Cisco is warning of 5 new Catalyst SD-WAN Supervisor merchandise vulnerabilities with essentially the most vital permitting unauthenticated distant entry to the server.
Cisco Catalyst SD-WAN Supervisor for WAN is community administration software program permitting admins to visualise, deploy, and handle units on extensive space networks (WAN).
Probably the most extreme of the disclosed flaws impacting the product is CVE-2023-20252 (CVSS v3.1: 9.8), which permits unauthorized entry attributable to points with the Safety Assertion Markup Language (SAML) APIs.
“A vulnerability within the Safety Assertion Markup Language (SAML) APIs of Cisco Catalyst SD-WAN Supervisor may enable an unauthenticated, distant attacker to achieve unauthorized entry to the applying as an arbitrary person,” warns the security bulletin.
The flaw will be leveraged by sending specifically crafted requests on to the SAML APIs, which generate arbitrary authorization tokens that enable unconditional entry to the applying.
Exploitation of CVE-2023-20252 has the potential for person impersonation, unauthorized knowledge entry/modification/deletion, and repair disruption.
The remaining 4 vulnerabilities are much less extreme:
- CVE-2023-20253 (CVSS v3.1: 8.4): Unauthorized configuration rollback attributable to CLI vulnerabilities.
- CVE-2023-20034 (CVSS v3.1: 7.5): Info disclosure vulnerability in Elasticsearch entry management.
- CVE-2023-20254 (CVSS v3.1: 7.2): Authorization bypass within the session administration system. (requires multi-tenant characteristic enabled)
- CVE-2023-20262 (CVSS v3.1: 5.3): DoS vulnerability within the SSH service. (impacts SSH entry solely)
It’s price noting that CVE-2023-20034 can also be remotely exploitable with out requiring authentication. Nevertheless, its severity is mitigated by the truth that entry is proscribed to the Elasticsearch database with the privileges of the Elasticsearch person.
The 5 flaws impression numerous variations of Cisco Catalyst SD-WAN Supervisor, with extra particulars on the impacted and goal improve variations under:
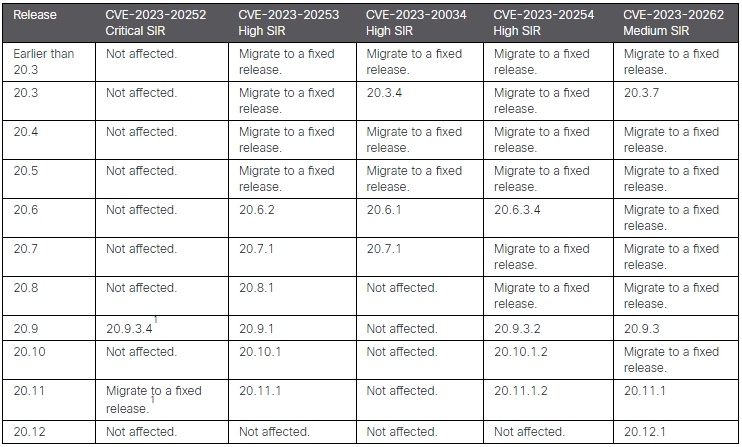
CVE-2023-20252, which is essentially the most pressing to repair, impacts releases 20.9.3.2 and 20.11.1.2 however doesn’t have an effect on older releases within the 20.9 and 20.11 branches.
Catalyst SD-WAN Supervisor model 20.12, the newest out there launch, isn’t impacted by any flaws aside from the medium severity one (fastened in 20.12.1), so that is the most secure model to improve to if doable.
Cisco has shared no workarounds for the fastened flaws this time, so the one advisable motion is upgrading to a patched launch.
The seller clarifies that IOS XE Software program, SD-WAN cEdge Routers, and SD-WAN vEdge Routers usually are not weak.
Not one of the flaws are reported as actively exploited, but upgrading to the advisable variations ought to be handled with urgency.




