A number of menace actors, each state-sponsored and financially motivated, are exploiting the CVE-2025-8088 high-severity vulnerability in WinRAR for preliminary entry and to ship numerous malicious payloads.
The security situation is a path traversal flaw that leverages Alternate Data Streams (ADS) to write down malicious recordsdata to arbitrary areas. Attackers have exploited this up to now to plant malware within the Home windows Startup folder, for persistence throughout reboots.
Researchers at cybersecurity firm ESET found the vulnerability and reported in early August 2025 that the Russia-aligned group RomCom had been exploiting it in zero-day assaults.

In a report at this time, the Google Risk Intelligence Group (GTIG) says that exploitation began as early as July 18, 2025, and continues to this present day from each state-backed espionage actors and lower-tier, financially motivated cybercriminals.
“The exploit chain usually includes concealing the malicious file throughout the ADS of a decoy file contained in the archive.
“Whereas the consumer usually views a decoy doc, comparable to a PDF, throughout the archive, there are additionally malicious ADS entries, some containing a hidden payload whereas others are dummy knowledge,” Google researchers clarify.
When opened, WinRAR extracts the ADS payload utilizing listing traversal, usually dropping LNK, HTA, BAT, CMD, or script recordsdata that execute on consumer login.
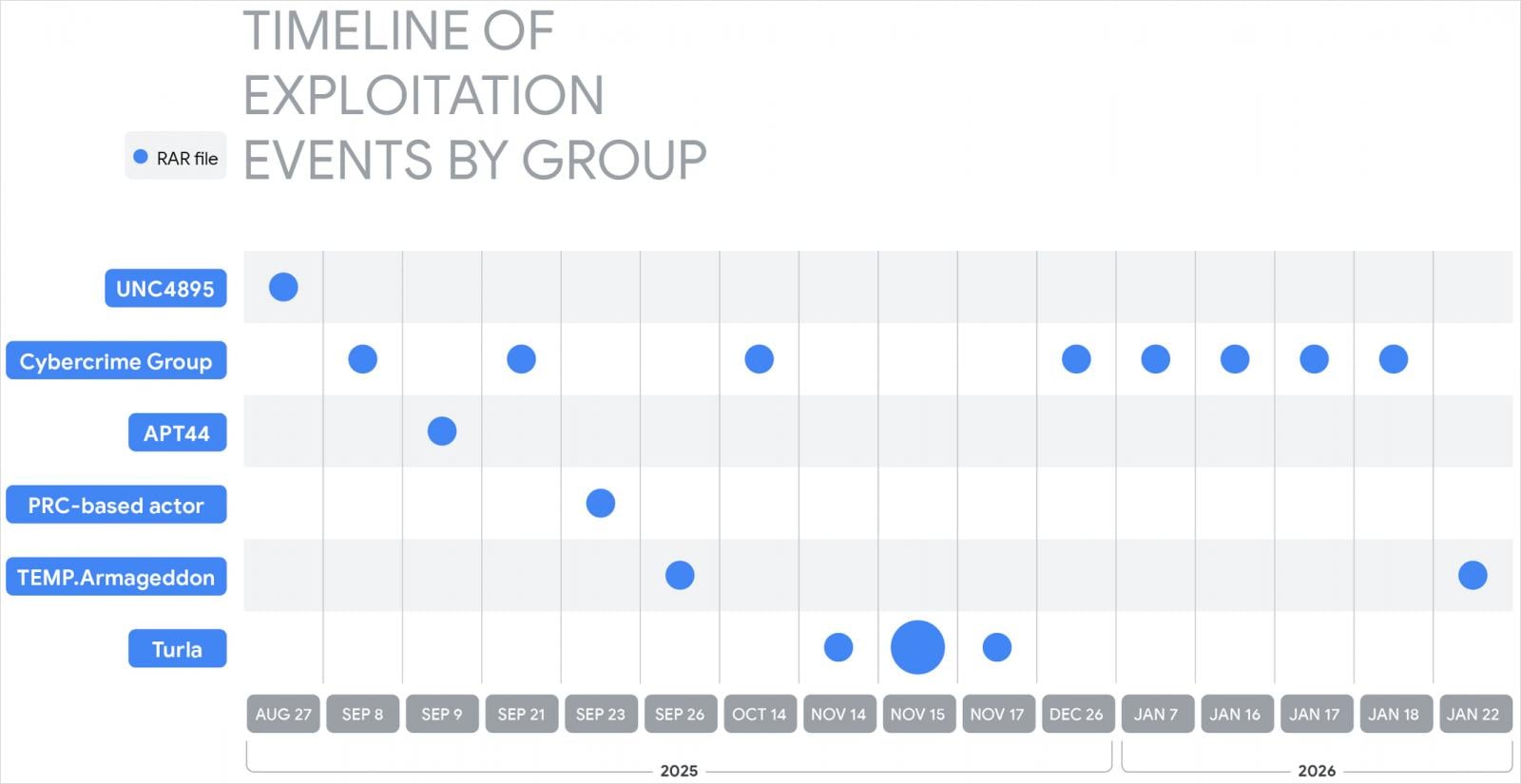
Among the many state-sponsored menace actors that Google researchers noticed exploiting CVE-2025-8088 are:
- UNC4895 (RomCom/CIGAR) delivering NESTPACKER (Snipbot) through spearphishing to Ukrainian army models.
- APT44 (FROZENBARENTS) utilizing malicious LNK recordsdata and Ukrainian-language decoys for follow-on downloads.
- TEMP.Armageddon (CARPATHIAN) dropping HTA downloaders into Startup folders (exercise ongoing into 2026).
- Turla (SUMMIT) delivering the STOCKSTAY malware suite utilizing Ukrainian military themes.
- China-linked actors utilizing the exploit to deploy POISONIVY, dropped as a BAT file that downloads further payloads.
Supply: Google
Google additionally noticed financially motivated actors exploiting the WinRAR path-traversal flaw to distribute commodity distant entry instruments and data stealers comparable to XWorm and AsyncRAT, Telegram bot-controlled backdoors, and malicious banking extensions for the Chrome browser.
All these menace actors are believed to have sourced working exploits from specialised suppliers, comparable to one utilizing the alias “zeroplayer,” who marketed a WinRAR exploit final July.
The identical menace actor has additionally marketed a number of high-value exploits final 12 months, together with alleged zero-days for Microsoft Workplace sandbox escape, company VPN RCE, Home windows native privilege escalation, and bypasses for security options (EDR, antivirus), promoting them for costs between $80,000 and $300,000.
Google feedback that this displays the commoditization of exploit improvement, which is essential within the cyberattacks lifecycle, lowering the friction and complexity for attackers and enabling them to focus on unpatched programs in a short while.

Whether or not you are cleansing up previous keys or setting guardrails for AI-generated code, this information helps your group construct securely from the beginning.
Get the cheat sheet and take the guesswork out of secrets and techniques administration.




