A crypto pockets maker claimed this week that hackers could also be focusing on folks with an iMessage “zero-day” exploit — however all indicators level to an exaggerated menace, if not a downright rip-off.
Belief Pockets’s official X (beforehand Twitter) account wrote that “we now have credible intel relating to a high-risk zero-day exploit focusing on iMessage on the Darkish Internet. This may infiltrate your iPhone with out clicking any hyperlink. Excessive-value targets are possible. Every use raises detection danger.”
The pockets maker advisable iPhone customers to show off iMessage utterly “till Apple patches this,” despite the fact that no proof reveals that “this” exists in any respect.
The tweet went viral, and has been seen over 3.6 million instances as of our publication. Due to the eye the put up obtained, Belief Pockets hours later wrote a follow-up put up. The pockets maker doubled down on its resolution to go public, saying that it “actively communicates any potential threats and dangers to the neighborhood.”
Belief Pockets, which is owned by crypto change Binance, didn’t reply to information.killnetswitch’s request for remark. Apple spokesperson Scott Radcliffe declined to remark when reached Tuesday.
Because it seems, in line with Belief Pockets’s CEO Eowyn Chen, the “intel” is an commercial on a darkish website online referred to as CodeBreach Lab, the place somebody is providing mentioned alleged exploit for $2 million in bitcoin cryptocurrency. The advert titled “iMessage Exploit” claims the vulnerability is a distant code execution (or RCE) exploit that requires no interplay from the goal — generally referred to as “zero-click” exploit — and works on the most recent model of iOS. Some bugs are referred to as zero-days as a result of the seller has no time, or zero days, to repair the vulnerability. On this case, there isn’t a proof of an exploit to start with.
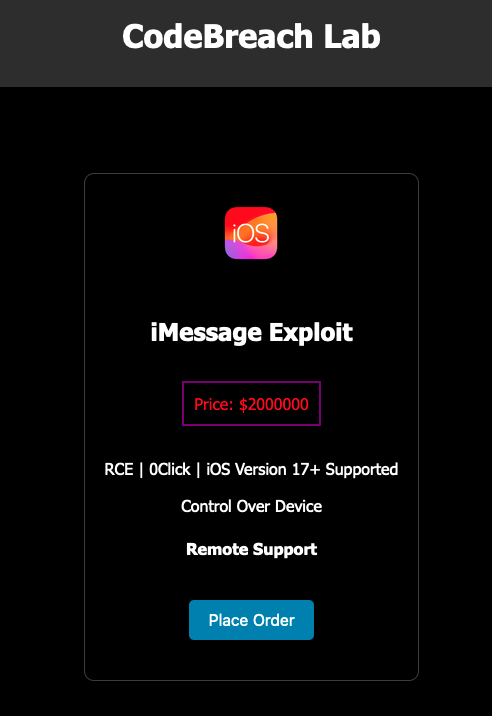
A screenshot of the darkish net advert claiming to promote an alleged iMessage exploit. Picture Credit: information.killnetswitch
RCEs are among the strongest exploits as a result of they permit hackers to remotely take management of their goal units over the web. An exploit like an RCE coupled with a zero-click functionality is extremely priceless as a result of these assaults could be performed invisibly with out the gadget proprietor understanding. In actual fact, an organization that acquires and resells zero-days is presently providing between $3 to $5 million for that sort of zero-click zero-day, which can be an indication of how arduous it’s to search out and develop these kind of exploits.
Contact Us
Do you’ve got any details about precise zero-days? Or about spyware and adware suppliers? From a non-work gadget, you possibly can contact Lorenzo Franceschi-Bicchierai securely on Sign at +1 917 257 1382, or through Telegram, Keybase and Wire @lorenzofb, or e-mail. You can also contact information.killnetswitch through SecureDrop.
Zero-days do exist, and have been utilized by authorities hacking items for years. However in actuality, you most likely don’t want to show off iMessage except you’re a high-risk person, similar to a journalist or dissident below an oppressive authorities, for instance.
It’s higher recommendation to recommend folks activate Lockdown Mode, a particular mode that disables sure Apple gadget options and functionalities with the purpose of decreasing the avenues hackers can use to assault iPhones and Macs.
In response to Apple, there isn’t a proof anybody has efficiently hacked somebody’s Apple gadget whereas utilizing Lockdown Mode. A number of cybersecurity consultants like Runa Sandvik and the researchers who work at Citizen Lab, who’ve investigated dozens of circumstances of iPhone hacks, suggest utilizing Lockdown Mode.
For its half, CodeBreach Lab seems to be a brand new web site with no observe file. After we checked, a search on Google returned solely seven outcomes, considered one of which is a put up on a widely known hacking discussion board asking if anybody had beforehand heard of CodeBreach Lab.
On its homepage — with typos — CodeBreach Lab claims to supply a number of forms of exploits apart from for iMessage, however gives no additional proof.
The homeowners describe CodeBreach Lab as “the nexus of cyber disruption.” However it will most likely be extra becoming to name it the nexus of braggadocio and naivety.
information.killnetswitch couldn’t attain CodeBreach Lab for remark as a result of there isn’t a option to contact the alleged firm. After we tried to purchase the alleged exploit — as a result of why not — the web site requested for the client’s identify, e-mail handle, after which to ship $2 million in bitcoin to a selected pockets handle on the general public blockchain. After we checked, no person has up to now.
In different phrases, if somebody desires this alleged zero-day, they should ship $2 million to a pockets that, at this level, there isn’t a option to know who it belongs to, nor — once more — any option to contact.
And there’s a superb likelihood that it’s going to stay that method.




