A crucial Apache OFBiz pre-authentication distant code execution vulnerability is being actively exploited utilizing public proof of idea (PoC) exploits.
Apache OFBiz (Open For Enterprise) is an open-source enterprise useful resource planning system many companies use for e-commerce stock and order administration, human sources operations, and accounting.
OFBiz is a part of Atlassian JIRA, a industrial mission administration and issue-tracking software program utilized by over 120,000 firms worldwide. Due to this fact, any flaws within the open-source mission are inherited by Atlassian’s product.
This authentication bypass flaw is tracked as CVE-2023-49070 and was mounted in OFBiz model 18.12.10, launched on December 5, 2023.
The problem doubtlessly enabled attackers to raise their privileges with out authentication, carry out arbitrary code execution, and entry delicate data.
Whereas investigating Apache’s repair, which was to take away the XML-RPC code from OFBiz, SonicWall researchers found that the foundation trigger for CVE-2023-49070 was nonetheless current.
This incomplete repair nonetheless allowed attackers to use the bug in a completely patched model of the software program.
Actively exploited in assaults
In a write-up printed yesterday, SonicWall researchers display it is doable to bypass Apache’s repair for the CVE-2023-49070 vulnerability when utilizing particular credential combos.
“It was found whereas researching the root trigger for the beforehand disclosed CVE-2023-49070,” explains SonicWall’s report.
“The security measures taken to patch CVE-2023-49070 left the foundation concern intact and subsequently the authentication bypass was nonetheless current.”
This patch bypass is attributable to flawed logic in dealing with empty or particular parameters like “requirePasswordChange=Y.”
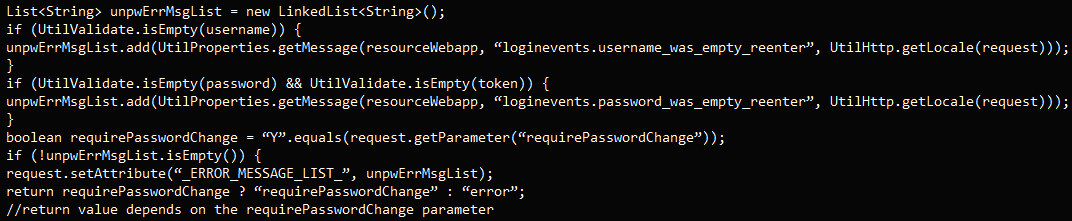
SonicWall reported their findings to the Apache crew, who rapidly resolved the flaw, which they categorized as a server-side request forgery (SSRF) downside.
The brand new bypass concern was assigned CVE-2023-51467 and was addressed in OFBiz model 18.12.11, launched on December 26, 2023.
Nonetheless, not many have upgraded to this newest launch but, and the abundance of public PoCs exploits for the pre-auth RCE makes the flaw a simple goal for hackers.
Menace monitoring service ‘Shadowserver’ reported right this moment that it has detected fairly a number of scans that leverage public PoCs, making an attempt to use CVE-2023-49070.
“All through December now we have noticed scans utilizing a PoC that has been printed for CVE-2023-49070, so anticipate related for CVE-2023-51467,” warned ShadowServer CEO Piotr Kijewski.
Kijewski advised BleepingComputer that present exploitation makes an attempt are being performed to search out weak servers by forcing them to hook up with an oast.on-line URL.
The researchers additional mentioned these scanning weak servers are significantly involved in discovering weak Confluence servers.
Confluence servers are a well-liked goal for menace actors as they generally maintain delicate information that can be utilized to unfold laterally on to additional inner companies or for extortion.
To reduce the danger, customers of Apache OFBiz are beneficial to improve to model 18.12.11 as quickly as doable.