Virtually 11 million internet-exposed SSH servers are susceptible to the Terrapin assault that threatens the integrity of some SSH connections.
The Terrapin assault targets the SSH protocol, affecting each purchasers and servers, and was developed by tutorial researchers from Ruhr College Bochum in Germany.
It manipulates sequence numbers through the handshake course of to compromise the integrity of the SSH channel, notably when particular encryption modes like ChaCha20-Poly1305 or CBC with Encrypt-then-MAC are used.
An attacker may thus downgrade the general public key algorithms for consumer authentication and disable defenses in opposition to keystroke timing assaults in OpenSSH 9.5.
A notable requirement for the Terrapin assault is the necessity for attackers to be in an adversary-in-the-middle (AitM) place to intercept and modify the handshake trade.
It’s value noting that menace actors usually compromise networks of curiosity and anticipate the best second to progress their assault.
A current report by security menace monitoring platform Shadowserver warns that there are almost 11 million SSH servers on the general public internet – recognized by distinctive IP addresses, which might be susceptible to Terrapin assaults.
This constitutes roughly 52% of all scanned samples within the IPv4 and IPv6 area monitored by Shadoserver.
A lot of the susceptible methods have been recognized in the US (3.3 million), adopted by China (1.3 million), Germany (1 million), Russia (700,000), Singapore (390,000), and Japan (380,000).
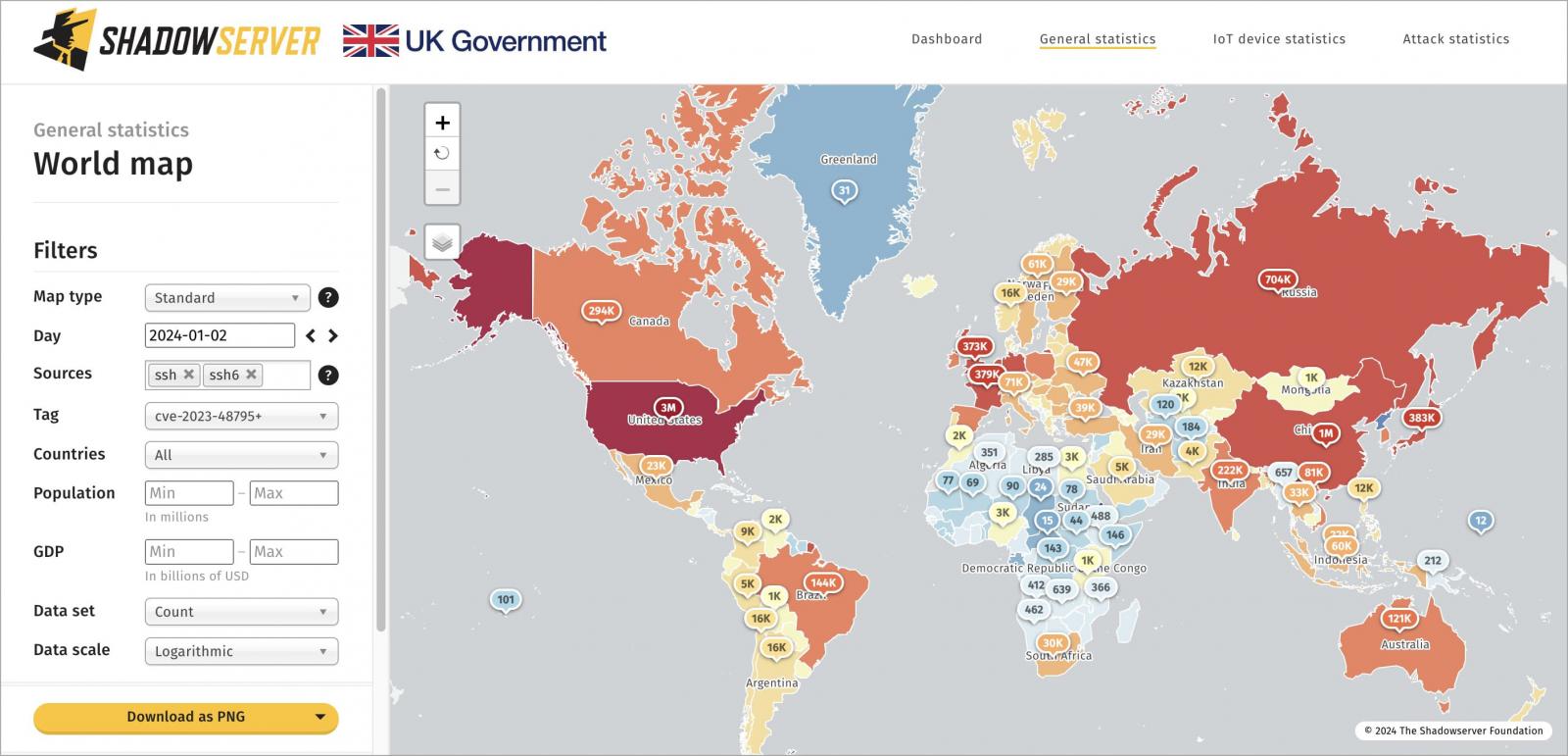
The importance of Shadowserver’s report lies in highlighting that Terrapin assaults can have a widespread impression.
Whereas not all 11 million cases are at fast threat of being attacked, it exhibits that adversaries have a big pool to select from.
If you wish to test an SSH shopper or server for its susceptibility to Terrapin, the Ruhr College Bochum workforce offers a vulnerability scanner.