Marquis Software program Options, a Texas-based monetary companies supplier, is blaming a ransomware assault that impacted its programs and affected dozens of U.S. banks and credit score unions in August 2025 on a security breach reported by SonicWall a month later.
The software program firm offers knowledge analytics, compliance reporting, CRM instruments, and digital advertising companies to greater than 700 banks, credit score unions, and mortgage lenders throughout the USA.
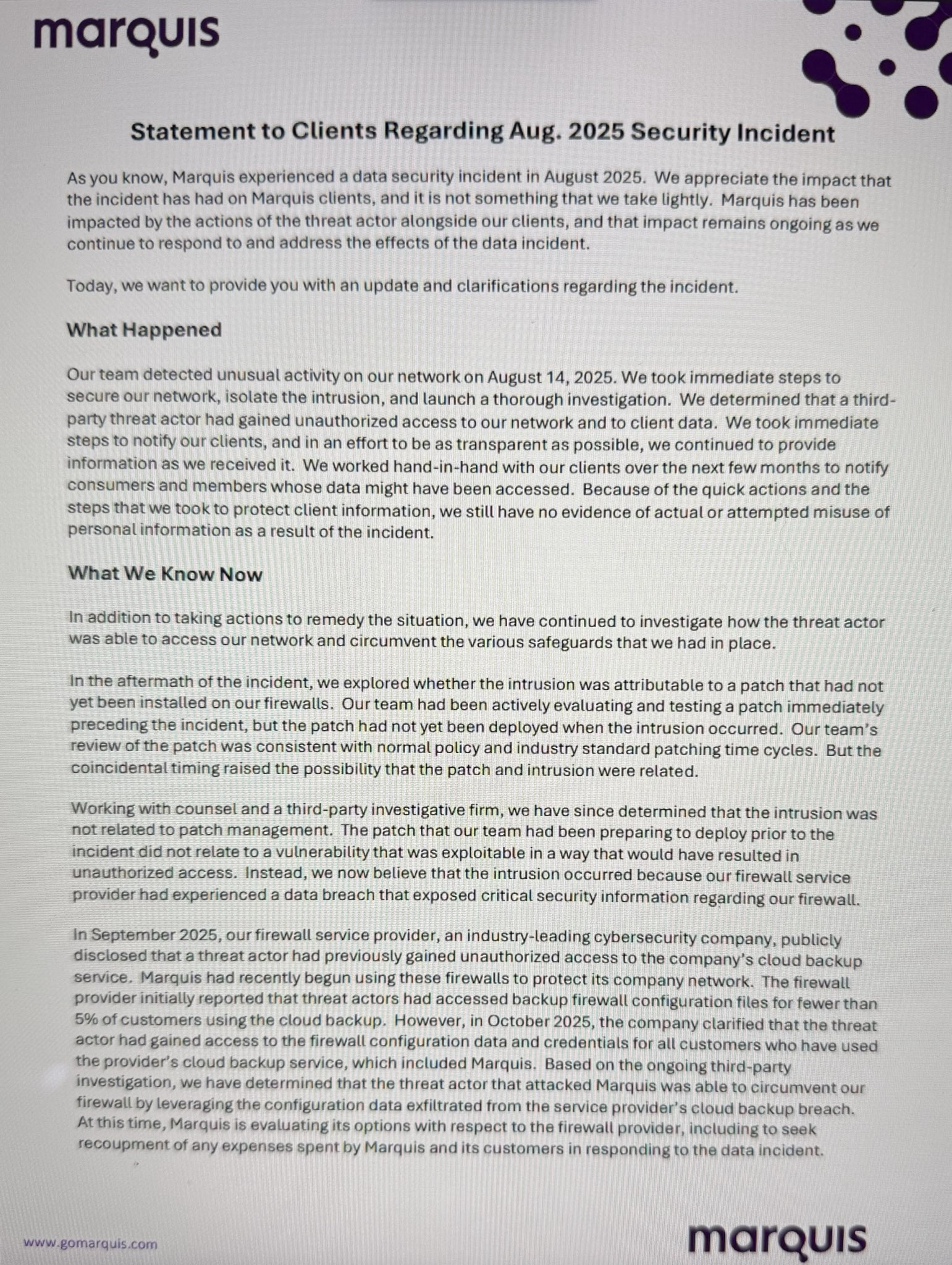
In statements to prospects earlier this week seen by BleepingComputer, Marquis says the ransomware operators did not breach its programs by exploiting an unpatched SonicWall firewall, as beforehand believed.

As an alternative, the attackers used info obtained from firewall configuration backup information stolen after gaining unauthorized entry to SonicWall’s MySonicWall on-line buyer portal.
“Primarily based on the continued third-party investigation, we now have decided that the risk actor that attacked Marquis was in a position to circumvent our firewall by leveraging the configuration knowledge extracted from the service supplier’s cloud backup breach,” Marquis stated.
“Right now, Marquis is evaluating its choices with respect to the firewall supplier, together with to hunt recoupment of any bills spent by Marquis and its prospects in responding to the info incident.”
SonicWall disclosed the security breach talked about by Marquis on September 17, when it warned prospects to reset their MySonicWall account credentials and stated the incident affected solely about 5% of its firewall prospects utilizing its cloud backup service.
The corporate additionally warned that risk actors might extract entry credentials and tokens, making it “considerably simpler” to compromise affected prospects’ firewalls. Nonetheless, roughly three weeks later, SonicWall issued an replace confirming that every one prospects utilizing its cloud backup service have been affected by the September breach.
One month later, it revealed one other replace stating {that a} Mandiant investigation into the September assault discovered proof linking the incident to state-sponsored hackers.
SonicWall added that the MySonicWall breach was unrelated to assaults by the Akira ransomware gang that focused MFA-protected SonicWall VPN accounts in late September.
Cybersecurity firm Huntress reported on October 13 that it had noticed risk actors compromising over 100 SonicWall SSLVPN accounts in a large-scale marketing campaign utilizing stolen, legitimate credentials. Nonetheless, Huntress discovered no proof linking these assaults to the SonicWall cloud backup hack, and SonicWall didn’t reply to BleepingComputer’s requests for remark on the time.
BleepingComputer reached out once more earlier this week, however a SonicWall spokesperson has but to answer.

As MCP (Mannequin Context Protocol) turns into the usual for connecting LLMs to instruments and knowledge, security groups are transferring quick to maintain these new companies secure.
This free cheat sheet outlines 7 finest practices you can begin utilizing immediately.




