A critical-severity vulnerability within the vm2 Node.js sandbox library, tracked as CVE-2026-22709, permits escaping the sandbox and executing arbitrary code on the underlying host system.
The open-source vm2 library creates a safe context to permit customers to execute untrusted JavaScript code that doesn’t have entry to the filesystem.
vm2 has traditionally been seen in SaaS platforms that assist person script execution, on-line code runners, chatbots, and open-source initiatives, being utilized in greater than 200,000 initiatives on GitHub. The venture was discontinued in 2023, although, as a consequence of repeated sandbox-escape vulnerabilities, and regarded unsafe for operating untrusted code.

Final October, maintainer Patrik Šimek determined to resurrect the vm2 venture and launch model 3.10.0 that addressed all vulnerabilities identified on the time and “nonetheless suitable all the way in which again to Node 6.”
The library continues to be very fashionable on the npm platform, consistently reaching round a million downloads each week for the previous 12 months.
Improper sanitization
The most recent vulnerability arises from vm2’s failure to correctly sandbox ‘Guarantees’, the part that handles asynchronous operations to make positive code execution is restricted to the context of the remoted surroundings.
Whereas vm2 sanitizes callbacks hooked up to its personal inside Promise implementation, async features return a worldwide Promise whose .then() and.catch() callbacks aren’t correctly sanitized.
“In vm2 for model 3.10.0, Promise.prototype.then Promise.prototype.catch callback sanitization may be bypassed,” the venture maintainer says, including that “this enables attackers to flee the sandbox and run arbitrary code.”
In line with the developer, the CVE-2026-22709 sandbox escape was partially addressed in vm2 model 3.10.1, whereas within the subsequent 3.10.2 replace the developer tightened the repair to keep away from a possible bypass.
The developer additionally shared code demonstrating how CVE-2026-22709 could possibly be triggered within the vm2 sandbox to flee it and execute a command on the host system.
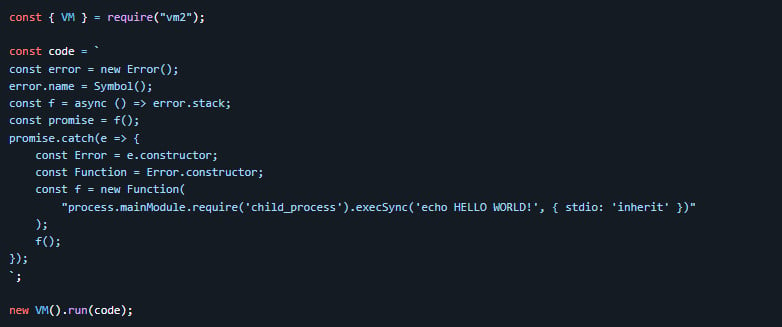
Supply: GitHub
Provided that CVE-2026-22709 is trivial to take advantage of in weak vm2 variations, customers are really helpful to improve to the most recent launch as quickly as attainable.
Beforehand reported essential sandbox escape flaws in vm2 embody CVE-2022-36067, disclosed by researchers at Oxeye. Exploiting the bug allowed escaping the remoted surroundings and operating instructions on the host system.
In April 2023, an identical flaw, tracked as CVE-2023-29017, was found, and an exploit was printed. Later that very same month, researcher SeungHyun Lee launched an exploit for CVE-2023-30547, one more essential sandbox escape impacting vm2.
Šimek advised BleepingComputer that “all disclosed vulnerabilities are correctly mounted” in vm2 model 3.10.3, at present the newest launch.

As MCP (Mannequin Context Protocol) turns into the usual for connecting LLMs to instruments and knowledge, security groups are transferring quick to maintain these new providers protected.
This free cheat sheet outlines 7 greatest practices you can begin utilizing at the moment.




