The most recent incarnation of the infamous BreachForums hacking discussion board has suffered a data breach, with its consumer database desk leaked on-line.
BreachForums is the title of a collection of hacking boards used to commerce, promote, and leak stolen knowledge, in addition to promote entry to company networks and different unlawful cybercrime providers.
The positioning was launched after the primary of those boards, RaidForums, was seized by regulation enforcement, with the proprietor, “All-powerful”, arrested.

Whereas BreachForums has suffered data breaches and police actions up to now, it has been repeatedly relaunched underneath new domains, with some accusing it of now being a honeypot for regulation enforcement.
Yesterday, an internet site named after the ShinyHunters extortion gang launched a 7Zip archive named breachedforum.7z.
This archive comprises three recordsdata named:
- shinyhunte.rs-the-story-of-james.txt
- databoose.sql
- breachedforum-pgp-key.txt.asc
A consultant of the ShinyHunters extortion gang instructed BleepingComputer they aren’t affiliated with the location that distributed this archive.
The archive’s ‘breachedforum-pgp-key.txt.asc’ file is the PGP personal key created on July 25, 2023, and utilized by BreachForums to signal official messages from the directors. Whereas the important thing has been leaked, it’s passphrase-protected, and with out the password, it could actually’t be abused to signal messages.
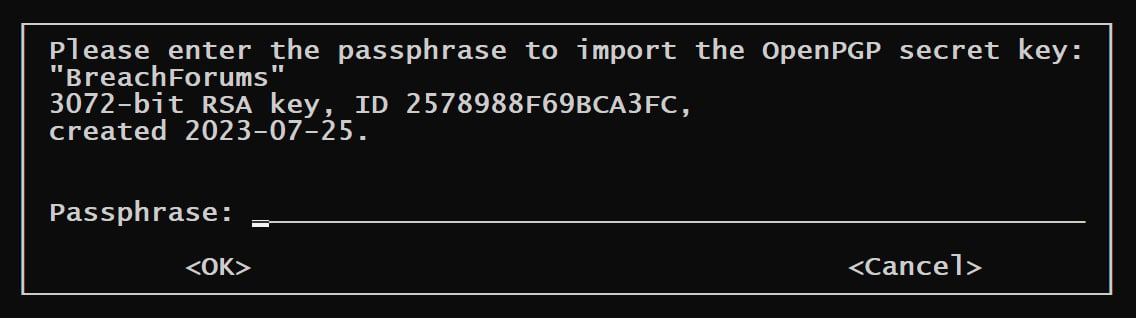
Supply: BleepingComputer
The “databoose.sql” file is a MyBB customers database desk (mybb_users) containing 323,988 member data that embrace member show names, registration dates, IP addresses, and different inside info.
BleepingComputer’s evaluation of the desk reveals that the majority of the IP addresses map again to a neighborhood loopback IP tackle (0x7F000009/127.0.0.9), so they aren’t of a lot use.
Nevertheless, 70,296 data don’t comprise the 127.0.0.9 IP tackle, and the data we examined map to a public IP tackle. These public IP addresses might be an OPSEC concern for these folks and precious to regulation enforcement and cybersecurity researchers.
The final registration date within the newly leaked consumer database is from August 11, 2025, which is similar day that the earlier BreachForums at breachforums[.]hn was closed. This shutdown adopted the arrest of a few of its alleged operators.
That very same day, a member of the ShinyHunters extortion gang posted a message on the “Scattered Lapsus$ Hunters” Telegram channel, claiming the discussion board was a law-enforcement honeypot. The BreachForums directors subsequently denied these allegations.
The breachforums[.]hn area was later seized by regulation enforcement in October 2025 after it was repurposed to extort firms impacted by the widespread Salesforce knowledge theft assaults performed by the ShinyHunters extortion group.
The present BreachForums administrator, often known as “N/A,” has acknowledged the brand new breach, stating {that a} backup of the MyBB consumer database desk was briefly uncovered in an unsecured folder and downloaded solely as soon as.
“We need to tackle latest discussions relating to an alleged database leak and clearly clarify what occurred,” N/A wrote on BreachForums.
“To start with, this isn’t a latest incident. The info in query originates from an previous users-table leak courting again to August 2025, throughout the interval when BreachForums was being restored/recovered from the .hn area.”
“In the course of the restoration course of, the customers desk and the discussion board PGP key have been briefly saved in an unsecured folder for a really brief time period. Our investigation reveals that the folder was downloaded solely as soon as throughout that window,” continued the administrator.
Whereas the administrator mentioned that BreachForums members ought to use disposable electronic mail addresses to cut back danger and that the majority IP addresses mapped to native IPs, the database nonetheless comprises info that might be of curiosity to regulation enforcement.
It is finances season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the yr forward. This report compiles their insights, permitting readers to benchmark methods, determine rising traits, and evaluate their priorities as they head into 2026.
Learn the way high leaders are turning funding into measurable affect.





