British public sale home Christie’s is notifying people whose information was stolen by the RansomHub ransomware gang in a current community breach.
Christie’s found that it was the sufferer of a security breach that affected a few of its programs on Could 9, 2024. After turning into conscious of the occasion, Christie’s took measures to safe its community and employed exterior cybersecurity consultants to assist examine the incident’s affect.
The public sale home says it additionally notified regulation enforcement and is now working to help their investigation.
Whereas analyzing the breach, Christie’s discovered {that a} risk actor who breached its programs accessed and extracted buyer information between Could 8 and Could 9.
Following the investigation, Christie’s reviewed the accessed information to establish people whose info could have been affected, get hold of their contact info, and alert them of the incident after finishing the overview on Could 30.
The data breach notification letters despatched to affected people state that the public sale home is “not conscious of any makes an attempt to misuse your info on account of this incident.”
“We took extra steps to safe our programs and proceed to judge technical and organizational measures to keep away from the reoccurrence of an analogous incident,” Christie’s added [PDF].
The public sale home can be providing impacted individuals a free twelve-month subscription for the CyEx Id Protection Whole id theft and fraud monitoring service, which can alert them of modifications to their Experian, Equifax, and TransUnion credit score information to identify any doubtlessly fraudulent exercise on their credit score studies.
Claimed by RansomHub
Whereas Christie’s did not identify the attackers behind the Could breach, the RansomHub gang added the public sale home to its darkish internet leak portal, claiming it had breached its programs and stolen delicate shopper information.
The cybercriminals claimed to have exfiltrated the total names, addresses, ID doc particulars, and varied different delicate private info of at the least 500,000 Christie’s shoppers.
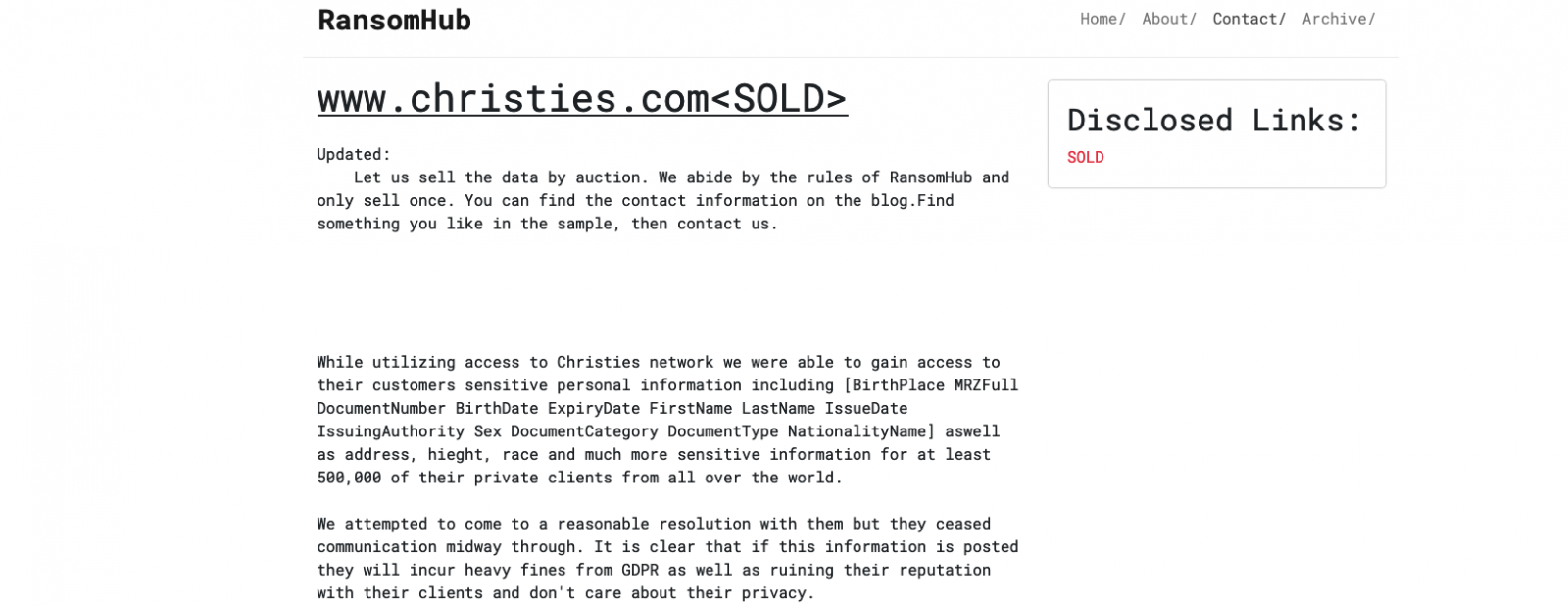
RansomHub has since up to date the Christie’s entry, saying they’ve bought the stolen information on their very own public sale platform. BleepingComputer could not independently confirm the risk actors’ claims that they bought the info.
The day the extortion hub claimed the Christie’s breach, a spokesperson advised BleepingComputer that attackers had breached the corporate’s community and stole a restricted quantity of private information belonging to a few of its shoppers.
Nevertheless, BleepingComputer was additionally advised that the corporate discovered no proof that any monetary or transactional information have been compromised through the incident.
RansomHub is a comparatively new operation that calls for ransom fee from victims in alternate for not leaking information stolen throughout assaults. If negotiations fail, it typically auctions the stolen information solely to the very best bidder.
Whereas the ransomware gang was recognized as a possible purchaser of Knight ransomware supply code, they rarely encrypt information throughout their assaults, focusing as a substitute on data-theft-based extortion.
Lately, RansomHub claimed the breach of main U.S. telecom supplier Frontier Communications, which needed to shut down its programs in April to include a cyberattack. The corporate warned 750,000 prospects this week that their info was uncovered in a data breach.




