Net Utility Safety consists of a myriad of security controls that guarantee that an online software:
- Capabilities as anticipated.
- Can’t be exploited to function out of bounds.
- Can’t provoke operations that it’s not speculated to do.
Net Purposes have change into ubiquitous after the growth of Net 2.0, which Social Media Platforms, E-Commerce web sites, and e mail shoppers saturating the web areas in recent times.
Because the purposes eat and retailer much more delicate and complete knowledge, they change into an ever extra interesting goal for attackers.
Frequent Attack Strategies
The three most typical vulnerabilities that exist on this area are Injections (SQL, Distant Code), Cryptographic Failures (beforehand delicate knowledge publicity), and Damaged Entry Management (BAC). Immediately, we are going to deal with Injections and Damaged Entry Management.
Injections
SQL is the commonest Database software program that’s used, and hosts a plethora of fee knowledge, PII knowledge, and inner enterprise information.
A SQL Injection is an assault that makes use of malicious SQL code for backend database manipulation to entry info that was not meant to be displayed.
The start line for this, is a command such because the one beneath:

This can return ALL rows from the “Customers” desk, since OR 1=1 is at all times TRUE. Going additional with this, this methodology can even return passwords if there are any.
Image an assault like this being carried out towards a big social media firm, or a big e-commerce enterprise, and one can start to see how a lot delicate knowledge might be retrieved with only one command.
Damaged Entry Management
Damaged Entry Management (BAC) has risen the ranks on the OWASP prime ten from fifth to the commonest Net Utility Safety Dangers. The 34 Frequent Weak point Enumerations (CWEs) mapped to Damaged Entry Management had extra occurrences in purposes than another class throughout OWASP’s latest testing.
The commonest forms of BAC, is Vertical and Horizontal privilege escalation. Vertical privilege escalation happens when a person can elevate their privileges and carry out actions, they need to not have entry to do.
The CVE-2019-0211, which was an Apache Native Privilege Escalation. This essential vulnerability, from 2019, affected Apache HTTP servers operating on Unix programs, particularly these using the mod_prefork, mod_worker, and mod_event libraries.
This granted attackers the potential to execute unprivileged scripts, doubtlessly resulting in root entry and compromising shared internet hosting providers. Exploiting this flaw requires the manipulation of shared-memory areas inside Apache’s employee processes, which should be executed earlier than initiating an Apache sleek restart.
The beneath is a screenshot of the POC code. As one can see, a sure degree of technical capability is required on this respect, nonetheless, vertical privilege escalation can simply as simply happen when a person’s permissions are overly permissive, or not revoked once they depart a enterprise.
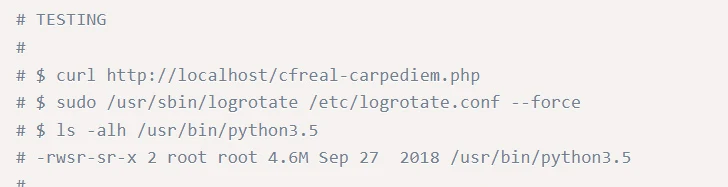
This takes us again to the precept of least privilege, a ubiquitous time period discovered all through the IT world, that’s now changing into extra commonplace as we realise how essential net purposes have change into.
Horizontal Privilege Escalation is when a person good points entry to knowledge they don’t seem to be speculated to have entry to, however that knowledge is held on the similar degree as their very own permissions. This may be seen with one commonplace person accessing the info of one other commonplace person. While this shouldn’t be allowed, the privileges usually are not rising vertical, however spreading horizontally. That is typically seen as extra harmful, as it could happen with out elevating any alerts on security programs.
With BAC changing into ever extra current within the final couple of years, it is very important keep in mind:
- Solely relying on obfuscation isn’t a adequate methodology for entry management.
- If a useful resource isn’t meant to be accessible to the general public, it needs to be denied entry by default.
- Builders ought to explicitly specify allowed entry for every useful resource on the code degree, with entry denial because the default setting.
Finest Practices – Learn between the Strains (of code!)
To keep up security, builders must confirm incoming knowledge, implement parameterized queries when interacting with databases, and apply efficient session administration strategies to guard delicate knowledge. A lot of this depends on each the security of net browsers, but in addition of the back-end security of the online servers delivering net content material, resulting in a segregation of duties in net security.
The largest drawback that arises right here, is that while Net Utility Firewalls (WAFs), can mitigate these dangers, a lot of the duty for safe implementation of net content material lands on the toes of the builders who put these websites collectively. Cybersecurity can usually change into an afterthought, with performance being most popular.
Sensible Instance – Enter Validation
Enter Validation is the best and simplest methods to implement safe coding, on this instance to stop SQL injections.
- Person Enter: The person supplies enter, for instance:
- Sanitization: The person enter isn’t instantly inserted into the SQL question. It’s sanitized and handled as knowledge, not as SQL code.
- Question Execution: The SQL question is executed with the person enter as a parameter:
- As such, the question enters the backend as beneath:


On this code, the (user_input,) is a tuple containing the person’s enter. The database driver takes care of escaping and correctly dealing with this enter. It ensures that the enter is handled as a knowledge worth, not executable SQL code.
If the person enter comprises malicious code, corresponding to “105 or 1=1,” it’s not executed as SQL. As a substitute, it is handled as a worth to be in comparison with the UserId within the database.
The database driver mechanically handles the escaping of the enter, stopping it from affecting the construction of the SQL question or introducing security vulnerabilities.
Net Utility Firewalls (WAFs)
A WAF operates at layer 7 of the OSI mannequin, and acts as a reverse proxy, making certain consumer site visitors passes via the WAF earlier than coming into the backend server. The foundations or insurance policies on the WAF defend towards the documented vulnerabilities which might be current in these backend servers and filter out malicious site visitors.
There are a plethora of WAFs in the marketplace, and these can all present a powerful defence towards the extra novel assaults, and contribute properly to a defence in depth method, the follow of safe coding is one thing that make sure the foundations of the online software is safe and won’t fall sufferer to extra advanced or novel assaults sooner or later.
WAFs are at the moment transferring in the direction of a mix of security mannequin that use behavioural-analysis applied sciences to detect malicious threats, and additional mitigate towards the threats of extra superior ‘bots’ which have been leveraged for low-effort assaults on web sites.
The primary downside of utilizing a WAF, other than the added latency and HTTP overhead, is the truth that a WAF might be bypassed by utilizing a 0-day exploit towards an internet software, which safe coding and proper sanitisation can mitigate towards extra successfully that offsetting all Net software security to a WAF. You will need to keep in mind a WAF is just a layer of security, and never your entire resolution.
Incident Response and Restoration
SecurityHQ’s recommendations to mitigate towards assaults:
- Using a WAF as a primary line of defence is essential to make sure enterprise can defend towards a big quantity of assaults.
- Guarantee up-to-date and robust commonplace algorithms and protocols are in use, this needs to be paired with correct key administration.
- Encrypt knowledge in transit with safe protocols corresponding to TLS with ahead secrecy (FS) ciphers, cipher prioritization by the server. Implement encryption utilizing directives corresponding to HTTP Strict Transport Safety (HSTS).
- Allow bot administration methods on web sites and have a documented incident response plan.
- Guarantee safe improvement practices are in place, with a documented means of testing new options on net purposes and guarantee enter validation is deployed.
- This needs to be coupled with making certain the precept of least privilege.
For extra info on these threats, converse to an professional right here. Or in case you suspect a security incident, you possibly can report an incident right here.
Observe: This text was expertly written by Tim Chambers, Senior Cyber Safety Supervisor at SecurityHQ




