A spike in suspicious scans focusing on Palo Alto Networks login portals signifies clear reconnaissance efforts from suspicious IP addresses, researchers warn.
Cybersecurity intelligence firm GreyNoise experiences a 500% enhance in IP addresses targeted on Palo Alto Networks GlobalProtect and PAN-OS profiles.
The exercise culminated on October 3 with greater than 1,285 distinctive IPs engaged within the exercise. Usually, each day scans don’t exceed 200 addresses, the corporate says.
Many of the noticed IPs have been geolocated within the U.S., whereas smaller clusters have been primarily based within the U.Okay., the Netherlands, Canada, and Russia.
One exercise cluster concentrated its site visitors on targets in the US and one other one targeted on Pakistan, the researchers say, noting that each had “distinct TLS fingerprints however not with out overlap.”
In keeping with GreyNoise, 91% of the IP addresses have been categorized as suspicious. A further 7% have been tagged as malicious.
“Almost all exercise was directed at GreyNoise’s emulated Palo Alto profiles (Palo Alto GlobalProtect, Palo Alto PAN-OS), suggesting the exercise is focused in nature, doubtless derived from public (e.g., Shodan, Censys) or attacker-originated scans fingerprinting Palo Alto gadgets,” explains GreyNoise.
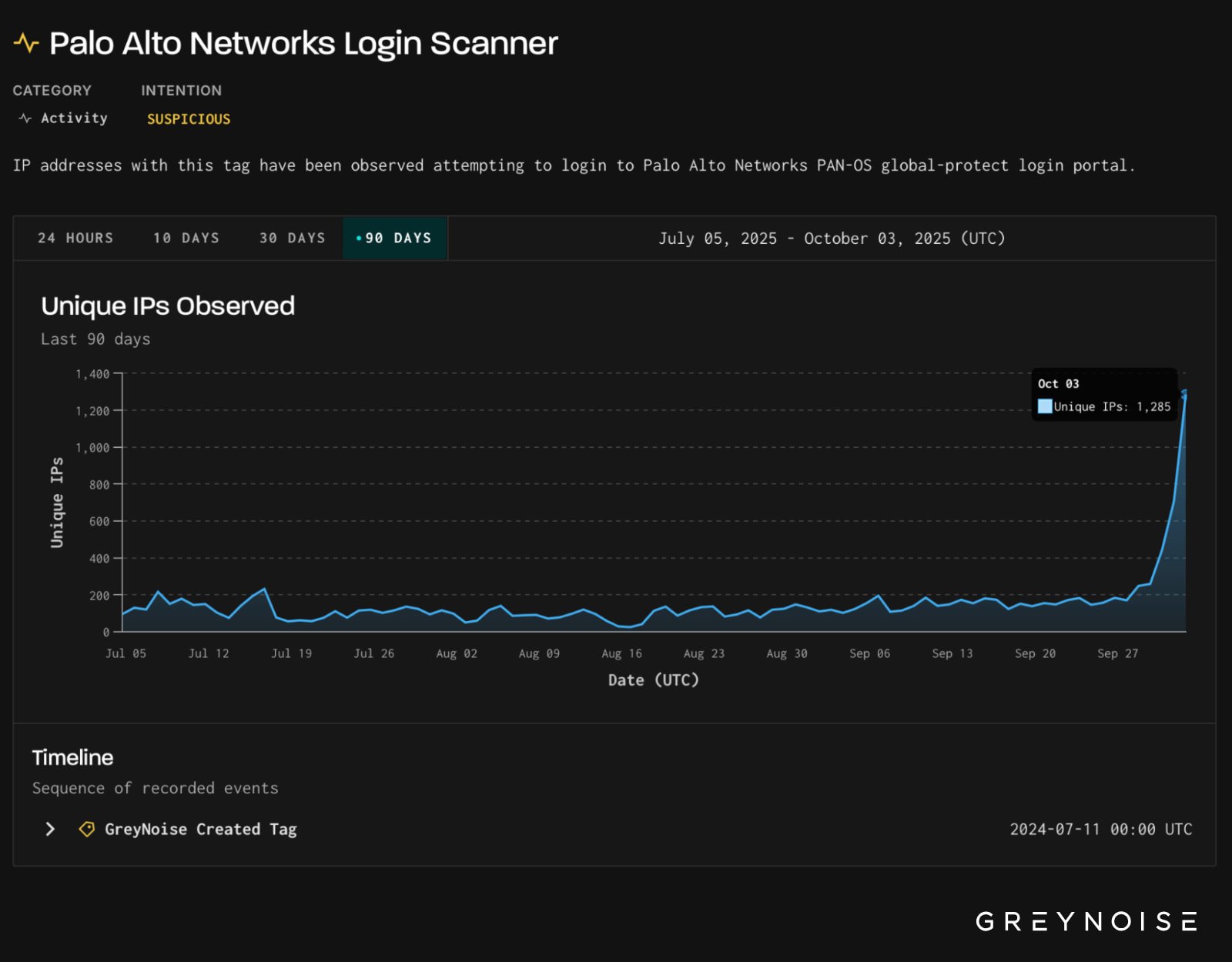
Supply: GreyNoise
GreyNoise has beforehand warned that such scan exercise typically signifies preparation for assaults utilizing new exploits for zero-day or n-day flaws.
The cybersecurity agency issued a warning lately about elevated community scans focusing on Cisco ASA gadgets. Two weeks later, information emerged a couple of zero-day vulnerability exploited in assaults focusing on the identical Cisco product.
Nevertheless, GreyNoise says the noticed correlation is weaker for the current scans specializing in Palo Alto Networks merchandise.
Grafana additionally focused
Researchers additionally observed a rise in exploitation makes an attempt of an previous path traversal vulnerability in Grafana. The security situation is recognized as CVE-2021-43798 and was exploited in December 2021 in zero-day assaults.
GreyNoise noticed 110 distinctive malicious IPs, most of them from Bangladesh, launching assaults on September 28.
The targets have been based totally in the US, Slovakia, and Taiwan, with the assaults sustaining a constant vacation spot ratio relying on the particular origin, which usually signifies automation.
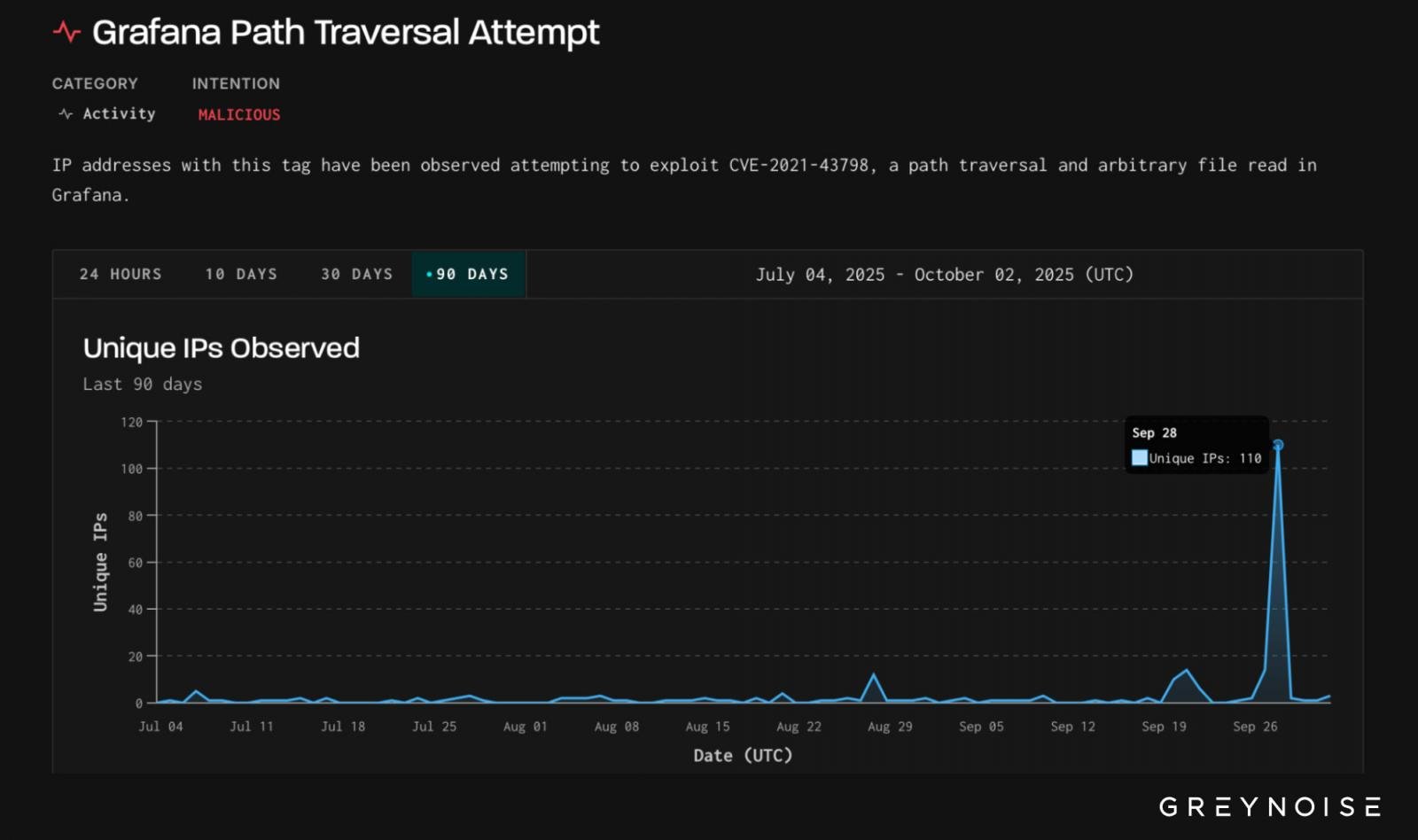
Supply: GreyNoise
Greynoise recommends directors to be sure that their Grafana cases are patched in opposition to CVE-2021-43798 and block the recognized 110 malicious IP addresses.
The researchers additionally advise checking the logs for proof of path traversal requests that will return delicate information.

Be part of the Breach and Attack Simulation Summit and expertise the way forward for security validation. Hear from high consultants and see how AI-powered BAS is remodeling breach and assault simulation.
Do not miss the occasion that can form the way forward for your security technique




