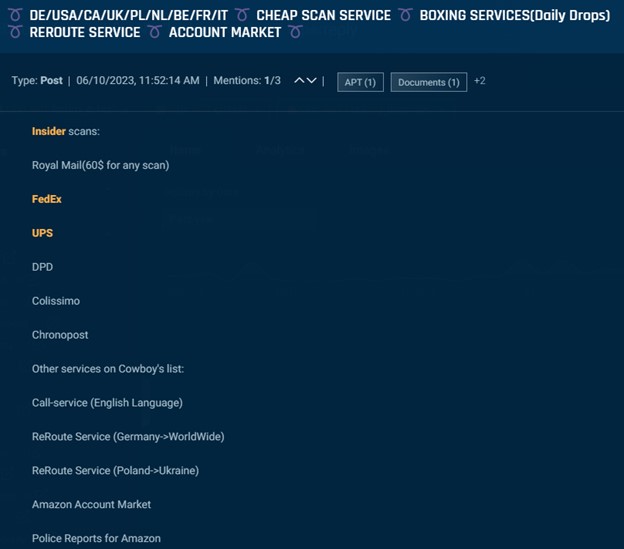
Cybersixgill
Insider Threats: Social media
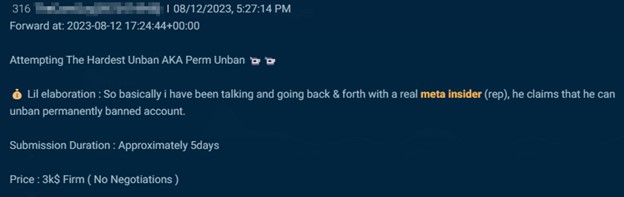
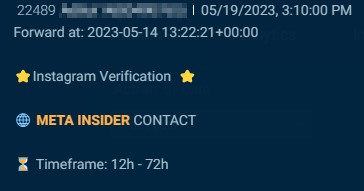
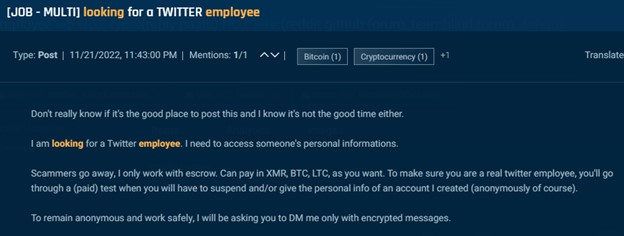
Menace actors goal insiders at social media corporations to ban, un-ban and entry buyer knowledge. The examples under present how one actor on Telegram claimed to be “paying good” for somebody at Instagram or X (previously Twitter), and one other provided “$$$$$$” for somebody at Snapchat.
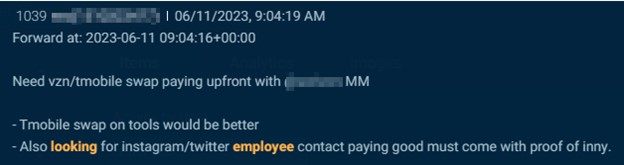
Cybersixgill
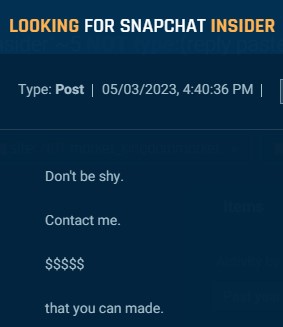
Cybersixgill
If the submit specifies the perform of the specified insider, it usually has to do with banning, unbanning, or verifying accounts. Along with this, actors additionally search social media staff to offer a person’s private info.
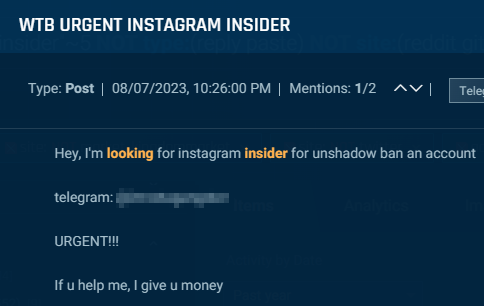
Cybersixgill
Cybersixgill
Cybersixgill
Cybersixgill
Insider Threats: Monetary providers
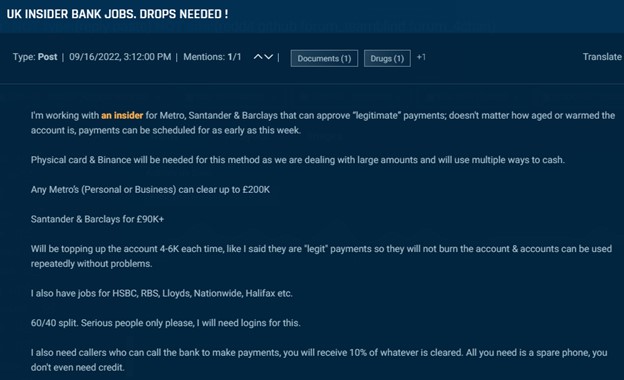
An insider at a financial institution or different monetary providers firm is perhaps the required hyperlink to execute a big, fraudulent scheme. Underground actors use insiders at banks to approve funds and cash transfers, enabling fraudsters to maneuver and launder cash. Within the subsequent instance, an actor claims to have an insider at Metro, Santander, and Barclays that may approve funds of as much as GBP90,000-GBP200,000 (relying on the financial institution). The actor notes that these funds seem reliable and don’t burn the account.
Cybersixgill
On this subsequent instance, an actor claims to have a Financial institution of America insider onboard. The actor is in search of account and routing info, in addition to cell phone numbers, in an effort to perform their scheme.

Cybersixgill
Insiders additionally allegedly help with “loading,” an exercise involving shifting cash to an account within the actor’s management.
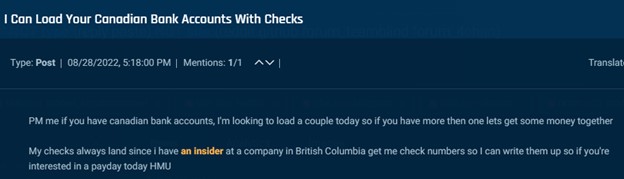
Cybersixgill
Equally, actors search to make use of insiders for cash conversions. The instance under is from an actor anticipating to obtain $10,000-$30,000 every day from a “challenge” and seeks a PayPal worker to transform it into cryptocurrency.
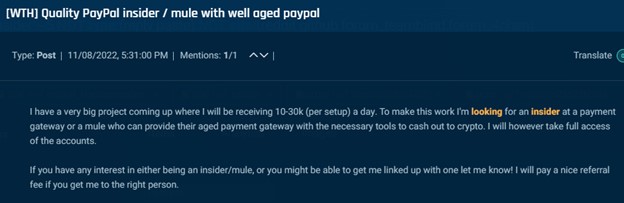
Cybersixgill
Actors additionally search financial institution insiders with entry to the SWITCH software server.

Cybersixgill
On this subsequent submit, the actor even notes that they search to deploy the FASTCASH malware. FASTCASH malware can be utilized to trigger ATMs to eject their money, and it was initially recognized with Hidden Cobra, a North Korean superior persistent menace (APT). Whether or not these posts’ authors have any connection to the group is unsure, nonetheless, in the event that they achieve getting access to the SWITCH software server, they stand to generate very vital money payouts.
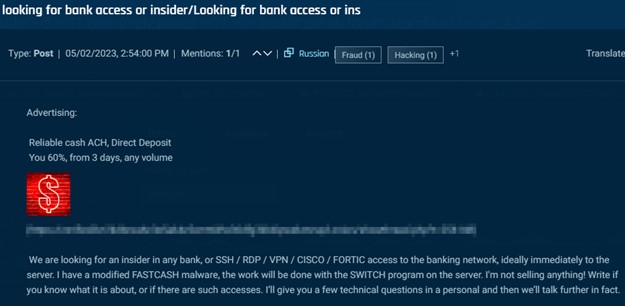
Cybersixgill
Insider Threats: Authorities and army
Transcending from cybercrime to espionage, we found a number of posts through which actors solicited governmental or government-affiliated insiders to offer info. This consists of people, like within the picture under, who can present nationwide citizen databases to help in doxing. An actor in search of an insider within the French authorities to offer citizen knowledge.
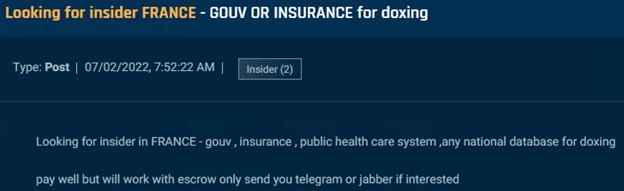
Cybersixgill
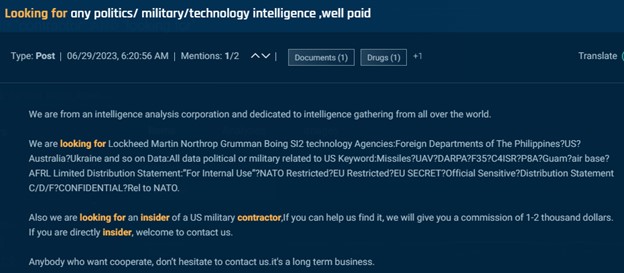
Different posts search people who can present labeled info. For instance, this subsequent submit appeared a number of occasions throughout a number of boards and Telegram from a self-described “intelligence evaluation company” providing $1,000-$2,000 as a finders price for somebody that may join them with an insider at a US army contractor.
Cybersixgill
Lastly, we additionally found the under submit through which a person presupposed to promote sixteen units of labeled authorities knowledge, together with proprietary knowledge belonging to protection producers reminiscent of Raytheon and Elbit. The submit additionally lists a secret doc a couple of confidential 5 Eyes army train for $300, noting that it was obtained by an insider.

Cybersixgill
We should emphasize that posts soliciting insiders to offer labeled info are uncommon. The penalties for such actions are extreme, and many of the darkish internet’s customers are financially motivated. Even so, it’s not unparalleled for an insider to leak labeled info on the deep and darkish internet; most lately, a Massachusetts Nationwide Guardsman has been charged with posting labeled paperwork on a Discord server.
Defending Towards Insider Threats
Workers can pose a novel kind of menace to a corporation. Most staff aren’t malicious, they usually should be trusted with entry to the information and techniques wanted for performing their duties. Nonetheless, those that are lured by a wide range of strategies to make use of their positions to help in prison enterprises could cause vital monetary and reputational harm to their employers.
In line with the 2023 Verizon Data Breach Investigations Report, malicious insiders perpetrate about 19% of identified data breaches. Whereas there isn’t any means of understanding for certain what number of of those assaults originated from a partnership cast on the deep and darkish internet, there are a number of practices that corporations can take to guard themselves.
- Principal of least privilege: Worker privileges must be restricted solely to what their duties require.
- Job rotation: Common biking of staff between duties to disclose fraudulent exercise.
- A number of signoff: Execution of delicate actions ought to require a number of staff to approve.
- VIP account safety: Clients with delicate accounts or who usually tend to be focused ought to be capable of opt-in to extra stringent account safety.
- Worker consciousness: Workers ought to perceive that menace actors search to recruit their friends and perpetrate fraud. In the event that they see one thing suspicious, they need to report it.
- Automated detection: Use of software program to flag suspicious actions.
- Underground monitoring: Organizations should perceive adversarial efforts to recruit insiders. Actual-time cyber menace intelligence from the clear, deep, and darkish internet is important to assemble the data wanted to reveal organizational danger from insider threats.
A rogue worker can severely impression a enterprise’s operations, funds, community security, and model. They’re excess of simply an “IT drawback” or perhaps a “security workforce drawback.” A correct organizational protection requires coordination between technical and non-technical gamers, from the SOC to HR, in an effort to preserve the corporate safe.
Organizations should determine which of their staff are in roles that is perhaps focused for recruitment by cybercriminals, and implement stringent monitoring and controls to neutralize any threats from contained in the constructing.




