Gladinet has launched security updates for its CentreStack enterprise resolution to handle an area file inclusion vulnerability (CVE-2025-11371) that risk actors have leveraged as a zero-day since late September.
Researchers at cybersecurity platform Huntress disclosed the exploitation exercise final week saying that the flaw was a bypass for mitigations Gladinet applied for the deserialization vulnerability resulting in distant code execution (RCE) recognized as CVE-2025-30406.
The native file inclusion (LFI) vulnerability enabled attackers to learn the Net.config file on totally patched CentreStack deployments, extract the machine key, after which use it to take advantage of CVE-2025-30406.
When Huntress alerted of the zero-day assaults Gladinet supplied mitigations for purchasers and was within the strategy of growing a patch.
The security replace that addresses CVE-2025-11371 is now out there in CentreStack model 16.10.10408.56683 and directors are strongly advisable to put in it.
In an replace to the unique alert, Huntress shares extra technical particulars on CVE-2025-11371 that embrace a minimal proof-of-concept exploit.
The basis reason behind the LFI subject is a sanitization failure on the temp-download handler, reachable at /storage/t.dn, which accepts an ‘s=” parameter, resulting in listing traversal.
On the service runs as NT AUTHORITYSYSTEM and resolves information relative to the temp folder, the flaw permits attackers to learn any file the SYSTEM account can entry, together with Net.config, which accommodates the ASP.NET machine key.
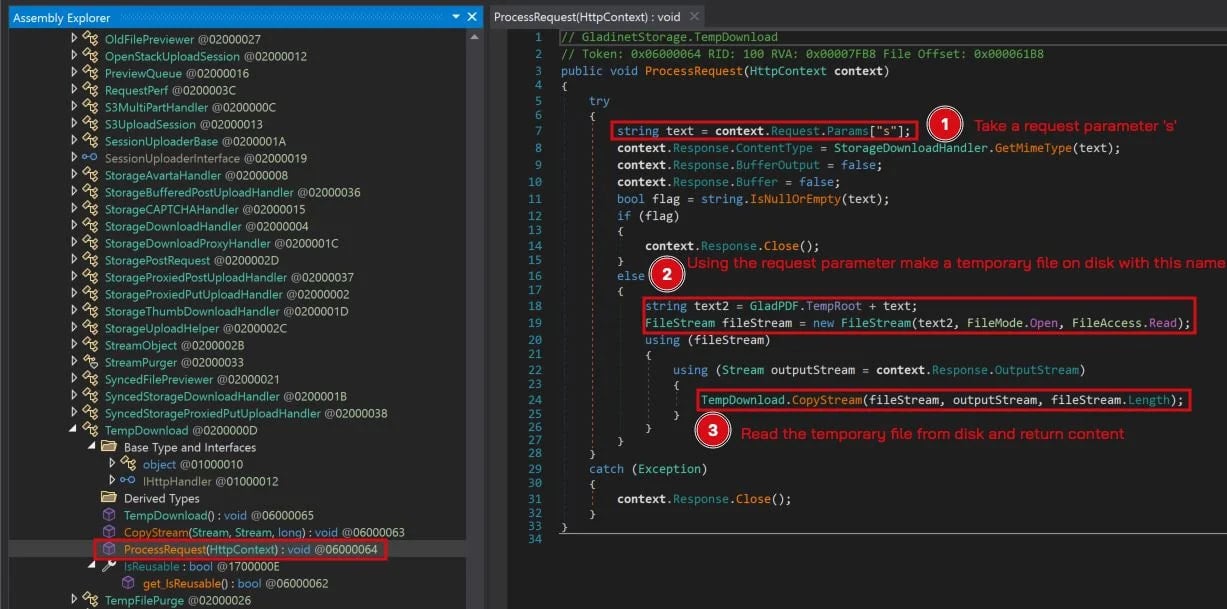
Supply: Huntress
With this key, attackers can forge a malicious ViewState payload that may be deserialized by the server as a result of CVE-2025-30406, resulting in distant code execution.
Within the wild, Huntress noticed HTTP requests to “/storage/t.dn?s=…’ returning Net.config, adopted by base64-encoded POST payloads triggering command execution on the targets.
Huntress revealed a one-line PowerShell Invoke-WebRequest instance exhibiting how an unauthenticated request to’/storage/t.dn?s=…’ can be utilized to retrieve Net.config.
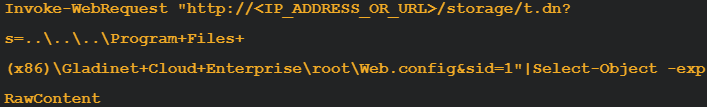
Supply: Huntress
Nevertheless, the researchers didn’t launch the total exploit chain together with the sooner deserialization RCE (CVE-2025-30406).
Doubtlessly impacted customers are advisable to improve to CentreStack model 16.10.10408.56683.
If putting in the brand new model just isn’t attainable, a mitigation is to disable the temp handler within the Net.config file for the UploadDownloadProxy element by eradicating the road that defines it within the file.

Be part of the Breach and Attack Simulation Summit and expertise the way forward for security validation. Hear from prime specialists and see how AI-powered BAS is remodeling breach and assault simulation.
Do not miss the occasion that can form the way forward for your security technique




