A brand new menace actor referred to as Amaranth Dragon, linked to APT41 state-sponsored Chinese language operations, exploited the CVE-2025-8088 vulnerability in WinRAR in espionage assaults on authorities and regulation enforcement companies.
The hackers mixed professional instruments with the customized Amaranth Loader to ship encrypted payloads from command-and-control (C2) servers behind Cloudflare infrastructure, for extra correct concentrating on and elevated stealth.
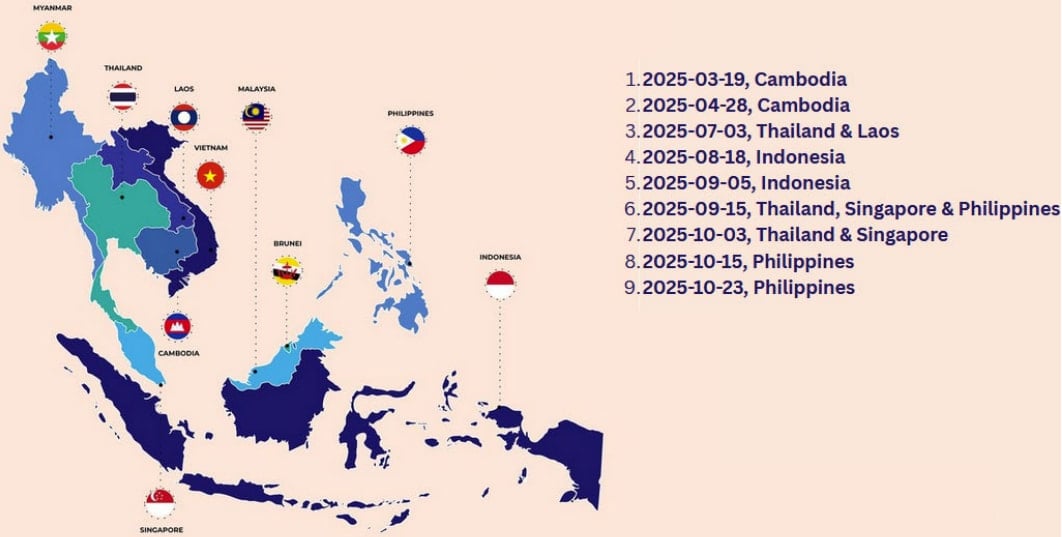
Based on researchers at cybersecurity firm Examine Level, Amaranth Dragon focused organizations in Singapore, Thailand, Indonesia, Cambodia, Laos, and the Philippines.

The CVE-2025-8088 vulnerability may be exploited to write down malicious information to arbitrary areas by leveraging the Alternate Data Streams (ADS) characteristic in Home windows. A number of menace actors exploited it in zero-day assaults since mid-2025 to attain persistence by dropping malware within the Home windows Startup folder.
Final week, a report from Google Menace Intelligence Group (GTIG) confirmed that CVE-2025-8088 was nonetheless actively exploited by a number of menace teams, together with RomCom, APT44, Turla, and varied China-linked dangerous actors.
Examine Level stories that Amaranth Dragon began exploiting the WinRAR flaw on August 18, 2025, 4 days after the primary working exploit grew to become publicly accessible.
Nonetheless, the researchers have been monitoring the malicious actor’s exercise since March 2025 and recognized a number of campaigns, every restricted to concentrating on one or two international locations by way of strict geofencing.
Moreover, the lures used within the assaults had been themed round geopolitical or native occasions.
Supply: Examine Level
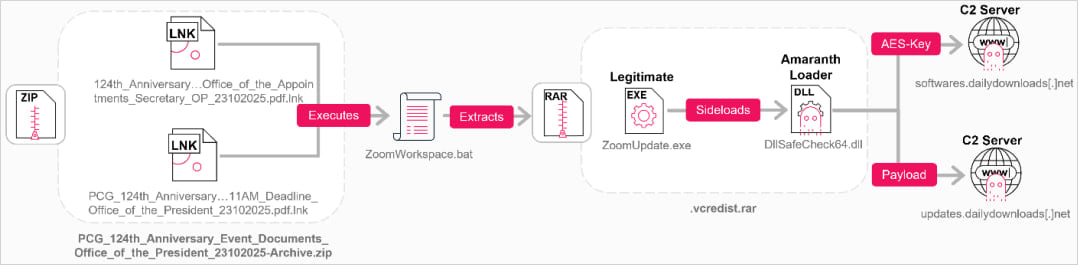
In assaults earlier than August 2025, Amaranth Dragon’s assaults relied on ZIP archives with .LNK and .BAT information that included the scripts to decrypt and run the group’s loader.
When exploits for CVE-2025-8088 grew to become accessible, the menace actor leveraged the vulnerability to position a malicious script within the Startup folder. In some instances, a Registry Run key was additionally created for redundancy.
These mechanisms launch a digitally signed executable that launches the Amaranth Loader payload utilizing the DLL-sideloading approach.
Supply: Examine Level
The loader retrieves an AES-encrypted payload from an exterior URL and decrypts it in reminiscence. In lots of instances, this payload was the Havoc C2 post-exploitation framework, which has been abused in cyberattacks since at the least 2023 and in addition seen in ClickFix-based assaults.
To filter visitors from international locations exterior the assault scope, the actor used C2 servers behind Cloudflare infrastructure configured to just accept visitors solely from focused areas.
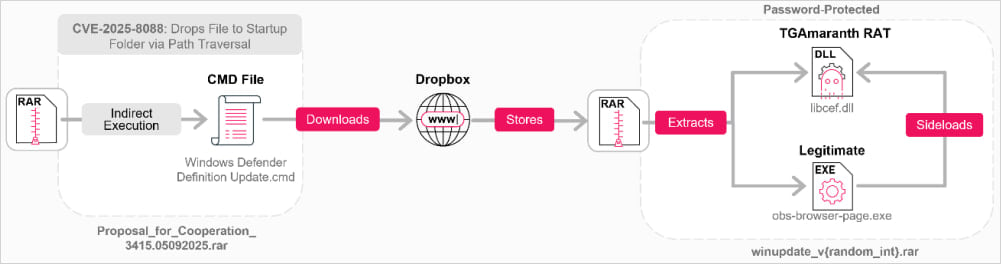
Examine Level noticed a brand new distant entry instrument, tracked as TGAmaranth RAT, being deployed in more moderen Amaranth Dragon assaults. The RAT makes use of a Telegram bot for C2 exercise.
Supply: Examine Level
TGAmaranth additionally helps file importing/downloading, taking screenshots, and itemizing operating processes on the host.
It may well evade detection by implementing varied protections towards debugging, antivirus, and endpoint detection and response (EDR) options, which embrace changing a hooked ntdll.dll, a Home windows system library used for low-level interactions, with an unhooked copy.
Given the widespread exploitation of CVE-2025-8088 by a number of menace actors, organizations are suggested to improve to WinRAR model 7.13 or later (the most recent is 7.20), which addresses the flaw.
Examine Level says that Amaranth Dragon’s assaults present that the actor has “technical proficiency and operational self-discipline” and may adapt its ways and infrastructure for optimum affect on its targets.
The researcher’s report accommodates indicators of compromise for archives, URLs, supporting information, and the malware utilized in assaults. YARA guidelines are additionally accessible to assist defenders detect Amaranth Dragon intrusions.

Fashionable IT infrastructure strikes sooner than handbook workflows can deal with.
On this new Tines information, find out how your staff can cut back hidden handbook delays, enhance reliability by automated response, and construct and scale clever workflows on prime of instruments you already use.




