A critical-severity vulnerability within the Superior Customized Fields: Prolonged (ACF Prolonged) plugin for WordPress may be exploited remotely by unauthenticated attackers to acquire administrative permissions.
ACF Prolonged, at present energetic on 100,000 web sites, is a specialised plugin that extends the capabilities of the Superior Customized Fields (ACF) plugin with options for builders and superior web site builders.
The vulnerability, tracked as CVE-2025-14533, may be leveraged for admin privileges by abusing the plugin’s ‘Insert Person / Replace Person’ kind motion, in variations of ACF Prolonged 0.9.2.1 and earlier.

The flaw arises from the dearth of enforcement of function restrictions throughout form-based person creation or updates, and exploitation works even when function limitations are appropriately configured within the subject settings.
“Within the weak model [of the plugin], there are not any restrictions for kind fields, so the person’s function may be set arbitrarily, even to ‘administrator’, whatever the subject settings, if there’s a function subject added to the shape,” Wordfence explains.
“As with all privilege escalation vulnerability, this can be utilized for full web site compromise,” the researchers warn.
Though the end result from exploiting the flaw is extreme, Wordfence notes that the difficulty is barely exploitable on websites that explicitly use a ‘Create Person’ or ‘Replace Person’ kind with a task subject mapped.
CVE-2025-14533 was found by security researcher Andrea Bocchetti, who, on December 10, 2025, submitted a report back to Wordfence to validate the difficulty and escalate it to the seller.
4 days later, the seller addressed the issue and launched it in ACF Prolonged model 0.9.2.2.
Primarily based on obtain stats from wordpress.org, roughly 50,000 customers have downloaded the plugin since then. Assuming all downloads had been for the most recent model, that leaves roughly an equal variety of websites uncovered to assaults.
WordPress plugin enumeration exercise
Though no assaults concentrating on CVE-2025-14533 have been noticed but, a report from menace monitoring agency GreyNoise presents large-scale WordPress plugin reconnaissance exercise aimed toward enumerating doubtlessly weak websites.
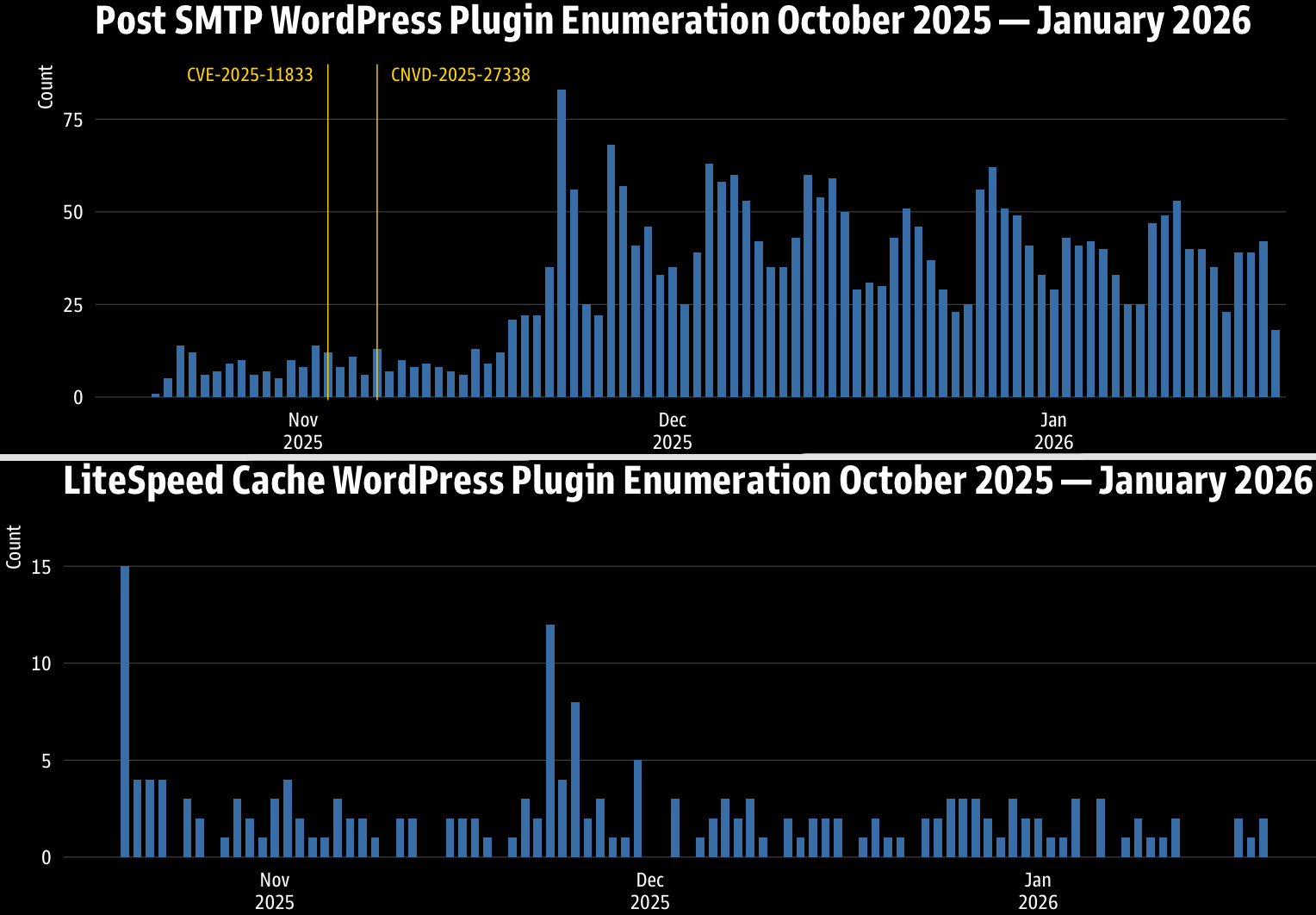
In line with GreyNoise, from late October 2025 to mid-January 2026, almost 1,000 IPs throughout 145 ASNs focused 706 distinct WordPress plugins in over 40,000 distinctive enumeration occasions.
Essentially the most focused plugins are Submit SMTP, Loginizer, LiteSpeed Cache, website positioning by Rank Math, Elementor, and Duplicator.
Supply: GreyNoise
Energetic exploitation of the Submit SMTP flaw CVE-2025-11833 was reported in early November 2025 by Wordfence, and GreyNoise’s data point out a centered effort concentrating on this flaw involving 91 IPs.
One other flaw GreyNoise urged admins to patch is CVE-2024-28000, which impacts LiteSpeed Cache and was marked as actively exploited by Wordfence in August 2024.

As MCP (Mannequin Context Protocol) turns into the usual for connecting LLMs to instruments and knowledge, security groups are transferring quick to maintain these new companies protected.
This free cheat sheet outlines 7 finest practices you can begin utilizing at the moment.




