Iron Mountain, a number one information storage and restoration companies firm, says {that a} latest breach claimed by the Everest extortion gang is restricted to largely advertising supplies.
Headquartered in Portsmouth, New Hampshire, and based in 1951, Iron Mountain makes a speciality of information facilities and data administration, and has over 240,000 clients worldwide from greater than 61 international locations, together with 95% of the Fortune 1000.
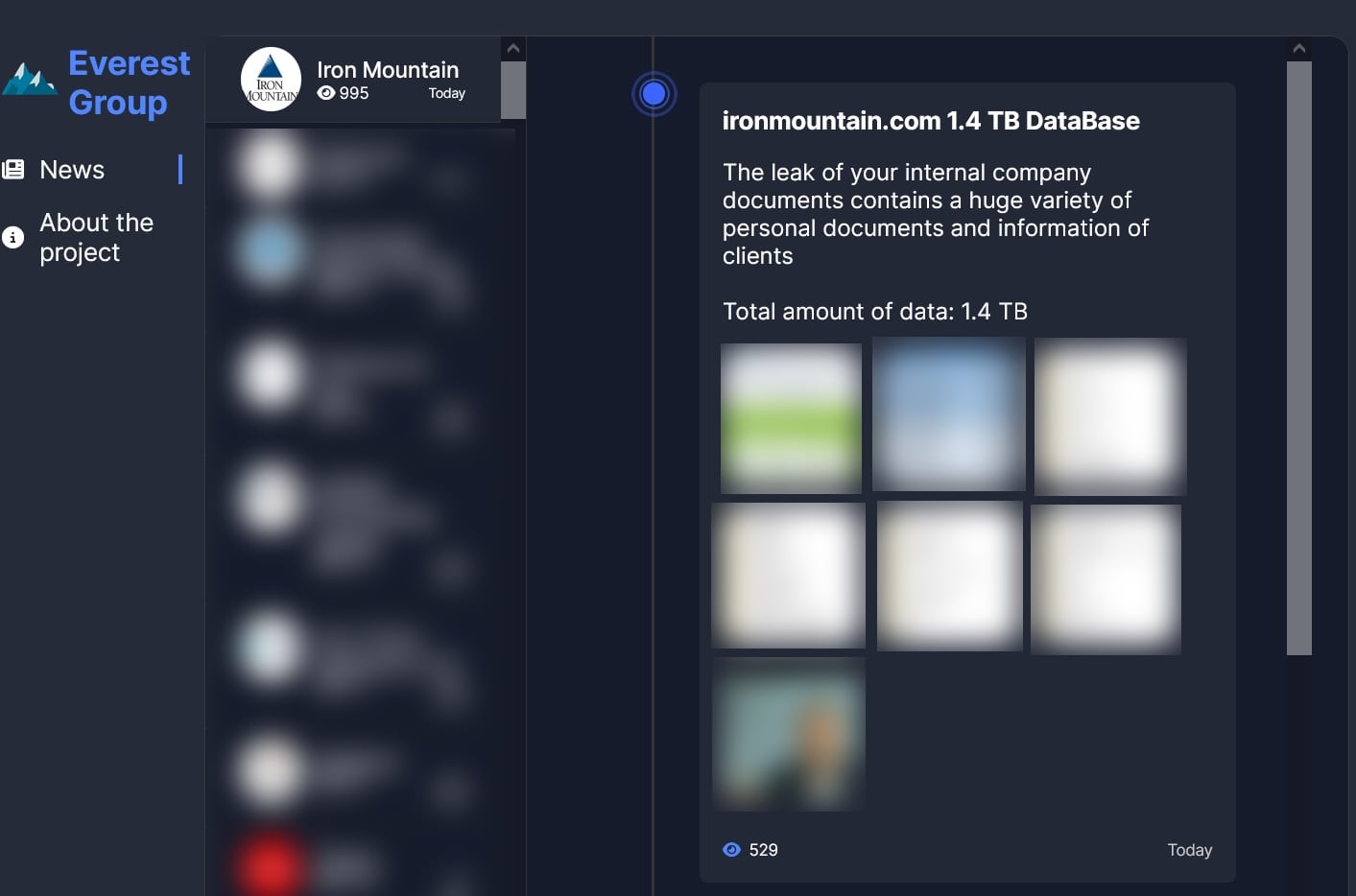
The corporate’s assertion comes after the cybercrime group claimed on its darkish internet leak website that it had stolen 1.4 TB of “inside firm paperwork” containing “private paperwork and knowledge on purchasers.”

Nonetheless, Iron Mountain advised BleepingComputer that the attackers used compromised credentials to entry a single folder on a file-sharing server storing advertising supplies.
It additionally added that the Everest operators did not deploy any ransomware payloads on the server, and no different Iron Mountain techniques had been breached within the incident.
“No buyer confidential or delicate data has been concerned. A single compromised login credential was used to realize entry to at least one folder, consisting primarily of selling supplies shared with third-party distributors on a public-facing file-sharing website,” the corporate advised BleepingComputer.
“Right now, we additionally verify that no Iron Mountain techniques have been breached, and there’s no ransomware or malware involvement, or another cyber exercise, past the compromised folder credential, which has since been deactivated.”
Because it surfaced in 2020, the Everest ransomware group has shifted ways from encrypting victims’ techniques with ransomware to data-theft-only company extortion.
Everest can also be identified for appearing as an preliminary entry dealer for different risk actors and cybercrime gangs, promoting entry to breached company networks for a payment.
Over the past 5 years, Everest has added a whole bunch of victims to its leak portal, which is utilized in double-extortion assaults wherein the risk actors threaten to publish stolen recordsdata until victims pay ransoms.
In August 2024, the U.S. Division of Well being and Human Companies additionally warned that Everest was more and more focusing on healthcare organizations throughout the US.
Extra not too long ago, the cybercrime operation took down its web site in April 2025 after it was defaced and its contents changed with the “Do not do crime CRIME IS BAD xoxo from Prague” message.

Fashionable IT infrastructure strikes quicker than guide workflows can deal with.
On this new Tines information, learn the way your staff can scale back hidden guide delays, enhance reliability via automated response, and construct and scale clever workflows on high of instruments you already use.




