Belief lies on the coronary heart of each relationship, transaction, and encounter. But in our on-line world—the place we work, reside, study, and play—belief can grow to be elusive.
Because the daybreak of the web almost 50 years in the past, we’ve witnessed unbelievable digital transformations paired with more and more formidable threats. Figuring out who and what to belief has grow to be so tough that the very notion of belief has been flipped on its head. This new philosophy of “by no means belief, at all times confirm” is broadly accepted, but implementing zero belief successfully throughout expertise infrastructure, associate ecosystems, and even day by day digital interactions can nonetheless be difficult.
I lately had the honour of discussing belief in our on-line world with a gaggle of world expertise leaders as a part of CyberArk’s 10-year celebration as a public firm at Nasdaq. Following are highlights from our wide-ranging dialog, together with some key issues for constructing an anti-fragile digital ecosystem.
‘Belief is inbuilt drops and misplaced in buckets’
I can’t take credit score for this quote—it belongs to Kevin Plank, founding father of Underneath Armor—nevertheless it’s one among my favorites. As CIO at CyberArk, constructing belief internally and externally is integral to my job. Actually, forging belief is THE most important a part of any software program supplier’s job. And because the world turns into more and more interdependent, this additionally turns into probably the most difficult half.
Nearly each group depends on third-party services and products—and for good purpose. SaaS makes groups extra environment friendly and efficient and might strengthen security. Cloud platforms gas innovation by reducing limitations to entry and eliminating back-end IT infrastructure complications. In the meantime, generative AI (genAI) has ushered in an thrilling new wave of productiveness, high quality and creativity.
With any expertise disruption comes threat, and threat cascades downhill. In keeping with analysis from information science agency Cyentia Institute, the typical group does enterprise with 11 third events, and 98% of organizations do enterprise with a 3rd occasion that has suffered a breach. These numbers and related dangers shortly balloon when fourth-party relationships enter the image: The typical agency has oblique relationships with 200 fourth events which have been breached.
A compromise on one occasion can result in a compromise on all. Take into account the current assaults focusing on cloud storage agency Snowflake clients, which snowballed into an enormous international breach.
But the notion of trustworthiness goes past cybersecurity. More and more, the narrative is shifting to resilience. The July 2024 CrowdStrike incident—through which a corrupt replace file crashed tens of millions of Home windows-based machines worldwide—highlighted an inherent belief hole in at this time’s interdependent our on-line world structure. Although the web’s early founders took decentralization precautions to keep away from such catastrophic occasions, we’ve reached some extent at this time the place some important single factors of failure jeopardize its resilience.
Bridging the belief hole
On this setting, organizations should depend on companions who can exhibit their potential to uphold service availability necessities, safe environments, and defend information. Constructing trusted vendor partnerships begins with a stable technique and guardrails for good decision-making, reminiscent of certifications (i.e., ISO and SOC2), frameworks (i.e., SBOM), third-party threat scoring mechanisms, clear contract phrases and circumstances, and lots of different points (i.e., MFA, information at relaxation encryption and patch administration necessities).
As genAI use surges, organizations are more and more targeted on methods to grasp and govern the AI-based instruments of their third-party distributors. Whereas frameworks are evolving, probably the most essential consideration—at the very least for now—is that the shopper group’s information is secure. Some crucial inquiries to ask potential companions embrace:
- What steps does the seller take—together with utilizing genAI—to enhance product resilience and security?
- Does the seller comply with privateness greatest practices? For example, can clients decide out of sure options to make sure their information stays theirs?
- Are vendor workers required to make use of MFA and different identification security mechanisms to entry buyer information?
Constructing belief with third-party distributors should be balanced with constructing inside resilience to organize for an inevitable black swan occasion. By embracing an “assume breach” mindset and repeatedly stress-testing contingency plans and processes, groups will likely be higher ready to reply and prevail.
Making certain a resilient our on-line world for our future
Bridging the belief hole to make sure a resilient our on-line world for all requires collaboration on many fronts—starting with stronger public-private partnerships. Current strides made by the U.S. CISA, NSA, Cyber Command, and a number of other main tech companies to share menace intelligence, mitigate assaults, and promote safe by design practices are very encouraging. The behind-the-scenes collaboration to defend the U.S. 2024 election is a superb instance. In an unprecedented yr marked by AI-based deep fakes and misinformation campaigns, these partnerships are essential for defending democracy and preserving trendy infrastructure.
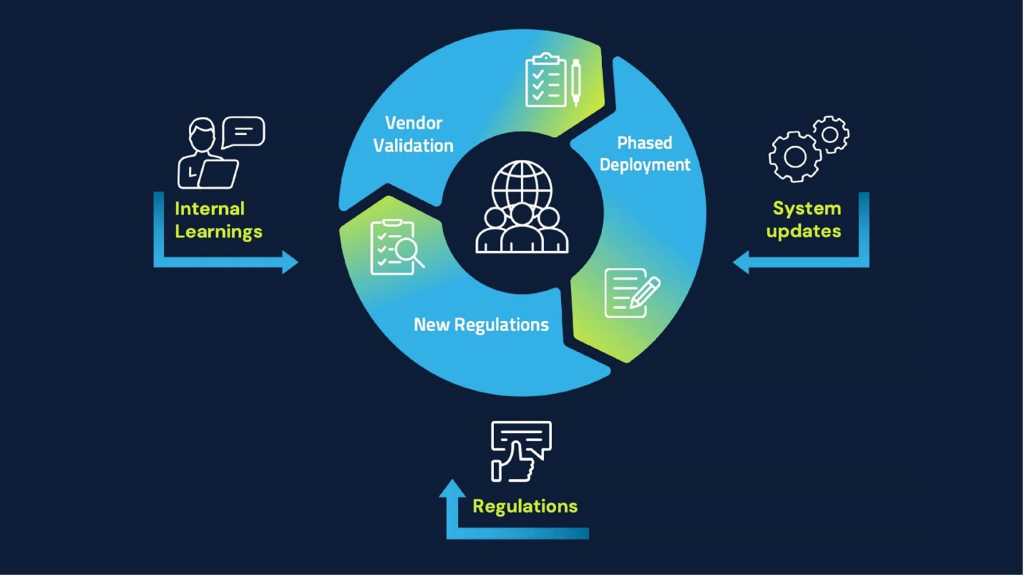
Constructing on these resilience efforts is what I name the Resolution Hygiene Framework, one other mechanism that organizations can make the most of in their very own cyber resilience journeys.
CyberArk
This three-pronged framework consists of:
- Vendor validation that maps the group’s full vendor ecosystem and figuring out crucial ones. It’s necessary to determine an annual cadence (at minimal) for evaluating distributors to establish any modifications, each good (reminiscent of a brand new certification with a greater restoration time goal that helps its availability) and dangerous (reminiscent of a current breach).
- Steady regulation assessments as a result of laws—from new AI acts to GDPR updates to MITRE framework modifications to new NIST requirements for post-quantum encryption—are continuously evolving.
- System updates that occur over time in a phased sequence because the world continues to vary and new classes are continuously realized. Our digital panorama is outlined by new assault strategies, applied sciences, identities and laws, and solely by means of considerate, risk-prioritized updates can organizations construct actually resilient digital infrastructures.
It begins and ends with belief
Belief is important to enterprise resilience and success. If we lose it, the web will stop to be a strong device for good. But when we protect it, we will unleash infinite prospects.
I’m optimistic that we will understand a brighter digital future collectively by specializing in belief—constructing it drop by drop, sustaining it, evaluating it, and repeatedly investing in it.
Further content material from Omer is out there on CyberArk’s Safety Issues | CIO Connections web page.




