Ever surprise what occurs when attackers do not break the foundations—they only comply with them higher than we do? When methods work precisely as they’re constructed to, however that “by design” habits quietly opens the door to danger?
This week brings tales that make you cease and rethink what’s actually below management. It isn’t all the time a couple of damaged firewall or missed patch—it is concerning the small decisions, default settings, and shortcuts that really feel innocent till they don’t seem to be.
The actual shock? Typically the menace would not come from exterior—it is baked proper into how issues are arrange. Dive in to see what’s quietly shaping in the present day’s security challenges.
⚡ Menace of the Week
FBI Warns of Scattered Spider’s on Airways — The U.S. Federal Bureau of Investigation (FBI) has warned of a brand new set of assaults mounted by the infamous cybercrime group Scattered Spider concentrating on the airline sector utilizing refined social engineering methods to acquire preliminary entry. Cybersecurity distributors Palo Alto Networks Unit 42 and Google Mandiant have additionally issued related alerts, urging organizations to be on alert and apply needed mitigations, together with sturdy authentication, segregation of identities, and imposing rigorous id controls for password resets and multi-factor authentication (MFA) registration, to harden their environments to guard in opposition to ways utilized by the menace actor.
🔔 Prime Information
- LapDogs ORB Community Compromised Over 1,000 SOHO Units — A China-linked APT has constructed an operational relay field (ORB) community known as LapDogs comprising over 1,000 backdoored routers for espionage functions. The digital break-ins started no later than September 2023 and have expanded ever since. The marketing campaign principally targets end-of-life routers, IoT units, internet-connected security cameras, digital servers, and different small workplace/house workplace (SOHO) units, with the aim of constructing an Operational Relay Field (ORB) community. 5 geographic areas — the US (352 victims), Japan (256 victims), South Korea (226 victims), Taiwan (80 victims), and Hong Kong (37 victims) — make up about 90% of the complete ORB community. The assaults leverage recognized security flaws in Linux-based units to drop a backdoor known as ShortLeash. The aim of the malware itself is just not recognized, though it has been discovered to share similarities with one other malware pattern utilized by UAT-5918. It is suspected that the units are being step by step, however steadily, compromised as a part of methodical and small-scale efforts the world over to achieve long-term entry to networks.
- Iranian Hacking Group Targets Israeli Cybersecurity Consultants — APT35, an Iranian state-sponsored hacking group related to the Islamic Revolutionary Guard Corps (IRGC) has been linked to a spear-phishing marketing campaign concentrating on journalists, high-profile cyber security specialists, and pc science professors in Israel that seeks to redirect them to bogus phishing pages which might be able to harvesting their Google account credentials. The assaults, which occur through emails and WhatsApp messages, leverage faux Gmail login pages or Google Meet invites to reap their credentials. The event comes amid geopolitical tensions between Iran and Israel, which has additionally led to a spike in hacktivist exercise within the area. “There are about 170 hacker teams attacking Israel, with about 1,345 cyber assaults on Israel, together with about 447 cyber assaults launched in opposition to Israel after the battle broke out,” NSFOCUS mentioned in a report printed final week. “The variety of hacker teams attacking Iran reached about 55, and the variety of cyber assaults on Iran reached about 155, of which about 20 had been launched in opposition to Iran after the battle broke out.”
- Citrix Patches Actively Exploited 0-Day — Citrix has launched security updates to handle a important flaw affecting NetScaler ADC that it mentioned has been exploited within the wild. The vulnerability, tracked as CVE-2025-6543 (CVSS rating: 9.2), is a reminiscence overflow bug that would end in unintended management circulation and denial-of-service. It is at present not recognized how the vulnerability is being exploited within the wild. The exploitation of CVE-2025-6543 coincides with reviews that one other important security vulnerability in NetScaler ADC (CVE-2025-5777, CVSS rating: 9.3) can be being weaponized in real-world assaults put up public-disclosure.
- U.S. Home Bans WhatsApp Use in Authorities Units — The U.S. Home of Representatives has formally banned congressional workers members from utilizing WhatsApp on government-issued units, citing security considerations. In accordance with the Home Chief Administrative Officer (CAO), the choice was taken based mostly on an absence of transparency in how WhatsApp protects consumer knowledge, the absence of saved knowledge encryption, and potential security dangers. WhatsApp has rejected these considerations, stating messages are end-to-end encrypted by default, and that it presents a “increased stage” of security than different apps.
- New Device to Neutralize Cryptomining Botnets — Akamai has proposed a novel mechanism to defang cryptomining botnets utilizing XMRogue, a proof-of-concept (PoC) software that lets defenders cease miners’ proxy servers from utilizing compromised endpoints for illicit mining functions. In instances the place a mining proxy is just not used, the strategy makes use of a script to ship greater than 1,000 simultaneous login requests utilizing the attacker’s pockets, which is able to power the pool to briefly ban the pockets. That mentioned, it is price noting that these strategies do not essentially take away the malicious code from the methods because it’s only a solution to disable the mining infrastructure.
️🔥 Trending CVEs
Hackers are fast to leap on newly found software program flaws—generally inside hours. Whether or not it is a missed replace or a hidden bug, even one unpatched CVE can open the door to severe harm. Beneath are this week’s high-risk vulnerabilities making waves. Overview the checklist, patch quick, and keep a step forward.
This week’s checklist contains — CVE-2025-49825 (Teleport), CVE-2025-6218 (WinRAR), CVE-2025-49144 (Notepad++), CVE-2025-27387 (OPPO ColorOS), CVE-2025-2171, CVE-2025-2172 (Aviatrix Controller), CVE-2025-52562 (ConvoyPanel), CVE-2025-27915 (Zimbra Basic Net Consumer), CVE-2025-48703 (CentOS Net Panel), CVE-2025-23264, CVE-2025-23265 (NVIDIA Megatron LM), CVE-2025-36537 (TeamViewer), CVE-2025-4563 (Kubernetes), CVE-2025-2135 (Kibana), CVE-2025-3509 (GitHub), CVE-2025-36004 (IBM i), CVE-2025-49853 (ControlID iDSecure), CVE-2025-37101 (HPE OneView for VMware vCenter), CVE-2025-3699 (Mitsubishi Electrical), CVE-2025-6709 (MongoDB), CVE-2025-1533, CVE-2025-3464 (ASUS Armoury Crate), and an unpatched flaw affecting Kerio Management.
📰 Across the Cyber World
- Safety Flaws Have an effect on 100s of Printers and Scanners — Eight security vulnerabilities have been disclosed in multifunction printers (MFP) from Brother Industries, Ltd, that have an effect on 742 fashions throughout 4 distributors, together with FUJIFILM Enterprise Innovation, Ricoh, Toshiba Tec Company, and Konica Minolta. “Some or all of those vulnerabilities have been recognized as affecting 689 fashions throughout Brother’s vary of printer, scanner, and label maker units,” Rapid7 mentioned. “Moreover, 46 printer fashions from FUJIFILM Enterprise Innovation, 5 printer fashions from Ricoh, and a pair of printer fashions from Toshiba Tec Company are affected by some or all of those vulnerabilities.” Probably the most extreme of the issues is CVE-2024-51978 (CVSS rating: 9.8), a important bug that enables distant unauthenticated attackers to leak the goal gadget’s serial quantity by chaining it with CVE-2024-51977 (CVSS rating: 5.3), and generate the goal gadget’s default administrator password. Having the admin password allows an attacker to reconfigure the gadget or abuse performance meant for authenticated customers.
- French Police Reportedly Arrest BreachForums Admins — French authorities have arrested 5 high-ranking members of BreachForums, a infamous on-line hub that focuses on promoting stolen knowledge and cybercriminal instruments. This included discussion board customers ShinyHunters, Hole, Noct, and Depressed. A fifth suspect is claimed to have been apprehended by French police officers in February 2025. He glided by the pseudonym IntelBroker (aka Kyle Northern), who has now been recognized as a 25-year-old British man named Kai West. The most recent iteration of BreachForums is at present offline. In accordance with the U.S. Division of Justice (DoJ), West’s real-world id was uncovered after undercover Federal Bureau of Investigation (FBI) brokers bought a stolen API key that granted illicit entry to 1 sufferer’s web site, and traced the Bitcoin pockets’s handle again to him. West has been charged with conspiracy to commit pc intrusions, conspiracy to commit wire fraud, accessing a protected pc to acquire data, and wire fraud. In complete, he faces as much as 50 years in jail. “Kai West, an alleged serial hacker, is charged for a nefarious, years-long scheme to steal sufferer’s [sic] knowledge and promote it for hundreds of thousands in illicit funds, inflicting greater than $25 million in damages worldwide,” mentioned FBI Assistant Director in Cost Christopher G. Raia. The U.S. is searching for his extradition.
- Canada Orders Hikvision to Shut its Canadian Operations — Canada’s authorities has ordered Chinese language CCTV methods vendor Hikvision to stop all its operations within the nation and shut down its Canadian enterprise following a nationwide security assessment. “The federal government has decided that Hikvision Canada Ic.’s continued operations in Canada could be injurious to Canada’s nationwide security,” in response to an announcement launched by Mélanie Joly, Canada’s Minister of Trade. “This dedication is the results of a multi-step assessment that assessed data and proof offered by Canada’s security and intelligence neighborhood.” As well as, the order prohibits the acquisition or use of Hikvision merchandise in authorities departments, businesses, and crown companies. Hikvision known as the allegations “unfounded” and that the choice “lacks a factual foundation, procedural equity, and transparency.”
- U.Ok. NCSC Particulars “Genuine Antics” Malware — The Nationwide Cyber Safety Centre (NCSC) is asking consideration to a brand new malware it calls Genuine Antics that runs throughout the Microsoft Outlook course of, displaying periodic malicious login prompts to steal credentials and OAuth 2.0 tokens in an try to achieve unauthorized entry to sufferer e-mail accounts. “The stolen credential and token knowledge is then exfiltrated by authenticating to the sufferer’s Outlook on the net account through the Outlook internet API, with the freshly stolen token, to ship an e-mail to an actor-controlled e-mail handle,” the NCSC mentioned. “The emails is not going to present within the sufferer’s despatched folder.”
- Microsoft Desires to Keep away from One other CrowdStrike-like Outage — Microsoft mentioned it is planning to ship a non-public preview of the Home windows endpoint security platform to pick out endpoint security companions, together with Bitdefender, CrowdStrike, ESET, SentinelOne, Trellix, Pattern Micro, and WithSecure, that can enable them to construct their anti-malware options to run exterior the Home windows kernel and within the consumer mode, simply as different common functions. “This implies security merchandise like anti-virus and endpoint safety options can run in consumer mode simply as apps do,” Microsoft mentioned. “This modification will assist security builders present a excessive stage of reliability and simpler restoration leading to much less affect on Home windows units within the occasion of sudden points.” The change, first introduced in November 2024, comes almost a 12 months after a defective CrowdStrike replace took down 8.5 million Home windows-based machines around the globe. In tandem, Microsoft mentioned it is also giving Blue Display of Dying (BSoD) an enormous visible makeover almost 40 years after its debut in Home windows, turning it black and itemizing the cease code and defective system driver behind the crash in an try to provide extra readability.
- Noyb Accuses Bumble of Violating E.U. GDPR — Bumble’s partnership with OpenAI for its Bumble for Pals function violates Europe’s Common Data Safety Regulation, in response to a grievance from Austrian privateness non-profit noyb. “Powered by OpenAI’s ChatGPT, the function is designed that can assist you begin a dialog by offering an AI-generated message,” noyb mentioned. “To be able to do that, your private profile data is fed into the AI system with out Bumble ever acquiring your consent. Though the corporate repeatedly exhibits you a banner designed to nudge you into clicking ‘Okay,’ which means that it depends on consumer consent, it really claims to have a so-called ‘authentic curiosity’ to make use of knowledge.” Noyb mentioned the “Okay” choice offers customers a false sense of management over their knowledge, when it claims to have a authentic curiosity in sending consumer knowledge to OpenAI.
- Jitter-Entice Turns Evasion into Detection — Cybersecurity researchers have designed a intelligent new method known as Jitter-Entice that goals to detect post-exploitation and command-and-control (C2) communication stemming from the usage of crimson teaming frameworks like Cobalt Strike, Sliver, Empire, Mythic, and Havoc which might be typically adopted by menace actors in cyber assaults to take care of entry, execute instructions, transfer laterally, and exfiltrate knowledge, whereas concurrently evading detection. These instruments are recognized to make use of a parameter known as “sleep” that defines how typically the beacon communicates with its operator (i.e., the C2 server). One obfuscation methodology used to cloak this periodic beaconing exercise motion is “jitter,” which provides a bit little bit of randomness to the communication sample to make sure that it stays undetected. “The jitter property for sleep-time between requests exists to create gentle randomness with the intent to look pure and like actual site visitors attributable to customers,” Varonis mentioned. Jitter-Entice demonstrates how patterns of randomness could be leveraged by defenders to find out if such site visitors exists within the first place, successfully turning attackers’ personal ways in opposition to them.
- REvil Members Launched in Russia — 4 members of the REvil ransomware group, Andrey Bessonov, Mikhail Golovachuk, Roman Muromsky, and Dmitry Korotayev, have been discovered responsible in Russia of monetary fraud and cybercrimes, and had been sentenced to 5 years in jail, however had been finally launched after a court docket decided that their sentence would quantity to time already served whereas awaiting trial. This quantities to lower than three years in detention. It is price noting that they had been arrested in early 2022 on fees regarding trafficking stolen cost knowledge and utilizing malicious software program to commit carding fraud. Different members of the crew, Daniil Puzyrevsky, Ruslan Khansvyarov, Aleksey Malozemov, and Artem Zayets, had been jailed for four-and-a-half to 6 years in October 2024. One other REvil member, Yaroslav Vasinksyi, was arrested in 2021 on the Polish border and extradited to the US a 12 months later. Final 12 months, he was sentenced in Could 2024 to virtually 14 years in jail and ordered to return $16 million to his numerous victims. It’s unusual for Russia to prosecute its personal hackers. In April 2022, Russia mentioned the U.S. had unilaterally shut down communication channels with Russia on cybersecurity and withdrawn the negotiation course of relating to the REvil gang.
- Malicious Python Package deal Shuts Down Home windows Techniques — A malicious Python package deal named psslib has been detected within the Python Package deal Index (PyPI) repository masquerading as a password security utility since November 2018, quietly attracting over 3,700 downloads up to now. The package deal is a typosquat of the authentic passlib library and is able to instantly shutting down Home windows methods when customers enter a password that doesn’t match the worth set by the package deal’s developer. The library additionally incorporates the flexibility to invoke a system reboot with out warning or consent. The invention comes as two “protestware” packages with hidden performance have been flagged within the npm registry. The packages (@link-loom/ui-sdk and @link-loom-react-sdk) particularly goal Russian-language customers visiting Russian or Belarusian domains (.ru, .su, and .by) in an online browser, blocking mouse-based interplay on the net web page and indefinitely taking part in the Ukrainian anthem on a loop. That mentioned, the assault ensures that solely repeat guests to the websites are focused, that means it is triggered solely when the goal visits the web sites greater than as soon as.
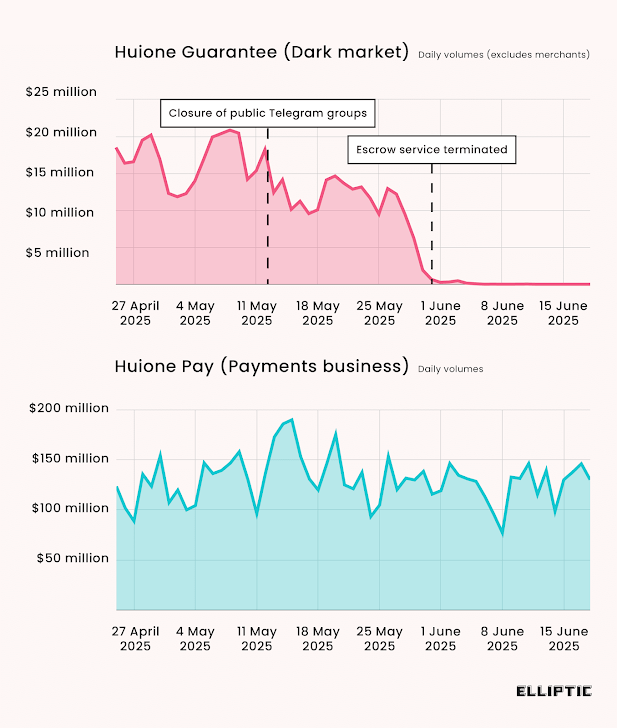
- Tudou Assure Takes Lead After HuiOne Shutdown — A bootleg Telegram market known as Tudou Assure has emerged as the primary winner following the closure of HuiOne Assure final month. The most recent findings present that it is enterprise as normal for Chinese language-language black markets within the wake of Telegram’s takedown of the 2 greatest of these bazaars, HuiOne Assure and Xinbi Assure. Each the providers are estimated to have enabled a staggering $35 billion in transactions. Blockchain intelligence agency Elliptic mentioned it is monitoring greater than thirty highly-active assure markets. “Most notably, Tudou Assure has seen customers greater than double – and cryptocurrency inflows at the moment are roughly equal to these seen for HuiOne Assure previous to its shutdown,” the corporate mentioned. “Most of the retailers working on Tudou are the identical ones that beforehand bought by way of HuiOne Assure, providing stolen knowledge, cash laundering providers and different merchandise wanted by scammers.” The shift can be important in gentle of the truth that HuiOne Assure is a significant shareholder in Tudou Assure. It acquired a 30% stake in December 2024. “These scammers have inflicted distress on hundreds of thousands of victims around the globe, stealing billions of {dollars}. Until these marketplaces are actively pursued, they are going to proceed to flourish,” Elliptic’s Tom Robinson was quoted as saying to WIRED.
- South Korea Focused by MeshAgent and SuperShell — Home windows and Linux servers in South Korea are being focused by Chinese language-speaking menace actors to drop internet shells like SuperShell and distant desktop software program comparable to MeshAgent to determine persistent entry and set up extra payloads. The IP handle used to stage the payloads has additionally been discovered to incorporate WogRAT (brief for “WingsOfGod”), a backdoor that may accumulate system data and execute arbitrary instructions issued by a distant server. The precise preliminary entry vector used within the assaults is unknown, in response to AhnLab. “The attacker appears to focus on not solely Home windows but in addition Linux, making an attempt to take management of the community the place the contaminated system belongs by transferring from the preliminary penetration part to the lateral motion part,” the cybersecurity firm mentioned. “Whereas the last word aim is unknown, the attacker could steal delicate data or infect the community with ransomware in the event that they efficiently take management of the group’s community.”
- AndroxGh0st Malware Evolves to Add New Flaws — The menace actors behind the AndroxGh0st malware have been discovered leveraging compromised web sites related to the College of California, San Diego, and an unnamed Jamaican occasions aggregator platform for C2 functions. Attacks mounted by the Python-based cloud assault software are recognized to leverage a variety of recognized security flaws, together with these affecting Apache Struts, Apache Shiro, FasterXML, Lantronix PremierWave, Popup Maker WordPress plugin, and Spring Framework, to acquire preliminary entry and drop the malware. “The botnet exploits common platforms (e.g., Apache Shiro, Spring framework, WordPress) and IoT units (Lantronix), enabling distant code execution, delicate knowledge theft, and cryptomining,” CloudSEK mentioned.
- Phishing Marketing campaign Leverages CapCut Lures — A brand new phasing marketing campaign is using faux CapCut bill lures to trick recipients into clicking on bogus hyperlinks that mimic Apple account login pages and immediate them to enter their monetary data to obtain a refund. Nonetheless, the assault is designed to stealthily hoover their credentials and bank card particulars to an exterior server. “As CapCut continues to dominate the short-form video modifying scene, cybercriminals are seizing the chance to use its recognition,” Cofense mentioned.
- Dutch Police Contact 126 People in Reference to Cracked.io — Dutch police have recognized and contacted 126 people who held accounts on the Cracked.io hacking discussion board. Authorities filed prison instances in opposition to eight suspects and warned the remaining people in opposition to participating in additional prison exercise. The youngest particular person contacted by authorities was 11 years previous. Legislation enforcement businesses from the U.S. and Europe seized Cracked and Nulled earlier this January. Previous to the takedown, the discussion board had greater than 4.7 million customers and was recognized for promoting hacking providers, stolen knowledge, and malware.
- Vulnerabilities in Airoha SoCs — Cybersecurity researchers have found three flaws in units that incorporate Airoha Techniques on a Chip (SoCs) that might be weaponized to take over inclined merchandise with out requiring any authentication or pairing, and on sure telephones, even snoop on conversations and extract name historical past and saved contacts. “Any susceptible gadget could be compromised if the attacker is in Bluetooth vary,” the researchers mentioned. The vulnerabilities, assigned the CVE identifiers CVE-2025-20700, CVE-2025-20701, and CVE-2025-20702, relate to lacking authentication for GATT Providers, lacking authentication for Bluetooth BR/EDR, and an unspecified vulnerability in a customized protocol that enables for manipulating the gadget. The Bluetooth chipset, in response to cybersecurity firm ERNW, is utilized in headsets, earbuds, dongles, audio system, and wi-fi microphones. “Some distributors will not be even conscious that they’re utilizing an Airoha SoC,” ERNW famous. “They’ve outsourced elements of the event of their gadget, such because the Bluetooth module.”
- Operation Overload Makes use of API to Amplify Professional-Russian Propaganda — A Russian disinformation operation often known as Operation Overload has adopted synthetic intelligence (AI) to generate Russian propaganda and unfold it throughout Telegram, X, BlueSky, and TikTok. The exercise entails AI-generated or deceptively edited content material, typically impersonating journalists, public figures, and revered establishments, to intervene with the political discourse in Ukraine, France, Germany, Poland, Moldova, and the US. “Whereas anti-Ukrainian narratives proceed to dominate, election interference stands out as a outstanding theme,” CheckFirst mentioned.
- Crypto Drainer Rip-off Impersonates Tax Authorities — A brand new phishing marketing campaign dubbed Declaration Entice has been noticed concentrating on cryptocurrency customers by impersonating European tax authorities, particularly Dutch businesses Belastingdienst and MijnOverheid. In these assaults, potential victims are lured through e-mail messages to phishing websites that harvest private data and run crypto drainer phishing kits to siphon seed phrases, and carry out unauthorized withdrawals by sending malicious transaction signing requests. “The sufferer’s journey begins with an e-mail that seems to return from Belastingdienst or MijnOverheid and tells the recipient they should full a particular declaration kind for his or her crypto belongings because of new tax laws launched in 2025,” Group-IB mentioned. “Scammers use strain ways: they set brief deadlines for finishing the shape and threaten victims with fines if they do not comply.” The disclosure comes as IBM X-Pressure detailed a phishing marketing campaign that is concentrating on monetary establishments the world over with weaponized Scalable Vector Graphics (SVG) recordsdata embedded with JavaScript to steal credentials and drop distant entry trojans (RATs). “When executed, the SVG-embedded JavaScript drops a ZIP archive containing a JavaScript file that’s used to obtain a Java-based loader,” IBM mentioned. “If Java is current, it deploys modular malware together with Blue Banana RAT, SambaSpy, and SessionBot.”
- Hive0131 Marketing campaign Delivers DCRat in Colombia — In a brand new phishing marketing campaign detected in early Could 2025, the menace actor tracked as Hive0131 focused customers in Colombia with bogus notifications about prison proceedings to provoke an assault chain that finally delivered the modular DCRat malware to reap recordsdata, keystrokes, and audio and video recordings. “Hive0131 is a financially motivated group possible originating from South America that routinely conducts campaigns largely in Latin America (LATAM) to ship a wide selection of commodity payloads,” IBM X-Pressure mentioned. “The present campaigns imitate official correspondence and comprise both an embedded hyperlink or a PDF lure with an embedded hyperlink. Clicking on the embedded hyperlink will provoke the an infection chain to execute the banking trojan ‘DCRat’ in reminiscence.” The assaults, which have additionally been discovered to both comprise a PDF lure with a hyperlink to a TinyURL or an embedded hyperlink to a Google Docs location, are characterised by way of an obfuscated .NET loader dubbed VMDetectLoader that is used to obtain and execute DCRat.
- CISA and NSA Name for Adoption of Reminiscence-Secure Languages — The U.S. Cybersecurity and Infrastructure Safety Company, together with the Nationwide Safety Company (NSA), issued steering on adopting memory-safe languages (MSLs) comparable to Rust to mitigate memory-related vulnerabilities in software program. MSLs provide built-in mechanisms comparable to bounds checking, reminiscence administration, knowledge race prevention, and runtime security checks to guard in opposition to reminiscence bugs. “Reaching higher reminiscence security calls for language-level protections, library assist, sturdy tooling, and developer coaching,” the businesses mentioned. “MSLs provide built-in safeguards that shift security burdens from builders to the language and the event atmosphere. By integrating security mechanisms straight on the language stage, MSLs improve security outcomes and scale back reliance on after-the-fact evaluation instruments.” Nonetheless, the report additionally factors out the challenges with adopting MSLs because of legacy methods and tightly coupled code, efficiency overhead, and the provision (or lack thereof) of instruments and libraries accessible for an MSL.
- New SmartAttack Method Makes use of Smartwatches to Steal Air-Gapped Data — A brand new side-channel assault dubbed SmartAttack has demonstrated the usage of smartwatches as receivers for ultrasonic covert communication in air-gapped environments. The strategy, in response to Dr. Mordechai Guri, the top of the Offensive Cyber Analysis Lab within the Division of Software program and Data Techniques Engineering on the Ben Gurion College of the Negev in Israel, makes use of the built-in microphones of smartwatches to seize covert alerts in real-time throughout the ultrasonic frequency vary of 18-22 kHz. As with different assaults of this type, the menace mannequin presupposes that the attacker has already infiltrated the air-gapped system and implanted malware that operates stealthily, transmitting data utilizing the contaminated machine’s audio system in a frequency vary that is inaudible to people. On the opposite finish, the assault additionally requires the menace actor to compromise the smartwatch of a person with entry to the secured atmosphere, and deploy malware able to receiving the covert ultrasonic communication, decoding it, reconstructing it, and forwarding it to the attacker’s infrastructure. In an experimental setup, SmartAttack can be utilized to transmit knowledge by way of ultrasonic alerts over distances of greater than 6 meters, with knowledge charges of as much as 50 bits per second. Dr. Guri, who disclosed RAMBO and PIXHELL assaults final 12 months to exfiltrate knowledge from air-gapped methods, mentioned the findings spotlight the “security dangers posed by smartwatches in high-security environments.” Potential mitigations embody prohibiting smartwatches and related audio-capable wearables when getting into safe environments, deploying ultrasonic monitoring methods to determine unauthorized transmissions, deploying ultrasonic jammers, and bodily eradicating or disabling audio {hardware} elements.
- Google Provides New Safety Characteristic to Sort out XSS Attacks — Google has added a brand new security function to the Chrome browser that mechanically escapes “<” and “>” characters inside HTML attributes. The brand new function is designed to stop cross-site scripting assaults that depend on slipping in malicious code inside HTML code. The function shipped with the steady model of Chrome 138 launched on June 24, 2025. “It is doable {that a} sanitizer could have a DOM tree it considers secure; nonetheless, after re-parsing, this DOM tree will likely be materially completely different, leading to an XSS,” Google’s Michał Bentkowski mentioned. Any such XSS assault is known as mutation XSS (mXSS).

🎥 Cybersecurity Webinars
- Designing Id for Belief at Scale—With Privateness, AI, and Seamless Logins in Thoughts ➝ In in the present day’s AI-powered world, buyer id is all about belief. This webinar unpacks insights from the Auth0 2025 Tendencies Report—overlaying how customers react to AI, rising privateness expectations, and the most recent id threats. Whether or not you are constructing login flows or belief methods, you may get clear, sensible recommendation to remain forward.
- Cease Pip Putting in and Praying: Safe Your Python Provide Chain in 2025 ➝ The Python ecosystem in 2025 is below assault—from repo jacking and typosquatting to hidden flaws in widespread container photos. When you’re nonetheless “pip putting in and hoping,” it is time to rethink. Be a part of security specialists as they unpack actual threats, clarify instruments like CVE, Sigstore, and SLSA, and share how PyPI is responding. Whether or not you are utilizing YOLO fashions or managing manufacturing apps, you may get clear, sensible steps to safe your Python provide chain in the present day.
🔧 Cybersecurity Instruments
- RIFT ➝ Microsoft has open-sourced RIFT, a software that helps analysts spot attacker-written code in complicated Rust malware. As Rust turns into extra common amongst menace actors, malware is getting more durable to research. RIFT cuts by way of the noise through the use of automated signature matching and binary diffing to spotlight solely the customized code—saving time and enhancing detection.
Disclaimer: These newly launched instruments are for instructional use solely and have not been absolutely audited. Use at your individual danger—assessment the code, check safely, and apply correct safeguards.
🔒 Tip of the Week
Past Defaults: Mastering Home windows Hardening ➝ Default Home windows settings are constructed for ease, not security. That is tremendous for informal use—however when you care about defending your knowledge, enterprise, and even simply your privateness, it is time to transcend the fundamentals.
The excellent news? You do not must be a sysadmin to lock down your system. Instruments like HardeningKitty, CIS-CAT Lite, and Microsoft’s Safety Compliance Toolkit do the heavy lifting for you. They scan your system and let you know precisely what to repair—like disabling outdated protocols (SMBv1, NetBIOS), hardening Workplace macros, or turning off dangerous Home windows options you do not even use.
If that sounds a bit a lot, don’t fret—there are one-click apps too. ConfigureDefender helps you to max out Microsoft Defender’s safety (together with turning on hidden superior guidelines). WPD and O&O ShutUp10++ enable you lower Home windows monitoring, bloatware, and junk settings in minutes. Consider them because the “Privateness + Safety” switches Microsoft ought to’ve given you by default.
Wish to get severe? Begin with CIS-CAT Lite to see the place your system stands, then run HardeningKitty to shut the gaps. These aren’t simply checkboxes—you are slicing off real-world assault paths like phishing payloads, document-based malware, and lateral motion throughout networks.
Backside line: You do not have to “simply use Home windows as it’s.” You can also make it be just right for you, not in opposition to you—with out breaking something. Small modifications, massive affect.
Conclusion
It is simple to get caught up within the technical particulars, however on the finish of the day, it is about making good choices with the instruments and time now we have. Nobody can repair the whole lot without delay—however figuring out the place the cracks are is half the battle. Whether or not it is a fast configuration examine or a deeper coverage rethink, small steps add up.
Take a couple of minutes to scan the highlights and see the place your group may want a re-evaluation.




