A subgroup of the Russian state-sponsored hacking group APT44, also called ‘Seashell Blizzard’ and ‘Sandworm’, has been concentrating on essential organizations and governments in a multi-year marketing campaign dubbed ‘BadPilot.’
The risk actor has been lively since at the least 2021 and can also be accountable for breaching networks of organizations in vitality, oil and fuel, telecommunications, delivery, and arms manufacturing sectors.
Microsoft’s Menace Intelligence workforce says that the actor is devoted to reaching preliminary entry to focus on methods, establishing persistence, and sustaining presence to permit different APT44 subgroups with post-compromise experience to take over.
“We’ve got additionally noticed the preliminary entry subgroup to pursue entry to a company previous to a Seashell Blizzard-linked damaging assault,” reads a Microsoft report shared with BleepingComputer.
Microsoft’s evaluation is “that Seashell Blizzard makes use of this preliminary entry subgroup to horizontally scale their operations as new exploits are acquired and to maintain persistent entry to present and future sectors of curiosity to Russia.”
Focusing on scope
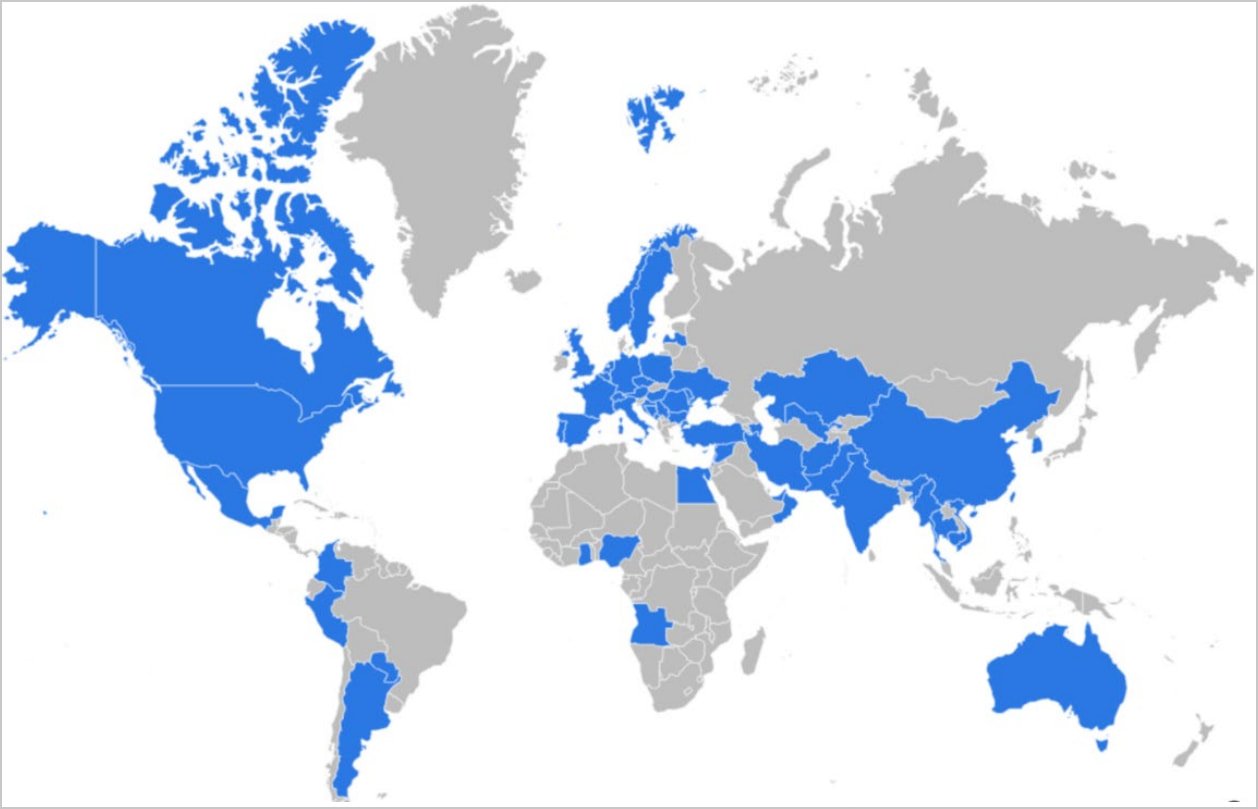
Microsoft’s earliest observations of the subgroup’s exercise present opportunistic operations concentrating on Ukraine, Europe, Central and South Asia, and the Center East, specializing in essential sectors.
Beginning 2022, following Russia’s invasion of Ukraine, the subgroup intensified its operations in opposition to essential infrastructure supporting Ukraine, together with authorities, army, transportation, and logistics sectors.
Their intrusions aimed toward intelligence assortment, operational disruptions, and wiper assaults aimed toward corrupting knowledge on the focused methods.
“We assess that the subgroup has probably enabled at the least three damaging cyberattacks in Ukraine since 2023,” mentions Microsoft concerning the subgroup’s particular exercise.
By 2023, the subgroup’s concentrating on scope had broadened, conducting large-scale compromises throughout Europe, america, and the Center East, and in 2024, it began specializing in america, United Kingdom, Canada, and Australia.
Supply: Microsoft
Preliminary entry and post-compromise exercise
The APT44 subgroup employs a number of methods to compromise networks, together with exploiting n-day vulnerabilities in internet-facing infrastructure, credential theft, and provide chain assaults.
Provide-chain assaults had been significantly efficient in opposition to organizations throughout Europe and Ukraine, the place the hackers focused regionally managed IT service suppliers after which accessed a number of purchasers.
Microsoft has noticed community scans and subsequent exploitation makes an attempt of the next vulnerabilities:
- CVE-2021-34473 (Microsoft Alternate)
- CVE-2022-41352 (Zimbra Collaboration Suite)
- CVE-2023-32315 (OpenFire)
- CVE-2023-42793 (JetBrains TeamCity)
- CVE-2023-23397 (Microsoft Outlook)
- CVE-2024-1709 (ConnectWise ScreenConnect)
- CVE-2023-48788 (Fortinet FortiClient EMS)
After exploiting the above vulnerabilities to acquire entry, the hackers established persistence by deploying customized internet shells like ‘LocalOlive’.
In 2024, the APT44 subgroup began to make use of reliable IT distant administration instruments resembling Atera Agent and Splashtop Distant Providers to execute instructions on compromised methods whereas posing as IT admins to evade detection.
Concerning the post-initial entry exercise, the risk actors use Procdump or the Home windows registry to steal credentials, and Rclone, Chisel, and Plink for knowledge exfiltration by covert community tunnels.
.jpg)
Supply: Microsoft
Researchers noticed a novel approach in 2024 because the risk actor routed visitors by the Tor community “successfully cloaking all inbound connections to the affected asset and limiting exposures from each the actor and sufferer setting.”
Lastly, the subgroup performs lateral motion to achieve all of the components of the community it could actually, and modifies the infrastructure as required for its operations.
The modifications embody DNS configuration manipulations, the creation of recent companies and scheduled duties, and the configuration of backdoor entry utilizing OpenSSH with distinctive public keys.
Microsoft says that the Russian hacker subgroup has “near-global attain” and helps Seashell Blizzard broaden its geographical concentrating on.
Within the report printed right now, the researchers share searching queries, indicators of compromise (IoCs), and YARA guidelines for defenders to catch this risk actor’s exercise and cease it earlier than .




