Cybersecurity researchers have make clear the internal workings of the ransomware operation led by Mikhail Pavlovich Matveev, a Russian nationwide who was indicted by the U.S. authorities earlier this yr for his alleged position in launching hundreds of assaults the world over.
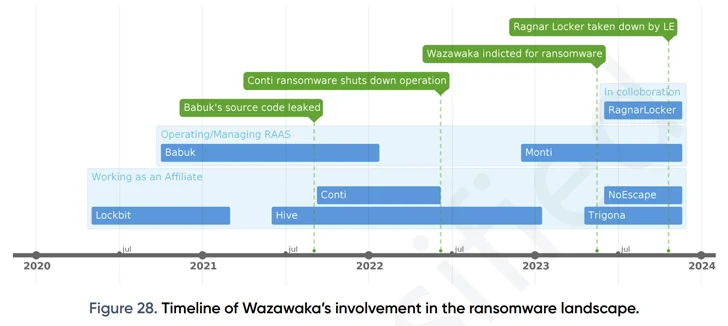
Matveev, who resides in Saint Petersburg and is understood by the aliases Wazawaka, m1x, Boriselcin, Uhodiransomwar, Orange, and waza, is alleged to have performed a vital half within the growth and deployment of LockBit, Babuk, and Hive ransomware variants since a minimum of June 2020.
“Wazawaka and his group members prominently exhibit an insatiable greed for ransom funds, demonstrating a big disregard for moral values of their cyber operations,” Swiss cybersecurity agency PRODAFT mentioned in a complete evaluation shared with The Hacker Information.
“Using ways that contain intimidation via threats to leak delicate recordsdata, partaking in dishonest practices, and persisting in retaining recordsdata even after the sufferer complies with the ransom fee, they exemplify the moral void prevalent within the practices of conventional ransomware teams.”
PRODAFT’s findings are the results of information compiled between April and December 2023 by intercepting hundreds of communication logs between numerous menace actors affiliated with completely different ransomware variants.
Matawveev is alleged to guide a group of six penetration testers – 777, bobr.kurwa, krbtgt, shokoladniy_zayac, WhyNot, and dushnila – to execute the assaults. The group has a flat hierarchy, fostering higher collaboration between the members.
“Every particular person contributes sources and experience as wanted, showcasing a exceptional stage of flexibility in adapting to new eventualities and conditions,” PRODAFT mentioned.
Matveev, apart from working as an affiliate for Conti, LockBit, Hive, Trigona, and NoEscape, additionally had a management-level position with the Babuk ransomware group up till early 2022, whereas sharing what’s being described as a “advanced relationship” with one other actor named Dudka, who is probably going the developer behind Babuk and Monti.

Attacks mounted by Matveev and his group contain using Zoominfo and companies like Censys, Shodan, and FOFA to assemble details about the victims, counting on identified security flaws and preliminary entry brokers for acquiring a foothold, along with utilizing a mixture of customized and off-the-shelf instruments to brute-force VPN accounts, escalate privileges, and streamline their campaigns.
“Following the attainment of preliminary entry, Wazawaka and his group primarily make use of PowerShell instructions to execute their most popular Distant Monitoring and Administration (RMM) software,” the corporate mentioned. “Distinctively, MeshCentral stands out because the group’s distinctive toolkit, continuously utilized as their most popular open-source software program for numerous operations.”
PRODAFT’s evaluation additional uncovered connections between Matveev and Evgeniy Mikhailovich Bogachev, a Russian nationwide linked to the event of the GameOver Zeus botnet, which was dismantled in 2014, and Evil Corp.
It is price noting that the Babuk ransomware operations rebranded as PayloadBIN in 2021, with the latter tied to Evil Corp in an obvious effort to get round sanctions imposed in opposition to it by the U.S. in December 2019.
“This technical affiliation, coupled with the identified relationship between Wazawaka and the infamous cybercriminal Bogachev, suggests deeper connections amongst Wazawaka, Bogachev, and the operations of Evil Corp,” PRODAFT mentioned.




