At the moment, at Wild West Hackin’ Fest, security researcher Wietze Beukema disclosed a number of vulnerabilities in Home windows LK shortcut information that permit attackers to deploy malicious payloads.
Beukema documented 4 beforehand unknown methods for manipulating Home windows LNK shortcut information to cover malicious targets from customers inspecting file properties.
LNK shortcuts have been launched with Home windows 95 and use a posh binary format that enables attackers to create misleading information that seem reputable in Home windows Explorer’s properties dialog however execute solely completely different applications when opened.

The found points exploit inconsistencies in how Home windows Explorer prioritizes conflicting goal paths specified throughout a number of non-compulsory knowledge buildings inside shortcut information.
The simplest variants use forbidden Home windows path characters, corresponding to double quotes, to create seemingly legitimate however technically invalid paths, inflicting Explorer to show one goal whereas executing one other, whereas one other makes use of non-conforming LinkTargetIDList values to execute a path aside from the one displayed within the LinkInfo subject.
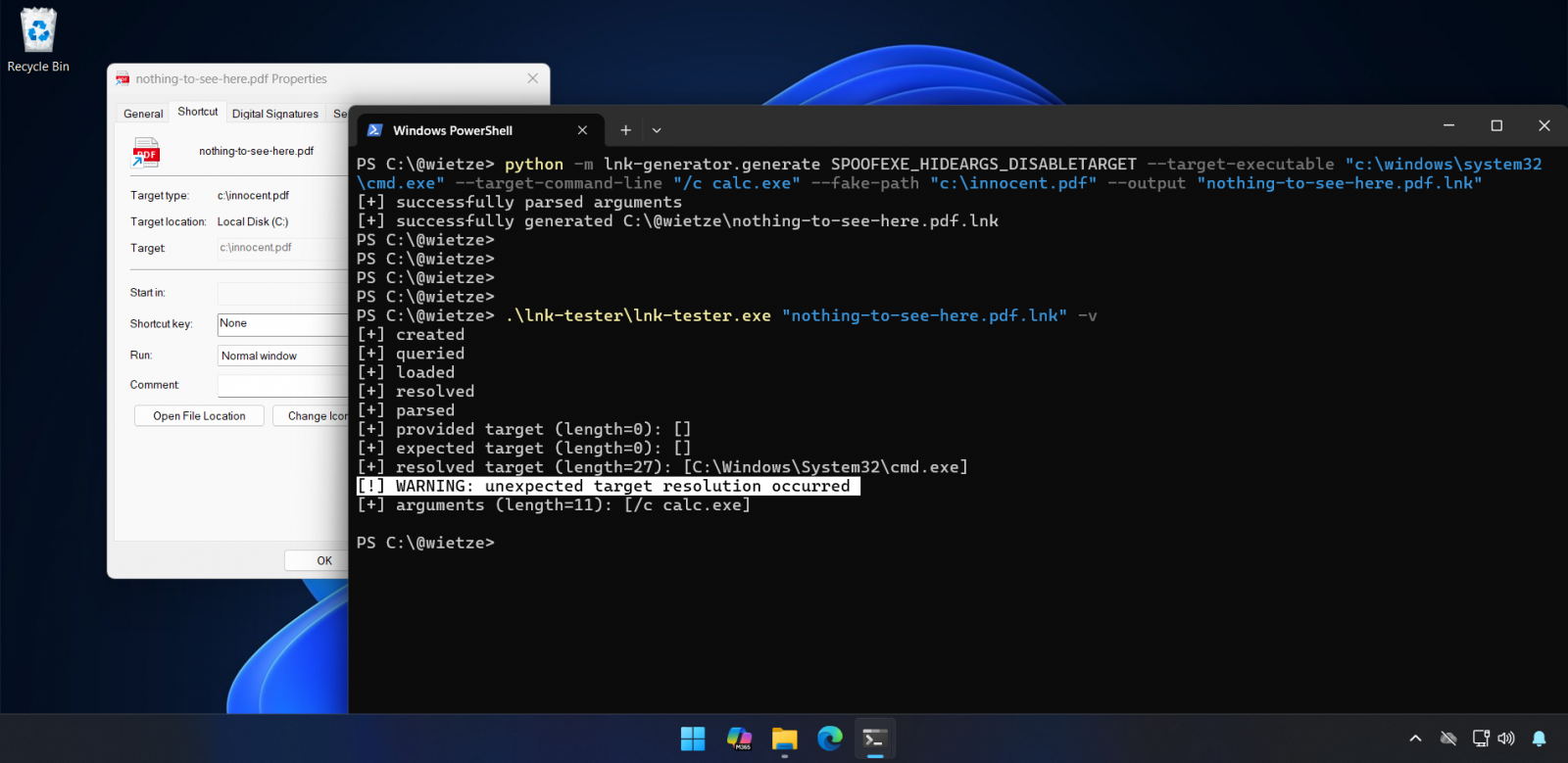
“This leads to the unusual state of affairs the place the person sees one path within the Goal subject, however upon execution, a very different path is executed. Because of the subject being disabled, it is usually attainable to “cover” any command- line arguments which might be offered,” Beukema stated.
Essentially the most highly effective approach recognized includes manipulating the EnvironmentVariableDataBlock construction inside LNK information. By setting solely the ANSI goal subject and leaving the Unicode subject empty, attackers can show a faux goal corresponding to “bill.pdf” within the properties window whereas truly executing PowerShell or different malicious instructions.
“Opening the LNK executes the “precise” goal instantly, not having to open it twice. Moreover, as a result of on this case the spoofed goal is in TargetIdList and the precise goal in EnvironmentVariableDataBlock, the precise goal might utilise setting variables,” Beukema defined.
“The goal program/file/listing is totally spoofed,” and “any command-line arguments are hidden,” the researcher additionally famous, which makes detection extraordinarily tough for customers.
That is attainable as a result of, as Beukema stated, Home windows Explorer will deal with all these malformed LNK shortcuts forgivingly, displaying spoofed info reasonably than rejecting invalid information.
The researcher has additionally launched “lnk-it-up,” an open-source device suite that generates Home windows LNK shortcuts utilizing these methods for testing and may determine doubtlessly malicious LNK information by predicting what Explorer shows versus what truly executes.
MSRC: Not a vulnerability
When Beukema submitted the EnvironmentVariableDataBlock challenge to the Microsoft Safety Response Middle in September (VULN-162145), Microsoft declined to categorise it as a security vulnerability, arguing that exploitation requires person interplay and doesn’t breach security boundaries.
“These methods don’t meet the bar for instant servicing below our severity classification tips as they require an attacker to trick a person into working a malicious file,” a Microsoft spokesperson instructed BleepingComputer when requested whether or not the corporate plans to deal with any of the failings.
“Microsoft Defender has detections in place to determine and block this risk exercise, and Sensible App Management gives a further layer of safety by blocking malicious information from the Web. As a security greatest follow, we strongly encourage prospects to heed security warnings and keep away from opening information from unknown sources.”
Microsoft additionally famous that Home windows identifies shortcut information (.lnk) as doubtlessly harmful and, when trying to open a .lnk file downloaded from the Web, routinely triggers a security warning advising customers to not open information from unknown sources. Microsoft strongly recommends heeding this warning.
Nonetheless, Beukema added that “there’s a purpose attackers nonetheless like LNK information – customers shortly click on by way of these kinds of warnings. In any other case, CVE-2025-9491 would not have been as ‘profitable’ because it was both.”
CVE-2025-9491, the security vulnerability talked about by the security researchers, is just like the problems Beukema found and may be exploited to cover command-line arguments through the use of extreme whitespace padding. Cybercrime teams and state-backed hacking teams from North Korea, Iran, Russia, and China have been abusing this security flaw for years in zero-day assaults.
Whereas initially Microsoft stated that CVE-2025-9491 would not break security boundaries and refused to repair the difficulty, it silently modified LNK information in June 2025 in an obvious effort to mitigate this actively exploited vulnerability.
As Pattern Micro risk analysts revealed in March 2025, CVE-2025-9491 was already being extensively exploited by not less than 11 state-sponsored teams and cybercrime gangs, together with Evil Corp, Bitter, APT37, APT43 (also referred to as Kimsuky), Mustang Panda, SideWinder, RedHotel, Konni, and others.
Cybersecurity agency Arctic Wolf additionally reported in October that the Mustang Panda Chinese language state-backed hacking group was exploiting this Home windows vulnerability in zero-day assaults focusing on European diplomats in Hungary, Belgium, and different European nations to deploy the PlugX distant entry trojan (RAT) malware.

Trendy IT infrastructure strikes sooner than handbook workflows can deal with.
On this new Tines information, learn the way your group can scale back hidden handbook delays, enhance reliability by way of automated response, and construct and scale clever workflows on high of instruments you already use.




