A hacker claims to have breached Condé Nast and leaked an alleged WIRED database containing greater than 2.3 million subscriber information, whereas additionally warning that they plan to launch as much as 40 million extra information for different Condé Nast properties.
On December 20, a risk actor utilizing the title “Pretty” leaked the database on a hacking discussion board, providing entry for roughly $2.30 within the website’s credit system. Within the submit, Pretty accused Condé Nast of ignoring vulnerability experiences and claimed the corporate did not take security severely.
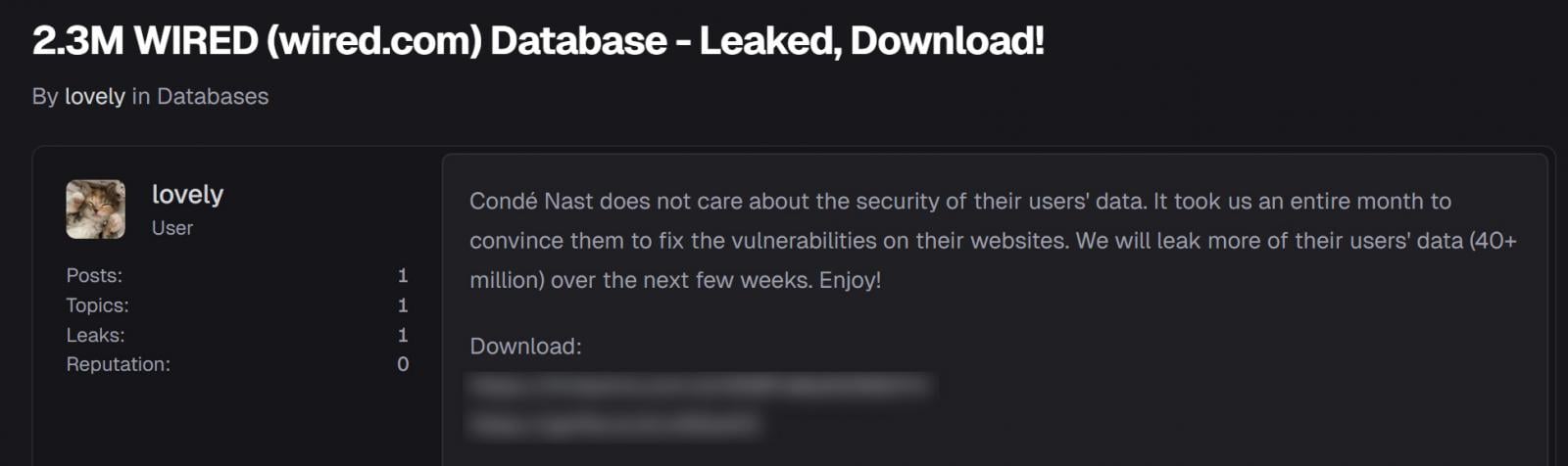
“Condé Nast doesn’t care concerning the security of their customers’ information. It took us a complete month to persuade them to repair the vulnerabilities on their web sites,” reads a submit on a hacking discussion board.

“We’ll leak extra of their customers’ information (40+ million) over the subsequent few weeks. Take pleasure in!”
Supply: BleepingComputer
The identical particular person later leaked the info on different hacking boards, the place customers additionally needed to spend discussion board credit to disclose the password to the archive containing the info.
Pretty additionally shared report counts for different Condé Nast properties they declare to have stolen information, together with, primarily based on the abbreviations used, The New Yorker, Epicurious, SELF, Vogue, Attract, Self-importance Honest, Glamour, Males’s Journal, Architectural Digest, Golf Digest, Teen Vogue, Model.com, and Condé Nast Traveler.
Whereas Condé Nast has not but confirmed it was breached, BleepingComputer analyzed the leaked database and was capable of validate twenty of the information as authentic WIRED subscribers.
The dataset accommodates 2,366,576 whole information and a pair of,366,574 distinctive electronic mail addresses, with timestamps starting from April 26, 1996, to September 9, 2025.
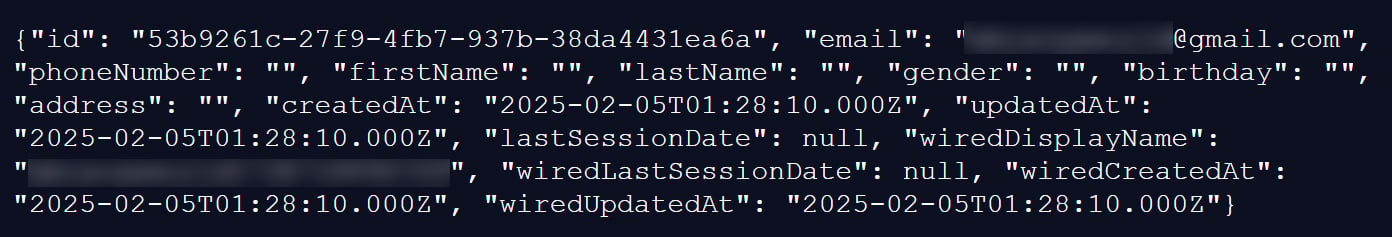
Every report features a subscriber’s distinctive inside ID, an electronic mail tackle, and non-compulsory information, comparable to first and final title, cellphone quantity, bodily tackle, gender, and birthday. Many of those fields are empty.
The information additionally embody account creation and replace timestamps, final session info, and WIRED-specific fields comparable to a show username and WIRED account creation and replace dates.
Supply: BleepingComputer
Whereas most of the information fields are empty, some embody extra private particulars.
Roughly 284,196 information (12.01%) embody each a primary and final title, 194,361 information (8.21%) embody a bodily tackle, 67,223 information (2.84%) embody a birthday, and 32,438 information (1.37%) embody a cellphone quantity.
A a lot smaller subset consists of extra full profiles, with 1,529 information (0.06%) containing a full title, birthday, cellphone quantity, tackle, and gender.
Alon Gal, co-founder and CTO of Hudson Rock, additionally verified the information utilizing infostealer logs containing beforehand compromised credentials.
“Our researchers recognized authentic subscriber credentials for wired.com inside international infostealer an infection logs,” reads an article on Infostealers.com.
“By matching these compromised credentials towards the information within the leaked database, we’ve definitively confirmed the authenticity of the dataset with none interplay with the sufferer group.”
The leaked database has since been added to Have I Been Pwned, permitting customers to examine whether or not their electronic mail addresses have been uncovered by the info leak.
Claiming to be a security researcher
Earlier than the leak, Pretty reportedly claimed to be a security researcher who contacted Dissent Doe of DataBreaches.web for assist in responsibly disclosing vulnerabilities to Condé Nast.
In keeping with DataBreaches.web, the person contacted them in late November in search of assist reaching Condé Nast’s security group relating to vulnerabilities that allegedly allowed attackers to view and modify person account info.
The particular person initially mentioned they’d downloaded solely a small variety of information to offer proof to Condé Nast, together with information verified as belonging to DataBreaches.web and a WIRED worker.
Nonetheless, after receiving no response from Condé Nast, the particular person later instructed Dissent Doe they’d downloaded the whole database and have been threatening to leak it.
Dissent Doe concluded that she had been misled and described the incident as a case the place they’d been performed by a risk actor who downloaded and leaked stolen information relatively than pursuing accountable disclosure.
“As for ‘Pretty,’ they performed me. Condé Nast ought to by no means pay them a dime, and nobody else ought to ever, as their phrase clearly can’t be trusted,” admitted DataBreaches.web.
BleepingComputer contacted Condé Nast with questions concerning the incident, however has not obtained a response presently.

Damaged IAM is not simply an IT downside – the impression ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with trendy calls for, examples of what “good” IAM seems to be like, and a easy guidelines for constructing a scalable technique.




