In 2024, BlackBerry unveiled new proprietary analysis, underscoring the vulnerability of software program provide chains in Malaysia and world wide.
In keeping with the examine, 79% of Malaysian organizations reported cyberattacks or vulnerabilities of their software program provide chains throughout the previous 12 months, barely exceeding the worldwide common of 76%. Alarmingly, 81% of respondents revealed that they had found unknown members inside their software program provide chains throughout this era.
These findings level to the rise in provide chain assaults, focusing on susceptible digital threads that join thousands and thousands of organizations. Across the identical time this survey was launched, BlackBerry’s World Risk Intelligence Report revealed the corporate detected and stopped a median of 11,500 distinctive malware samples every day, up 53 p.c from the earlier reporting interval. It additionally stated, within the Asia Pacific area, geopolitical tensions proceed to affect cyber tendencies, together with rising state-sponsored and financially-motivated cyberattacks on essential infrastructure, provide chains and companies.
In tandem, Malaysia’s efforts to bolster cybersecurity resilience by initiatives such because the Cyber Safety Act 2024 (Act 854) and the Nationwide Semiconductor Technique (NSS), will assist to strengthen general preparedness and fortify key industries and significant infrastructure. With ambitions for the NSS to ascertain Malaysia as a worldwide semiconductor hub, it rightly emphasizes secure-by-design ideas for Web of Issues (IoT) parts and expertise growth to strengthen the IT provide chain.
The Value of Insecurity
BlackBerry’s analysis paints a stark image of the influence of provide chain breaches. Almost a 3rd of Malaysian respondents recognized working methods (30%) and IoT parts (19%) as their greatest vulnerabilities. The results of assaults are extreme, together with monetary losses (71%), reputational injury (66%), and data breaches (59%).
BlackBerry
Whereas many organizations prioritize cybersecurity, 38% admitted restoration from provide chain incidents can take as much as a month. Christine Gadsby, BlackBerry’s CISO, emphasised that defending software program provide chains requires greater than belief.
“A complete strategy that integrates expert expertise, secure-by-design practices, and trendy AI monitoring instruments is important.”
Constructing Cyber-Resilience in Malaysia
The Cyber Safety Act 2024 mandates extra rigorous requirements for securing Malaysia’s Nationwide Important Data Infrastructure, which is seen as essential to the nation’s financial future and attracting overseas funding.
Dr. Megat Zuhairy bin Megat Tajuddin, CEO of NACSA, highlighted the significance of strong provide chain security for Malaysia’s international ambitions in sectors like semiconductors and Synthetic Intelligence (AI).
“By bettering compliance, adopting cutting-edge applied sciences, and coaching a talented workforce, we will shield key infrastructure, enhance financial confidence, and strengthen worldwide commerce partnerships.”
Challenges and Alternatives Forward
Regardless of important progress in cybersecurity regulation, expertise growth and different initiatives, the analysis revealed areas for enchancment. Malaysian organizations exhibit excessive confidence of their provide chain companions’ cybersecurity measures, with 95% believing their suppliers can forestall vulnerabilities. Nevertheless, solely 18% of corporations request ongoing proof of compliance with security frameworks post-onboarding.
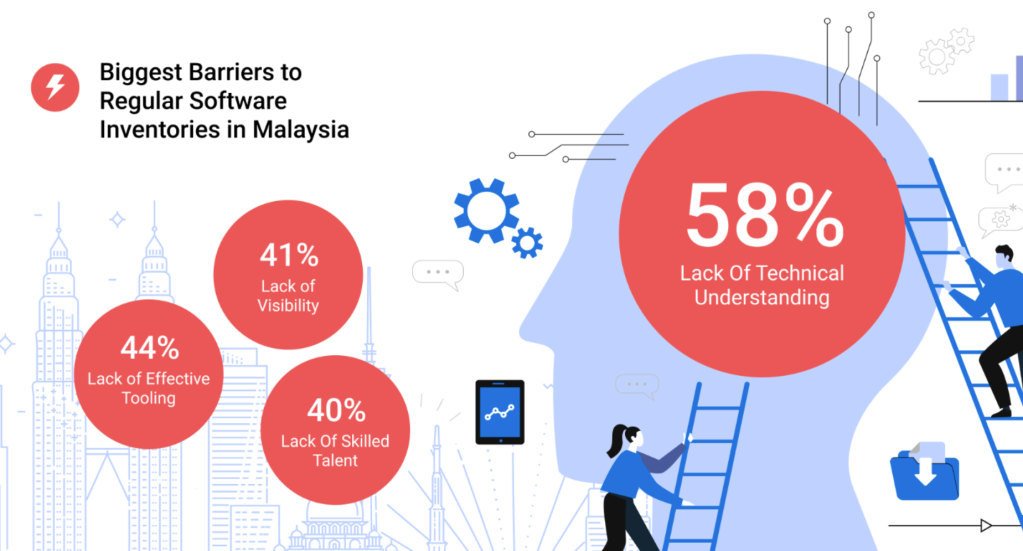
Furthermore, common software program stock audits are hindered by obstacles reminiscent of restricted technical understanding (58%), insufficient instruments (44%), and a scarcity of expert expertise (40%). To deal with these challenges, 77% of respondents expressed curiosity in adopting instruments that improve visibility into software program provide chains and automate vulnerability monitoring.
BlackBerry
Gadsby concluded by advocating for the mixing of Managed Detection and Response (MDR) applied sciences.
“These options present 24/7 menace monitoring, enabling resource-constrained IT groups to mitigate rising dangers successfully.”
The BlackBerry World Risk Report (September) additionally confirmed that organisations are more and more focused by a plethora of threats reminiscent of cyber espionage, eavesdropping, ransomware and phishing assaults. To boost the resilience of provide chains, organisations in Malaysia ought to heighten their vigilance and protections cross all menace vectors, together with units and communications, significantly following latest espionage campaigns infiltrating sovereign telecoms operators in the USA and ‘Lightspy’ cell espionage actors.
A Future-Prepared Cybersecurity Technique
As Malaysia strengthens its cybersecurity posture nationally, BlackBerry’s analysis highlights the urgency of secure-by-design practices and cross-sector collaboration.
Whereas these future-focused authorities insurance policies are an necessary first step, they can not thrive with out the proper coaching initiatives for a contemporary cybersecurity workforce. That’s the reason BlackBerry is actively supporting these efforts by its partnership with the Malaysian Communications & Multimedia Fee (MCMC) in working the Cybersecurity Heart of Excellence (CCoE) in Cyberjaya.
The CCoE is the primary of its type within the area, providing a spread of initiatives to assist construct an ecosystem of cybersecurity coaching each nationwide and regionally. It will in flip assist develop the workforce, fill a lot wanted roles and assist to safeguard towards cyberattacks focusing on Malaysian authorities establishments, companies and infrastructure.
To see the total software program provide chain examine in APAC, please go to right here. To entry the total international report, go to right here.




